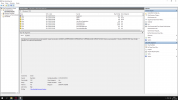
KMODE_EXCEPTION_NOT_HANDLED (1e)
This is a very common bugcheck. Usually the exception address pinpoints
the driver/function that caused the problem. Always note this address
as well as the link date of the driver/image that contains this address.
Arguments:
Arg1: ffffffffc0000005, The exception code that was not handled
Arg2: fffff804285fc4d7, The address that the exception occurred at
Arg3: fffff98d62c6e398, Parameter 0 of the exception
Arg4: ffff8d017effc920, Parameter 1 of the exception
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 7343
Key : Analysis.DebugAnalysisProvider.CPP
Value: Create: 8007007e on BORA
Key : Analysis.DebugData
Value: CreateObject
Key : Analysis.DebugModel
Value: CreateObject
Key : Analysis.Elapsed.mSec
Value: 17159
Key : Analysis.Memory.CommitPeak.Mb
Value: 87
Key : Analysis.System
Value: CreateObject
Key : WER.OS.Branch
Value: vb_release
Key : WER.OS.Timestamp
Value: 2019-12-06T14:06:00Z
Key : WER.OS.Version
Value: 10.0.19041.1
ADDITIONAL_XML: 1
OS_BUILD_LAYERS: 1
BUGCHECK_CODE: 1e
BUGCHECK_P1: ffffffffc0000005
BUGCHECK_P2: fffff804285fc4d7
BUGCHECK_P3: fffff98d62c6e398
BUGCHECK_P4: ffff8d017effc920
WRITE_ADDRESS: fffff80428efb390: Unable to get MiVisibleState
Unable to get NonPagedPoolStart
Unable to get NonPagedPoolEnd
Unable to get PagedPoolStart
Unable to get PagedPoolEnd
fffff80428e0f340: Unable to get Flags value from nt!KdVersionBlock
fffff80428e0f340: Unable to get Flags value from nt!KdVersionBlock
unable to get nt!MmSpecialPagesInUse
ffff8d017effc920
EXCEPTION_PARAMETER1: fffff98d62c6e398
EXCEPTION_PARAMETER2: ffff8d017effc920
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: obs64.exe
BAD_STACK_POINTER: ffff8d017effc0a8
STACK_TEXT:
ffff8d01`7effc0a8 fffff804`2870e6bf : 00000000`0000001e ffffffff`c0000005 fffff804`285fc4d7 fffff98d`62c6e398 : nt!KeBugCheckEx
ffff8d01`7effc0b0 fffff804`2860d066 : ffff8d01`7effc920 fffff804`2848db25 fffff98d`62c6e5d0 fffff804`285fc4d7 : nt!KiFatalFilter+0x1f
ffff8d01`7effc0f0 fffff804`285cb25f : fffff804`00000002 fffff804`282c9aa4 fffff98d`62c69000 fffff98d`62c70000 : nt!KeExpandKernelStackAndCalloutInternal$filt$0+0x16
ffff8d01`7effc130 fffff804`285fd45f : fffff804`282c9aa4 ffff8d01`7effc710 fffff804`285cb1c0 00000000`00000000 : nt!_C_specific_handler+0x9f
ffff8d01`7effc1a0 fffff804`28452d97 : ffff8d01`7effc710 00000000`00000000 fffff98d`62c6f1a0 fffff804`2840d468 : nt!RtlpExecuteHandlerForException+0xf
ffff8d01`7effc1d0 fffff804`284519a6 : fffff98d`62c6e398 ffff8d01`7effce20 fffff98d`62c6e398 ffffcb05`fe7bde80 : nt!RtlDispatchException+0x297
ffff8d01`7effc8f0 fffff804`285f5432 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiDispatchException+0x186
ffff8d01`7effcfb0 fffff804`285f5400 : fffff804`286066a5 00000000`00000000 fffff804`00000004 ffffcb05`feb43a01 : nt!KxExceptionDispatchOnExceptionStack+0x12
fffff98d`62c6e258 fffff804`286066a5 : 00000000`00000000 fffff804`00000004 ffffcb05`feb43a01 00000000`00000000 : nt!KiExceptionDispatchOnExceptionStackContinue
fffff98d`62c6e260 fffff804`286023e0 : fffff804`2b6c1000 ffffcb05`feb43a40 ffffcb05`00000000 fffff804`2b144f90 : nt!KiExceptionDispatch+0x125
fffff98d`62c6e440 fffff804`285fc4d7 : ffffcb05`f8a56b40 fffff804`7eaf6d7c 00000000`00020001 00000000`00000000 : nt!KiGeneralProtectionFault+0x320
fffff98d`62c6e5d0 fffff804`7eaf6d7c : 00000000`00020001 00000000`00000000 00000000`00000000 00000000`00000000 : nt!ExpInterlockedPopEntrySListFault
fffff98d`62c6e5e0 fffff804`7eaf44fc : ffffcb05`fda0ec20 ffffcb05`fe7bde80 fffff98d`62c6e8a0 ffffcb05`fcd0c000 : Ndu!PplGenericAllocateFunction+0x1c
fffff98d`62c6e620 fffff804`2b2c8c5f : 00000000`00000000 fffff98d`62c6e729 ffffcb05`00000004 fffff98d`62c6e9f0 : Ndu!NduOutboundTransportClassify+0x38c
fffff98d`62c6e6c0 fffff804`2b383ffb : ffffcb05`f5d318a8 00000000`00000000 ffffcb05`fa59dcd0 ffffcb05`fa59dcd0 : NETIO!KfdClassify2+0x19f
fffff98d`62c6e790 fffff804`2b38322b : ffffcb05`f5d31988 00000000`007eca8b 00000000`00000000 ffffcb05`f5d318a8 : tcpip!IppInspectLocalDatagramsOut+0x6cb
fffff98d`62c6ea60 fffff804`2b381d99 : 00000000`00000000 00000000`00000000 fffff804`2b548230 ffffcb05`fa59dcd0 : tcpip!IppSendDatagramsCommon+0x41b
fffff98d`62c6ebe0 fffff804`2b3a4507 : ffffcb05`fe2fd380 00000000`00000014 00000000`00000000 ffffcb05`fa59dcd0 : tcpip!IpNlpFastSendDatagram+0x349
fffff98d`62c6eca0 fffff804`2b3a2854 : ffffcb05`f5e1e7e8 fffff98d`62c6f310 fffff98d`62c6f120 00000000`00000000 : tcpip!TcpTcbSend+0x1737
fffff98d`62c6f020 fffff804`2b3a24be : 00000000`00000000 00000000`00000000 fffff98d`62c6f280 fffff804`2b3a2490 : tcpip!TcpEnqueueTcbSend+0x374
fffff98d`62c6f160 fffff804`2840d468 : ffffcb05`fa4fca01 00000000`00000000 ffffcb05`00000000 00000000`00000001 : tcpip!TcpTlConnectionSendCalloutRoutine+0x2e
fffff98d`62c6f1a0 fffff804`2840d3dd : fffff804`2b3a2490 fffff98d`62c6f280 ffffcb05`ffee7208 ffffcb05`fd5dbb60 : nt!KeExpandKernelStackAndCalloutInternal+0x78
fffff98d`62c6f210 fffff804`2b3c1d00 : 00000000`00000000 00000000`00000000 ffffcb05`ee4ce400 fffff804`3ea4df40 : nt!KeExpandKernelStackAndCalloutEx+0x1d
fffff98d`62c6f250 fffff804`3ea4c0d0 : ffffcb05`ffee7208 ffffcb05`fa4fcaf0 00000000`00001001 ffffcb05`ffee7208 : tcpip!TcpTlConnectionSend+0x80
fffff98d`62c6f2c0 fffff804`3ea4befa : ffffcb05`fa4fcaf0 fffff98d`62c6fa80 ffffcb05`f9198060 ffffcb05`ffee7000 : afd!AfdTLStartBufferedVcSend+0xa0
fffff98d`62c6f370 fffff804`3ea31720 : ffffcb05`ffee7208 00000000`00000000 00000000`00001001 fffff98d`62c6f868 : afd!AfdFastConnectionSend+0x2a2
fffff98d`62c6f440 fffff804`288c1b92 : 00000000`00000000 00000000`0001201f fffff98d`62c6fa80 ffffcb05`fd28d3b0 : afd!AfdFastIoDeviceControl+0xf90
fffff98d`62c6f7e0 fffff804`288c17f6 : 00000000`00000001 00000000`00008390 00000000`00000000 00000000`00000000 : nt!IopXxxControlFile+0x382
fffff98d`62c6f920 fffff804`28605fb5 : 00000000`00000000 00000000`00000000 00000000`00000102 ffffcb05`fd31bb60 : nt!NtDeviceIoControlFile+0x56
fffff98d`62c6f990 00007ffc`eb30be74 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x25
000000ae`1f47b428 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x00007ffc`eb30be74
SYMBOL_NAME: Ndu!PplGenericAllocateFunction+1c
MODULE_NAME: Ndu
IMAGE_NAME: Ndu.sys
IMAGE_VERSION: 10.0.19041.1030
STACK_COMMAND: .thread ; .cxr ; kb
BUCKET_ID_FUNC_OFFSET: 1c
FAILURE_BUCKET_ID: 0x1E_c0000005_STACKPTR_ERROR_Ndu!PplGenericAllocateFunction
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: vb_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {040fbfea-4e33-dce2-4a10-b9c4b0dd9e1c}
Followup: MachineOwner
---------
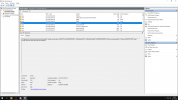
KMODE_EXCEPTION_NOT_HANDLED (1e)
This is a very common bugcheck. Usually the exception address pinpoints
the driver/function that caused the problem. Always note this address
as well as the link date of the driver/image that contains this address.
Arguments:
Arg1: ffffffffc0000005, The exception code that was not handled
Arg2: fffff8022e5fc4d7, The address that the exception occurred at
Arg3: 0000000000000000, Parameter 0 of the exception
Arg4: ffffffffffffffff, Parameter 1 of the exception
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 4421
Key : Analysis.DebugAnalysisProvider.CPP
Value: Create: 8007007e on BORA
Key : Analysis.DebugData
Value: CreateObject
Key : Analysis.DebugModel
Value: CreateObject
Key : Analysis.Elapsed.mSec
Value: 4441
Key : Analysis.Memory.CommitPeak.Mb
Value: 75
Key : Analysis.System
Value: CreateObject
Key : WER.OS.Branch
Value: vb_release
Key : WER.OS.Timestamp
Value: 2019-12-06T14:06:00Z
Key : WER.OS.Version
Value: 10.0.19041.1
ADDITIONAL_XML: 1
OS_BUILD_LAYERS: 1
BUGCHECK_CODE: 1e
BUGCHECK_P1: ffffffffc0000005
BUGCHECK_P2: fffff8022e5fc4d7
BUGCHECK_P3: 0
BUGCHECK_P4: ffffffffffffffff
READ_ADDRESS: fffff8022eefb390: Unable to get MiVisibleState
Unable to get NonPagedPoolStart
Unable to get NonPagedPoolEnd
Unable to get PagedPoolStart
Unable to get PagedPoolEnd
fffff8022ee0f340: Unable to get Flags value from nt!KdVersionBlock
fffff8022ee0f340: Unable to get Flags value from nt!KdVersionBlock
unable to get nt!MmSpecialPagesInUse
ffffffffffffffff
EXCEPTION_PARAMETER2: ffffffffffffffff
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: ModernWarfare.exe
TRAP_FRAME: cccccccccccccccc -- (.trap 0xcccccccccccccccc)
Unable to read trap frame at cccccccc`cccccccc
BAD_STACK_POINTER: ffffda00ef0bd158
STACK_TEXT:
ffffda00`ef0bd158 fffff802`2e6f465e : 00000000`0000001e ffffffff`c0000005 fffff802`2e5fc4d7 00000000`00000000 : nt!KeBugCheckEx
ffffda00`ef0bd160 fffff802`2e5fd45f : fffff802`2e6f463c 00000000`00000000 00000000`00000000 00000000`00000000 : nt!HvlpVtlCallExceptionHandler+0x22
ffffda00`ef0bd1a0 fffff802`2e452d97 : ffffda00`ef0bd710 00000000`00000000 ffffd68a`ae647fb0 fffff802`2e5fb5e5 : nt!RtlpExecuteHandlerForException+0xf
ffffda00`ef0bd1d0 fffff802`2e4519a6 : ffffd68a`ae6470f8 ffffda00`ef0bde20 ffffd68a`ae6470f8 ffffa406`fef68580 : nt!RtlDispatchException+0x297
ffffda00`ef0bd8f0 fffff802`2e5f5432 : 5e415f41`000004e0 c35b5e5f`5c415d41 cccccccc`cccccccc 9d058b48`68ec8348 : nt!KiDispatchException+0x186
ffffda00`ef0bdfb0 fffff802`2e5f5400 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KxExceptionDispatchOnExceptionStack+0x12
ffffd68a`ae646fb8 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiExceptionDispatchOnExceptionStackContinue
SYMBOL_NAME: nt!HvlpVtlCallExceptionHandler+22
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
IMAGE_VERSION: 10.0.19041.572
STACK_COMMAND: .thread ; .cxr ; kb
BUCKET_ID_FUNC_OFFSET: 22
FAILURE_BUCKET_ID: 0x1E_c0000005_R_STACKPTR_ERROR_nt!HvlpVtlCallExceptionHandler
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: vb_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {c4bb52a5-c6c0-a69d-d04f-6665c2332629}
Followup: MachineOwner
---------