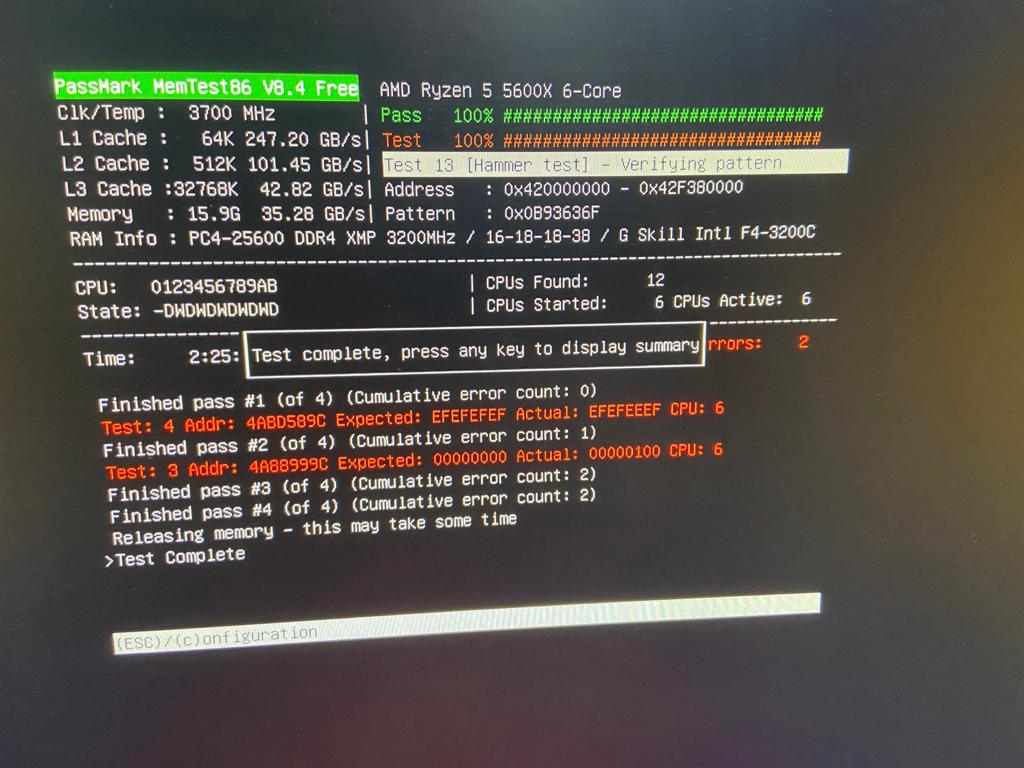
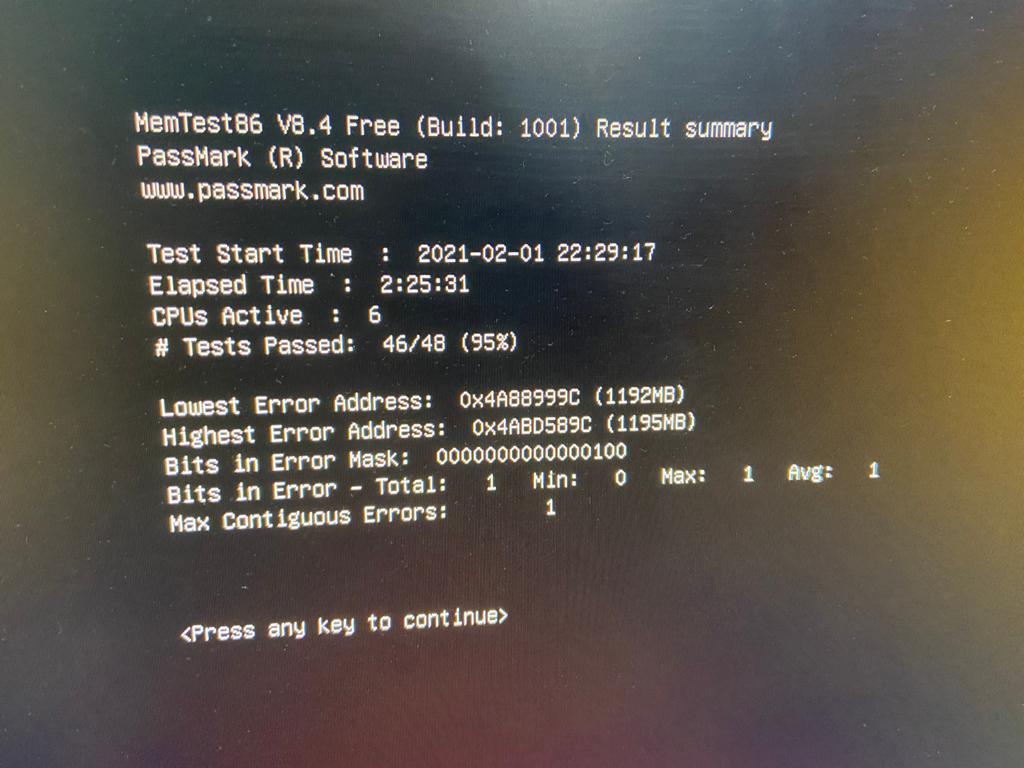
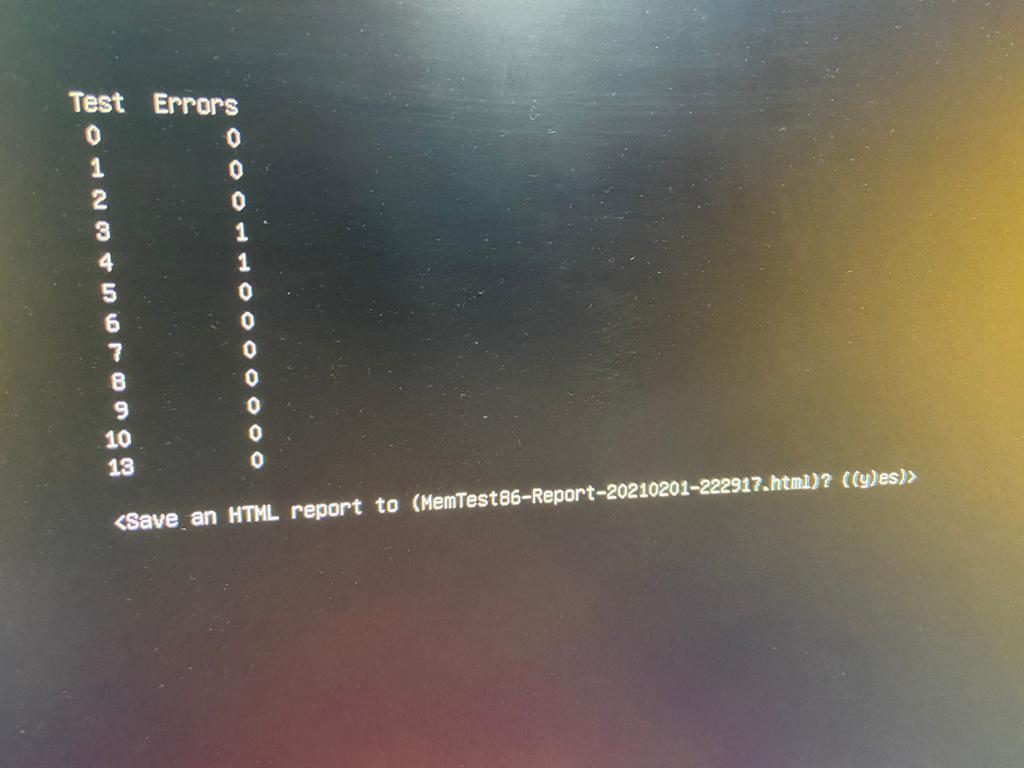
Microsoft (R) Windows Debugger Version 10.0.20153.1000 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Users\hazar\AppData\Local\Temp\7zO8A5EB612\013121-10984-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
************* Path validation summary **************
Response Time (ms) Location
Deferred srv*
Symbol search path is: srv*
Executable search path is:
Windows 10 Kernel Version 19041 MP (12 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Edition build lab: 19041.1.amd64fre.vb_release.191206-1406
Machine Name:
Kernel base = 0xfffff801`44400000 PsLoadedModuleList = 0xfffff801`4502a2f0
Debug session time: Sun Jan 31 16:02:43.824 2021 (UTC + 3:00)
System Uptime: 1 days 18:53:09.307
Loading Kernel Symbols
...............................................................
................................................................
................................................................
.....
Loading User Symbols
Loading unloaded module list
.................................
For analysis of this file, run !analyze -v
nt!KeBugCheckEx:
fffff801`447f5780 48894c2408 mov qword ptr [rsp+8],rcx ss:0018:ffffc287`693747a0=00000000000000be
3: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
ATTEMPTED_WRITE_TO_READONLY_MEMORY (be)
An attempt was made to write to readonly memory. The guilty driver is on the
stack trace (and is typically the current instruction pointer).
When possible, the guilty driver's name (Unicode string) is printed on
the bugcheck screen and saved in KiBugCheckDriver.
Arguments:
Arg1: fffff000045e0688, Virtual address for the attempted write.
Arg2: 8a00000000200121, PTE contents.
Arg3: ffffc28769374990, (reserved)
Arg4: 000000000000000a, (reserved)
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 3406
Key : Analysis.DebugAnalysisProvider.CPP
Value: Create: 8007007e on DESKTOP-0H5DIQU
Key : Analysis.DebugData
Value: CreateObject
Key : Analysis.DebugModel
Value: CreateObject
Key : Analysis.Elapsed.mSec
Value: 4872
Key : Analysis.Memory.CommitPeak.Mb
Value: 76
Key : Analysis.System
Value: CreateObject
Key : WER.OS.Branch
Value: vb_release
Key : WER.OS.Timestamp
Value: 2019-12-06T14:06:00Z
Key : WER.OS.Version
Value: 10.0.19041.1
ADDITIONAL_XML: 1
OS_BUILD_LAYERS: 1
BUGCHECK_CODE: be
BUGCHECK_P1: fffff000045e0688
BUGCHECK_P2: 8a00000000200121
BUGCHECK_P3: ffffc28769374990
BUGCHECK_P4: a
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: sihost.exe
TRAP_FRAME: ffffc28769374990 -- (.trap 0xffffc28769374990)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=7fffffffffffffff rbx=0000000000000000 rcx=8000000000000034
rdx=3fffffffffffffff rsi=0000000000000000 rdi=0000000000000000
rip=fffff8014495291a rsp=ffffc28769374b20 rbp=ffffc28769374c09
r8=ffffee8004bcfae0 r9=fffff80145050b80 r10=ffff8e8000000000
r11=ffffc28769374db0 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl zr na po nc
nt!MiBuildForkPte+0x62e:
fffff801`4495291a f0490fba6d183f lock bts qword ptr [r13+18h],3Fh ds:00000000`00000018=????????????????
Resetting default scope
STACK_TEXT:
ffffc287`69374798 fffff801`44862ec8 : 00000000`000000be fffff000`045e0688 8a000000`00200121 ffffc287`69374990 : nt!KeBugCheckEx
ffffc287`693747a0 fffff801`4460ca4f : 8a000000`00200121 00000000`00000003 ffffc287`69374a10 00000000`00000000 : nt!MiRaisedIrqlFault+0x16caac
ffffc287`693747f0 fffff801`4480395e : 00000000`00000000 00000000`00000000 00000000`00000000 fffff801`447124cc : nt!MmAccessFault+0x4ef
ffffc287`69374990 fffff801`4495291a : 80008001`74acd025 ffffc287`00000000 00000000`00000000 ffffee80`067497a0 : nt!KiPageFault+0x35e
ffffc287`69374b20 fffff801`44953803 : ffffb08c`35d1c080 ffffb08c`375ce0c0 ffff8ebf`fec4cc68 ffffee80`0c651360 : nt!MiBuildForkPte+0x62e
ffffc287`69374c50 fffff801`44cd4991 : ffffb08c`35d1c080 ffffc287`69374f59 ffffb08c`375ce0c0 ffffb08c`375ce0c0 : nt!MiCloneVads+0x4ab
ffffc287`69374ee0 fffff801`44bf591f : 00000000`00000000 ffffc287`00000000 00000000`00000000 00000000`00000000 : nt!MiCloneProcessAddressSpace+0x261
ffffc287`69374fc0 fffff801`44af52df : 00000000`00002ab1 ffffc287`69375b40 00000000`00000000 00000000`00000000 : nt!MmInitializeProcessAddressSpace+0x1a6f93
ffffc287`693751b0 fffff801`44bb7dd2 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!PspAllocateProcess+0x1c4f
ffffc287`69375720 fffff801`44d013d5 : ffffceda`6910aaea ffffceda`6910a44a 00000000`00000000 00000000`00000000 : nt!PspCreateProcess+0x242
ffffc287`693759f0 fffff801`448071b8 : 00000000`00000000 00000000`00000000 000001e7`77566d4d ffffc287`69375aa8 : nt!NtCreateProcessEx+0x85
ffffc287`69375a50 00007ffd`ac2cc954 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x28
000000b9`2007f4b8 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x00007ffd`ac2cc954
SYMBOL_NAME: nt!MiRaisedIrqlFault+16caac
MODULE_NAME: nt
IMAGE_VERSION: 10.0.19041.746
STACK_COMMAND: .thread ; .cxr ; kb
IMAGE_NAME: ntkrnlmp.exe
BUCKET_ID_FUNC_OFFSET: 16caac
FAILURE_BUCKET_ID: 0xBE_nt!MiRaisedIrqlFault
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: vb_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {1c5b4d11-09e0-def3-d2d0-70a11d69b92d}
Followup: MachineOwner
---------
3: kd> lmvm nt
Browse full module list
start end module name
fffff801`44400000 fffff801`45446000 nt (pdb symbols) C:\ProgramData\Dbg\sym\ntkrnlmp.pdb\3D4400784115718818EFC898413F36C41\ntkrnlmp.pdb
Loaded symbol image file: ntkrnlmp.exe
Mapped memory image file: C:\ProgramData\Dbg\sym\ntoskrnl.exe\F516CD761046000\ntoskrnl.exe
Image path: ntkrnlmp.exe
Image name: ntkrnlmp.exe
Browse all global symbols functions data
Image was built with /Brepro flag.
Timestamp: F516CD76 (This is a reproducible build file hash, not a timestamp)
CheckSum: 00A5F4B4
ImageSize: 01046000
File version: 10.0.19041.746
Product version: 10.0.19041.746
File flags: 0 (Mask 3F)
File OS: 40004 NT Win32
File type: 1.0 App
File date: 00000000.00000000
Translations: 0409.04b0
Information from resource tables:
CompanyName: Microsoft Corporation
ProductName: Microsoft® Windows® Operating System
InternalName: ntkrnlmp.exe
OriginalFilename: ntkrnlmp.exe
ProductVersion: 10.0.19041.746
FileVersion: 10.0.19041.746 (WinBuild.160101.0800)
FileDescription: NT Kernel & System
LegalCopyright: © Microsoft Corporation. All rights reserved.
Microsoft (R) Windows Debugger Version 10.0.20153.1000 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Users\hazar\AppData\Local\Temp\7zO8A583C62\013121-10984-02.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
************* Path validation summary **************
Response Time (ms) Location
Deferred srv*
Symbol search path is: srv*
Executable search path is:
Windows 10 Kernel Version 19041 MP (12 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Edition build lab: 19041.1.amd64fre.vb_release.191206-1406
Machine Name:
Kernel base = 0xfffff800`81400000 PsLoadedModuleList = 0xfffff800`8202a2f0
Debug session time: Sun Jan 31 21:26:01.051 2021 (UTC + 3:00)
System Uptime: 0 days 5:02:07.654
Loading Kernel Symbols
...............................................................
................................................................
................................................................
...
Loading User Symbols
Loading unloaded module list
.............
For analysis of this file, run !analyze -v
nt!KeBugCheckEx:
fffff800`817f5780 48894c2408 mov qword ptr [rsp+8],rcx ss:0018:ffff890c`cd23f0f0=000000000000001a
6: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
MEMORY_MANAGEMENT (1a)
# Any other values for parameter 1 must be individually examined.
Arguments:
Arg1: 0000000000041792, A corrupt PTE has been detected. Parameter 2 contains the address of
the PTE. Parameters 3/4 contain the low/high parts of the PTE.
Arg2: ffffe4bffaed87a8
Arg3: 0000000000000008
Arg4: 0000000000000000
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 3312
Key : Analysis.DebugAnalysisProvider.CPP
Value: Create: 8007007e on DESKTOP-0H5DIQU
Key : Analysis.DebugData
Value: CreateObject
Key : Analysis.DebugModel
Value: CreateObject
Key : Analysis.Elapsed.mSec
Value: 5167
Key : Analysis.Memory.CommitPeak.Mb
Value: 74
Key : Analysis.System
Value: CreateObject
Key : WER.OS.Branch
Value: vb_release
Key : WER.OS.Timestamp
Value: 2019-12-06T14:06:00Z
Key : WER.OS.Version
Value: 10.0.19041.1
ADDITIONAL_XML: 1
OS_BUILD_LAYERS: 1
BUGCHECK_CODE: 1a
BUGCHECK_P1: 41792
BUGCHECK_P2: ffffe4bffaed87a8
BUGCHECK_P3: 8
BUGCHECK_P4: 0
MEMORY_CORRUPTOR: ONE_BIT
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 2
PROCESS_NAME: StartMenuExperienceHost.exe
STACK_TEXT:
ffff890c`cd23f0e8 fffff800`8169d0fa : 00000000`0000001a 00000000`00041792 ffffe4bf`faed87a8 00000000`00000008 : nt!KeBugCheckEx
ffff890c`cd23f0f0 fffff800`8160b9e6 : 00000000`00000000 ffff890c`cd23f6c0 00000000`0000084c ffffe4bf`faed87a8 : nt!MiDeleteVa+0x153a
ffff890c`cd23f1f0 fffff800`8160bafb : ffffe4f2`00000000 ffffd18c`33375740 ffff890c`00000000 ffff890c`cd23f660 : nt!MiWalkPageTablesRecursively+0x776
ffff890c`cd23f290 fffff800`8160bafb : ffffe4f2`792ffeb8 ffffd18c`33375740 ffff890c`00000001 ffff890c`cd23f670 : nt!MiWalkPageTablesRecursively+0x88b
ffff890c`cd23f330 fffff800`8160bafb : ffffe4f2`792ff000 ffffd18c`33375740 ffff890c`00000002 ffff890c`cd23f680 : nt!MiWalkPageTablesRecursively+0x88b
ffff890c`cd23f3d0 fffff800`8165de6b : 00000000`00000000 ffffd18c`33375740 00000000`00000003 ffff890c`cd23f690 : nt!MiWalkPageTablesRecursively+0x88b
ffff890c`cd23f470 fffff800`8169b991 : ffff890c`cd23f610 ffffd18c`00000000 ffffe4be`00000002 00000000`00000000 : nt!MiWalkPageTables+0x36b
ffff890c`cd23f570 fffff800`8166baf0 : 00000000`00000001 ffff890c`00000000 ffffd18c`33375590 ffffd18c`361b7040 : nt!MiDeletePagablePteRange+0x4f1
ffff890c`cd23f880 fffff800`81a35c99 : ffffd18c`3573e740 00000000`00000000 ffffd18c`00000000 ffffd18c`00000000 : nt!MiDeleteVad+0x360
ffff890c`cd23f990 fffff800`81a35330 : ffffd18c`3573e740 ffffd18c`33375d60 ffffd18c`361b7040 00000000`00000000 : nt!MiUnmapVad+0x49
ffff890c`cd23f9c0 fffff800`81a335ff : ffffd18c`3573de80 ffffd18c`3573de80 ffffd18c`3573e740 ffffd18c`333750c0 : nt!MiCleanVad+0x30
ffff890c`cd23f9f0 fffff800`81a5d6e4 : ffffffff`00000000 ffffffff`ffffffff 00000000`00000001 ffffd18c`333750c0 : nt!MmCleanProcessAddressSpace+0x137
ffff890c`cd23fa70 fffff800`81d06b12 : fffff800`82124440 ffffd18c`333750c0 fffff800`81d06ae0 00000000`00000100 : nt!PspRundownSingleProcess+0x20c
ffff890c`cd23fb00 fffff800`81625975 : ffffd18c`361b7040 fffff800`81ad7210 ffffd18c`208aacc0 ffffd18c`00000000 : nt!PspProcessRundownWorkerSingle+0x32
ffff890c`cd23fb30 fffff800`81717e25 : ffffd18c`361b7040 00000000`00000080 ffffd18c`20887040 7f38d6c4`7378d6c0 : nt!ExpWorkerThread+0x105
ffff890c`cd23fbd0 fffff800`817fcdd8 : ffff9401`71560180 ffffd18c`361b7040 fffff800`81717dd0 d2003840`de403844 : nt!PspSystemThreadStartup+0x55
ffff890c`cd23fc20 00000000`00000000 : ffff890c`cd240000 ffff890c`cd239000 00000000`00000000 00000000`00000000 : nt!KiStartSystemThread+0x28
MODULE_NAME: hardware
IMAGE_NAME: memory_corruption
STACK_COMMAND: .thread ; .cxr ; kb
FAILURE_BUCKET_ID: MEMORY_CORRUPTION_ONE_BIT
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: vb_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {e3faf315-c3d0-81db-819a-6c43d23c63a7}
Followup: MachineOwner
---------