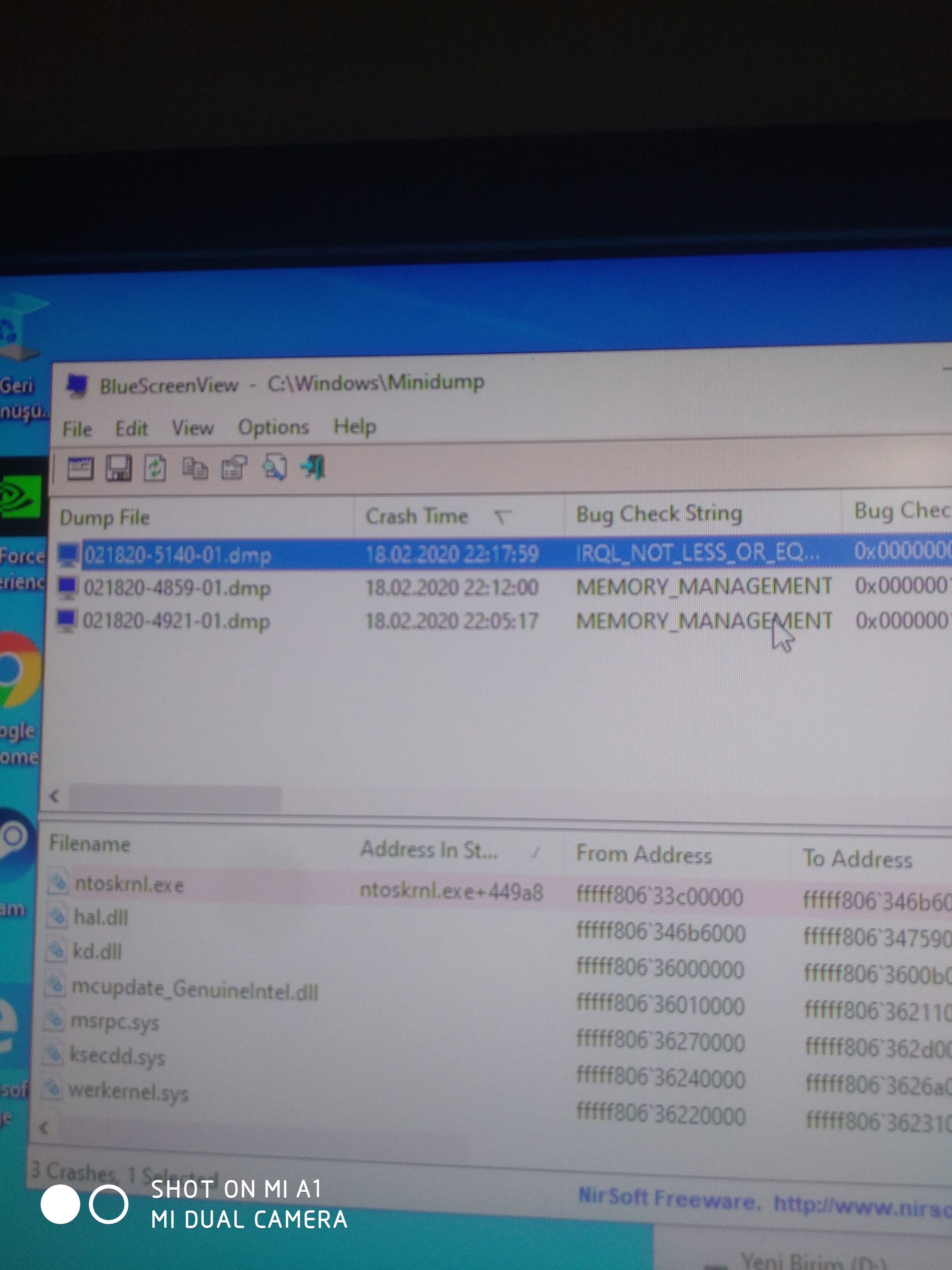
IRQL_NOT_LESS_OR_EQUAL (a)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If a kernel debugger is available get the stack backtrace.
Arguments:
Arg1: 0000000200000010, memory referenced
Arg2: 0000000000000002, IRQL
Arg3: 0000000000000000, bitfield :
bit 0 : value 0 = read operation, 1 = write operation
bit 3 : value 0 = not an execute operation, 1 = execute operation (only on chips which support this level of status)
Arg4: fffff80633c449a8, address which referenced memory
Debugging Details:
------------------
KEY_VALUES_STRING: 1
PROCESSES_ANALYSIS: 1
SERVICE_ANALYSIS: 1
STACKHASH_ANALYSIS: 1
TIMELINE_ANALYSIS: 1
DUMP_CLASS: 1
DUMP_QUALIFIER: 400
BUILD_VERSION_STRING: 18362.1.amd64fre.19h1_release.190318-1202
DUMP_TYPE: 2
BUGCHECK_P1: 200000010
BUGCHECK_P2: 2
BUGCHECK_P3: 0
BUGCHECK_P4: fffff80633c449a8
READ_ADDRESS: fffff806341733b8: Unable to get MiVisibleState
Unable to get NonPagedPoolStart
Unable to get NonPagedPoolEnd
Unable to get PagedPoolStart
Unable to get PagedPoolEnd
0000000200000010
CURRENT_IRQL: 2
FAULTING_IP:
nt!RtlRbRemoveNode+368
fffff806`33c449a8 498b4310 mov rax,qword ptr [r11+10h]
CPU_COUNT: 4
CPU_MHZ: d40
CPU_VENDOR: GenuineIntel
CPU_FAMILY: 6
CPU_MODEL: 3c
CPU_STEPPING: 3
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: WIN8_DRIVER_FAULT
BUGCHECK_STR: AV
PROCESS_NAME: lsass.exe
ANALYSIS_SESSION_HOST: DESKTOP-18V31A3
ANALYSIS_SESSION_TIME: 02-19-2020 21:47:51.0856
ANALYSIS_VERSION: 10.0.18362.1 x86fre
IRP_ADDRESS: ffffdf8f7a6b34a8
TRAP_FRAME: ffffb28cff328160 -- (.trap 0xffffb28cff328160)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=0000000000000000 rbx=0000000000000000 rcx=0000000200000000
rdx=ffffdf8f7c133e88 rsi=0000000000000000 rdi=0000000000000000
rip=fffff80633c449a8 rsp=ffffb28cff3282f8 rbp=0000000000000100
r8=0000000200000000 r9=0000000000000001 r10=ffffdf8f79d71fe8
r11=0000000200000000 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl nz na po nc
nt!RtlRbRemoveNode+0x368:
fffff806`33c449a8 498b4310 mov rax,qword ptr [r11+10h] ds:00000002`00000010=????????????????
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff80633dd33e9 to fffff80633dc1510
STACK_TEXT:
ffffb28c`ff328018 fffff806`33dd33e9 : 00000000`0000000a 00000002`00000010 00000000`00000002 00000000`00000000 : nt!KeBugCheckEx
ffffb28c`ff328020 fffff806`33dcf72b : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`0000000c : nt!KiBugCheckDispatch+0x69
ffffb28c`ff328160 fffff806`33c449a8 : 000000ea`00180000 00010016`00ea0001 fffff806`33c44493 00000000`00000100 : nt!KiPageFault+0x46b
ffffb28c`ff3282f8 fffff806`33c44493 : 00000000`00000100 ffffdf8f`7c132e80 00000000`00000000 ffffdf8f`7c133e80 : nt!RtlRbRemoveNode+0x368
ffffb28c`ff328310 fffff806`33c43e7a : ffffdf8f`74e02280 ffffdf8f`0000000f 00000000`00000ffe ffffb28c`ff328420 : nt!RtlpHpVsChunkCoalesce+0x183
ffffb28c`ff328380 fffff806`33c460ed : ffffdf8f`00000ffd 00000000`00000000 ffffdf8f`75af8220 00000000`00000000 : nt!RtlpHpVsContextFree+0x18a
ffffb28c`ff328420 fffff806`33f6f0a9 : fffff806`366d3105 fffff806`00000e90 00000000`00000000 01000000`00100000 : nt!ExFreeHeapPool+0x56d
ffffb28c`ff328540 fffff806`33c4650e : ffffdf8f`7c140040 fffff806`366668ab ffffdf8f`7c0cba10 00000000`00000068 : nt!ExFreePool+0x9
ffffb28c`ff328570 fffff806`33c47e1c : ffffdf8f`7a6b3520 ffffb28c`ff3287c0 ffffdf8f`74e02201 ffffb28c`ff32878c : nt!IopCompleteRequest+0x8e
ffffb28c`ff328660 fffff806`33c476a7 : ffffdf8f`7c140040 00000000`00000000 00000000`00000dd8 ffffdf8f`7c140040 : nt!IopfCompleteRequest+0x75c
ffffb28c`ff328770 fffff806`3625bb47 : ffffdf8f`7a6b3510 00000000`00000068 ffffdf8f`7956f1c0 ffffdf8f`79d0e340 : nt!IofCompleteRequest+0x17
ffffb28c`ff3287a0 fffff806`33c31f79 : ffffdf8f`7a6b3510 00000000`00000dd8 00000000`00000001 ffffdf8f`7a6b3628 : ksecdd!KsecDispatch+0x137
ffffb28c`ff328820 fffff806`341e9785 : ffffb28c`ff328b80 ffffdf8f`7a6b3510 00000000`00000001 ffffdf8f`7955e850 : nt!IofCallDriver+0x59
ffffb28c`ff328860 fffff806`341e9590 : 00000000`00000000 ffffb28c`ff328b80 ffffdf8f`7a6b3510 ffffb28c`ff328b80 : nt!IopSynchronousServiceTail+0x1a5
ffffb28c`ff328900 fffff806`341e8966 : 00007ff9`e9fe636e 00000000`00000000 00000000`00000000 00000000`00000000 : nt!IopXxxControlFile+0xc10
ffffb28c`ff328a20 fffff806`33dd2e18 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!NtDeviceIoControlFile+0x56
ffffb28c`ff328a90 00007ff9`ee4fc1a4 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x28
00000056`c787d8f8 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x00007ff9`ee4fc1a4
THREAD_SHA1_HASH_MOD_FUNC: 63de393ae86abe90047ec5700acf657a93f0b8dc
THREAD_SHA1_HASH_MOD_FUNC_OFFSET: e1503c6861af88abbacaf29c463f80106702da95
THREAD_SHA1_HASH_MOD: 43c20223fcb72681e5d7ce348b2470ef8d9091f2
FOLLOWUP_IP:
nt!ExFreePool+9
fffff806`33f6f0a9 4883c428 add rsp,28h
FAULT_INSTR_CODE: 28c48348
SYMBOL_STACK_INDEX: 7
SYMBOL_NAME: nt!ExFreePool+9
FOLLOWUP_NAME: Pool_corruption
IMAGE_NAME: Pool_Corruption
DEBUG_FLR_IMAGE_TIMESTAMP: 0
IMAGE_VERSION: 10.0.18362.657
MODULE_NAME: Pool_Corruption
STACK_COMMAND: .thread ; .cxr ; kb
BUCKET_ID_FUNC_OFFSET: 9
FAILURE_BUCKET_ID: AV_nt!ExFreePool
BUCKET_ID: AV_nt!ExFreePool
PRIMARY_PROBLEM_CLASS: AV_nt!ExFreePool
TARGET_TIME: 2020-02-18T19:17:59.000Z
OSBUILD: 18362
OSSERVICEPACK: 657
SERVICEPACK_NUMBER: 0
OS_REVISION: 0
SUITE_MASK: 272
PRODUCT_TYPE: 1
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
OSEDITION: Windows 10 WinNt TerminalServer SingleUserTS
OS_LOCALE:
USER_LCID: 0
OSBUILD_TIMESTAMP: 2005-04-23 04:40:32
BUILDDATESTAMP_STR: 190318-1202
BUILDLAB_STR: 19h1_release
BUILDOSVER_STR: 10.0.18362.1.amd64fre.19h1_release.190318-1202
ANALYSIS_SESSION_ELAPSED_TIME: 2ff9
ANALYSIS_SOURCE: KM
FAILURE_ID_HASH_STRING: km:av_nt!exfreepool
FAILURE_ID_HASH: {2ae0a97e-dcd7-47ef-dbfb-430f2cbf58a1}
Followup: Pool_corruption
---------
MEMORY_MANAGEMENT (1a)
# Any other values for parameter 1 must be individually examined.
Arguments:
Arg1: 0000000000041792, A corrupt PTE has been detected. Parameter 2 contains the address of
the PTE. Parameters 3/4 contain the low/high parts of the PTE.
Arg2: ffff88bffc92c488
Arg3: 0000000200000000
Arg4: 0000000000000000
Debugging Details:
------------------
***** Debugger could not find nt in module list, module list might be corrupt, error 0x80070057.
KEY_VALUES_STRING: 1
PROCESSES_ANALYSIS: 1
SERVICE_ANALYSIS: 1
STACKHASH_ANALYSIS: 1
TIMELINE_ANALYSIS: 1
DUMP_CLASS: 1
DUMP_QUALIFIER: 400
DUMP_TYPE: 2
BUGCHECK_P1: 41792
BUGCHECK_P2: ffff88bffc92c488
BUGCHECK_P3: 200000000
BUGCHECK_P4: 0
MEMORY_CORRUPTOR: ONE_BIT
BUGCHECK_STR: 0x1a_41792
CPU_COUNT: 4
CPU_MHZ: d40
CPU_VENDOR: GenuineIntel
CPU_FAMILY: 6
CPU_MODEL: 3c
CPU_STEPPING: 3
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: WIN8_DRIVER_FAULT
CURRENT_IRQL: 0
ANALYSIS_SESSION_HOST: DESKTOP-18V31A3
ANALYSIS_SESSION_TIME: 02-19-2020 21:47:54.0314
ANALYSIS_VERSION: 10.0.18362.1 x86fre
STACK_TEXT:
ffff8100`fe54eb68 fffff807`4fe253ee : 00000000`0000001a 00000000`00041792 ffff88bf`fc92c488 00000002`00000000 : 0xfffff807`4fdc1510
ffff8100`fe54eb70 00000000`0000001a : 00000000`00041792 ffff88bf`fc92c488 00000002`00000000 00000000`00000000 : 0xfffff807`4fe253ee
ffff8100`fe54eb78 00000000`00041792 : ffff88bf`fc92c488 00000002`00000000 00000000`00000000 fffff807`00000000 : 0x1a
ffff8100`fe54eb80 ffff88bf`fc92c488 : 00000002`00000000 00000000`00000000 fffff807`00000000 ffffbd0a`67bdc880 : 0x41792
ffff8100`fe54eb88 00000002`00000000 : 00000000`00000000 fffff807`00000000 ffffbd0a`67bdc880 ffff8100`fe54f180 : 0xffff88bf`fc92c488
ffff8100`fe54eb90 00000000`00000000 : fffff807`00000000 ffffbd0a`67bdc880 ffff8100`fe54f180 00000001`00000000 : 0x00000002`00000000
SYMBOL_NAME: ONE_BIT
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: hardware
IMAGE_NAME: memory_corruption
DEBUG_FLR_IMAGE_TIMESTAMP: 0
STACK_COMMAND: .thread ; .cxr ; kb
FAILURE_BUCKET_ID: MEMORY_CORRUPTION_ONE_BIT
BUCKET_ID: MEMORY_CORRUPTION_ONE_BIT
PRIMARY_PROBLEM_CLASS: MEMORY_CORRUPTION_ONE_BIT
TARGET_TIME: 2020-02-18T19:49:01.000Z
OSBUILD: 18362
OSSERVICEPACK: 0
SERVICEPACK_NUMBER: 0
OS_REVISION: 0
SUITE_MASK: 272
PRODUCT_TYPE: 1
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
OSEDITION: Windows 10 WinNt TerminalServer SingleUserTS
OS_LOCALE:
USER_LCID: 0
OSBUILD_TIMESTAMP: unknown_date
ANALYSIS_SESSION_ELAPSED_TIME: 14
ANALYSIS_SOURCE: KM
FAILURE_ID_HASH_STRING: km:memory_corruption_one_bit
FAILURE_ID_HASH: {e3faf315-c3d0-81db-819a-6c43d23c63a7}
Followup: MachineOwner
---------
MEMORY_MANAGEMENT (1a)
# Any other values for parameter 1 must be individually examined.
Arguments:
Arg1: 0000000000041792, A corrupt PTE has been detected. Parameter 2 contains the address of
the PTE. Parameters 3/4 contain the low/high parts of the PTE.
Arg2: fffffb3fffa7d180
Arg3: 0000000200000000
Arg4: 0000000000000000
Debugging Details:
------------------
KEY_VALUES_STRING: 1
PROCESSES_ANALYSIS: 1
SERVICE_ANALYSIS: 1
STACKHASH_ANALYSIS: 1
TIMELINE_ANALYSIS: 1
DUMP_CLASS: 1
DUMP_QUALIFIER: 400
BUILD_VERSION_STRING: 18362.1.amd64fre.19h1_release.190318-1202
DUMP_TYPE: 2
BUGCHECK_P1: 41792
BUGCHECK_P2: fffffb3fffa7d180
BUGCHECK_P3: 200000000
BUGCHECK_P4: 0
MEMORY_CORRUPTOR: ONE_BIT
BUGCHECK_STR: 0x1a_41792
CPU_COUNT: 4
CPU_MHZ: d40
CPU_VENDOR: GenuineIntel
CPU_FAMILY: 6
CPU_MODEL: 3c
CPU_STEPPING: 3
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: WIN8_DRIVER_FAULT
PROCESS_NAME: ShellExperienceHost.exe
CURRENT_IRQL: 2
ANALYSIS_SESSION_HOST: DESKTOP-18V31A3
ANALYSIS_SESSION_TIME: 02-19-2020 21:47:58.0401
ANALYSIS_VERSION: 10.0.18362.1 x86fre
STACK_TEXT:
ffffda04`595c5f68 fffff803`6ee253ee : 00000000`0000001a 00000000`00041792 fffffb3f`ffa7d180 00000002`00000000 : nt!KeBugCheckEx
ffffda04`595c5f70 fffff803`6ecac957 : 00000000`00000000 fffffb3f`ffa7d180 00000000`00000000 00000000`00000000 : nt!MiDeleteVa+0x176c9e
ffffda04`595c6080 fffff803`6ecace11 : ffffda04`595c64d0 fffffb7d`9fffd3e8 00000000`00000000 0a000001`32f17867 : nt!MiWalkPageTablesRecursively+0x1e7
ffffda04`595c6140 fffff803`6ecace11 : ffffda04`595c64d0 fffffb7d`becfffe8 00000000`00000000 0a000001`32ee8867 : nt!MiWalkPageTablesRecursively+0x6a1
ffffda04`595c6200 fffff803`6ecace11 : ffffda04`595c64d0 fffffb7d`bedf67f8 fffffb7d`00000000 8a000001`d15cc867 : nt!MiWalkPageTablesRecursively+0x6a1
ffffda04`595c62c0 fffff803`6ecac59c : ffffda04`595c64d0 fffffb7d`bedf6fb0 ffffda04`00000000 ffffda04`595c6449 : nt!MiWalkPageTablesRecursively+0x6a1
ffffda04`595c6380 fffff803`6ecaaa08 : ffffda04`595c64d0 00000000`00000002 00000000`00000001 00000000`00000000 : nt!MiWalkPageTables+0x36c
ffffda04`595c6480 fffff803`6ecb8b60 : ffffffff`ffffffff ffffdc0f`36928778 ffffda04`00000001 00000000`00000000 : nt!MiDeletePagablePteRange+0x268
ffffda04`595c6820 fffff803`6f1c7bfd : ffffdc0f`34388040 ffffdc0f`34388040 ffffdc0f`3677db10 ffffdc0f`36928770 : nt!MiDeleteVad+0x860
ffffda04`595c69e0 fffff803`6f1d9fb4 : ffffdc0f`3677db10 ffffdc0f`36aa0a60 ffffdc0f`34388040 00000000`00000000 : nt!MiUnmapVad+0x49
ffffda04`595c6a10 fffff803`6f1d9a6f : ffffdc0f`3677f4b0 ffffdc0f`3677f4b0 ffffdc0f`36928400 fffff803`6f06a400 : nt!MiCleanVad+0x30
ffffda04`595c6a40 fffff803`6f238941 : ffffffff`00000000 ffffffff`ffffffff 00000000`00000001 ffffdc0f`36928400 : nt!MmCleanProcessAddressSpace+0x137
ffffda04`595c6ac0 fffff803`6f4cb412 : 00000000`00000300 ffffdc0f`36928400 fffff803`6f4cb3e0 ffffdc0f`2ee90a20 : nt!PspRundownSingleProcess+0x139
ffffda04`595c6b40 fffff803`6ecbd005 : ffffdc0f`34388040 ffffdc0f`34388000 fffff803`6ed15f00 ffffdc0f`2ee90a20 : nt!PspProcessRundownWorkerSingle+0x32
ffffda04`595c6b70 fffff803`6ed2a7b5 : ffffdc0f`34388040 00000000`00000080 ffffdc0f`2ee8d300 ffffda04`00000001 : nt!ExpWorkerThread+0x105
ffffda04`595c6c10 fffff803`6edc8b5a : ffffb501`7fa00180 ffffdc0f`34388040 fffff803`6ed2a760 00000000`00000000 : nt!PspSystemThreadStartup+0x55
ffffda04`595c6c60 00000000`00000000 : ffffda04`595c7000 ffffda04`595c1000 00000000`00000000 00000000`00000000 : nt!KiStartSystemThread+0x2a
THREAD_SHA1_HASH_MOD_FUNC: f0658b3c09201cb6ded3fdc9146b2222bda022d0
THREAD_SHA1_HASH_MOD_FUNC_OFFSET: da278a9e228962e6fb37aefc86c9092d1521c792
THREAD_SHA1_HASH_MOD: aaa5a324bf1bd3082ad2b464ee2ed2f6d50e564c
SYMBOL_NAME: ONE_BIT
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: hardware
IMAGE_NAME: memory_corruption
DEBUG_FLR_IMAGE_TIMESTAMP: 0
STACK_COMMAND: .thread ; .cxr ; kb
FAILURE_BUCKET_ID: MEMORY_CORRUPTION_ONE_BIT
BUCKET_ID: MEMORY_CORRUPTION_ONE_BIT
PRIMARY_PROBLEM_CLASS: MEMORY_CORRUPTION_ONE_BIT
TARGET_TIME: 2020-02-18T19:51:08.000Z
OSBUILD: 18362
OSSERVICEPACK: 657
SERVICEPACK_NUMBER: 0
OS_REVISION: 0
SUITE_MASK: 272
PRODUCT_TYPE: 1
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
OSEDITION: Windows 10 WinNt TerminalServer SingleUserTS
OS_LOCALE:
USER_LCID: 0
OSBUILD_TIMESTAMP: 2005-04-23 04:40:32
BUILDDATESTAMP_STR: 190318-1202
BUILDLAB_STR: 19h1_release
BUILDOSVER_STR: 10.0.18362.1.amd64fre.19h1_release.190318-1202
ANALYSIS_SESSION_ELAPSED_TIME: 2378
ANALYSIS_SOURCE: KM
FAILURE_ID_HASH_STRING: km:memory_corruption_one_bit
FAILURE_ID_HASH: {e3faf315-c3d0-81db-819a-6c43d23c63a7}
Followup: MachineOwner
---------
MEMORY_MANAGEMENT (1a)
# Any other values for parameter 1 must be individually examined.
Arguments:
Arg1: 0000000000041792, A corrupt PTE has been detected. Parameter 2 contains the address of
the PTE. Parameters 3/4 contain the low/high parts of the PTE.
Arg2: ffff873ffad5d448
Arg3: 0000000200000000
Arg4: 0000000000000000
Debugging Details:
------------------
***** Debugger could not find nt in module list, module list might be corrupt, error 0x80070057.
KEY_VALUES_STRING: 1
PROCESSES_ANALYSIS: 1
SERVICE_ANALYSIS: 1
STACKHASH_ANALYSIS: 1
TIMELINE_ANALYSIS: 1
DUMP_CLASS: 1
DUMP_QUALIFIER: 400
DUMP_TYPE: 2
BUGCHECK_P1: 41792
BUGCHECK_P2: ffff873ffad5d448
BUGCHECK_P3: 200000000
BUGCHECK_P4: 0
MEMORY_CORRUPTOR: ONE_BIT
BUGCHECK_STR: 0x1a_41792
CPU_COUNT: 4
CPU_MHZ: d40
CPU_VENDOR: GenuineIntel
CPU_FAMILY: 6
CPU_MODEL: 3c
CPU_STEPPING: 3
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: WIN8_DRIVER_FAULT
CURRENT_IRQL: 0
ANALYSIS_SESSION_HOST: DESKTOP-18V31A3
ANALYSIS_SESSION_TIME: 02-19-2020 21:48:02.0069
ANALYSIS_VERSION: 10.0.18362.1 x86fre
STACK_TEXT:
ffffec0b`18683b68 fffff800`5aa253ee : 00000000`0000001a 00000000`00041792 ffff873f`fad5d448 00000002`00000000 : 0xfffff800`5a9c1510
ffffec0b`18683b70 00000000`0000001a : 00000000`00041792 ffff873f`fad5d448 00000002`00000000 00000000`00000000 : 0xfffff800`5aa253ee
ffffec0b`18683b78 00000000`00041792 : ffff873f`fad5d448 00000002`00000000 00000000`00000000 fffff800`00000000 : 0x1a
ffffec0b`18683b80 ffff873f`fad5d448 : 00000002`00000000 00000000`00000000 fffff800`00000000 ffff9d85`9e2728c0 : 0x41792
ffffec0b`18683b88 00000002`00000000 : 00000000`00000000 fffff800`00000000 ffff9d85`9e2728c0 ffffec0b`18684180 : 0xffff873f`fad5d448
ffffec0b`18683b90 00000000`00000000 : fffff800`00000000 ffff9d85`9e2728c0 ffffec0b`18684180 fffff000`00000000 : 0x00000002`00000000
SYMBOL_NAME: ONE_BIT
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: hardware
IMAGE_NAME: memory_corruption
DEBUG_FLR_IMAGE_TIMESTAMP: 0
STACK_COMMAND: .thread ; .cxr ; kb
FAILURE_BUCKET_ID: MEMORY_CORRUPTION_ONE_BIT
BUCKET_ID: MEMORY_CORRUPTION_ONE_BIT
PRIMARY_PROBLEM_CLASS: MEMORY_CORRUPTION_ONE_BIT
TARGET_TIME: 2020-02-18T20:51:36.000Z
OSBUILD: 18362
OSSERVICEPACK: 0
SERVICEPACK_NUMBER: 0
OS_REVISION: 0
SUITE_MASK: 272
PRODUCT_TYPE: 1
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
OSEDITION: Windows 10 WinNt TerminalServer SingleUserTS
OS_LOCALE:
USER_LCID: 0
OSBUILD_TIMESTAMP: unknown_date
ANALYSIS_SESSION_ELAPSED_TIME: 15
ANALYSIS_SOURCE: KM
FAILURE_ID_HASH_STRING: km:memory_corruption_one_bit
FAILURE_ID_HASH: {e3faf315-c3d0-81db-819a-6c43d23c63a7}
Followup: MachineOwner
---------