- RAM
- GSKILL 32GB (2x16GB) FLARE X5 DDR5 6000MHz CL36
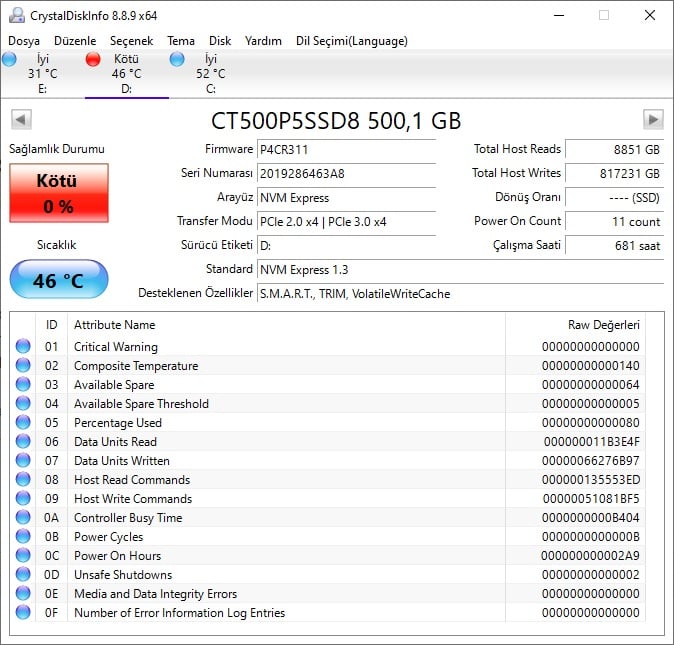
- SSD veya HDD modeli
- KINGSTON KC3000 2 TB NVME
- Ekran kartı
- 3060 Ti
- Anakart
- Asus TUF Gaming X670E-Plus WIFI
- İşlemci
- AMD Ryzen 7 7700X
Merhaba, çoğu sorunumun çözümü için forumdan faydalanıyordum. Fakat bu sefer çözemediğim bir sorun için üye oldum ve ilk mesajımla sizlerden yardım rica ediyorum. Elimden geldiğince detaylı açıklamaya çalışacağım.
Yeni bir sistem topladım, sistemin özellikleri:
Bazen durduk yere, bazen Chrome kullanırken, bazen Steam üzerinden oyuna çalıştır dediğim anda, bazen oyun içerisinden ana-menüye dönerken değişik ve random zamanlarda mavi ekran hatası alıyorum. Bazense, sistem mavi ekran hatası vermeden direkt kendini resetliyor.
Forumda gördüğüm ve araştırabildiğim her yöntemi denedim. (Sfcscan, DISM, sistemi formatlayıp sıfırdan kurma, tüm driverlar ve Windows güncel, BIOS güncel, GPU'da herhangi bir OC yok, CPU Max: 72 derece, GPU sıcaklığı Max: 85)
Memtest86 sonucu temiz çıktı, sonuca ilişkin görüntü:

-BIOS'ta yaptığım tek ayar, AI Overclock Tuner => Expo2 ve CPU Core Ratio = AI Optimized. Bu iki değişiklikten başka BIOS'ta bir değişiklik yapmadım.



Minidump Dosyalarından birkaçı:
 drive.google.com
drive.google.com
Mavi ekran almadığım zamanlar için olay görüntüleyiciden birkaç örnek:





Zahmet verip vaktinizden ayırıp okuduğunuz için teşekkür ederim. Gerçekten çözüm noktasında fikrim kalmadı.
OC ve Undervoltage konularında oldukça zayıfım. Hele ki yeni seri işlemciler konusunda epey uzak kaldım.
Bu nedenle stok ayarlar dışında pek bir değişiklik yapmadım/yapamadım.
Kıymetli geri dönüşleriniz için şimdiden teşekkürler.
Yeni bir sistem topladım, sistemin özellikleri:
Windows 11 Pro kullanıyorum.
| GSKILL 32GB (2x16GB) FLARE X5 DDR5 6000MHz CL36 1.35V PC RAM |
| Asus TUF Gaming X670E-Plus WIFI AMD X670 |
| AMD Ryzen 7 7700X 4.5 GHz |
| KINGSTON KC3000 2 TB NVME GEN4 SSD 7000/7000 |
| COOLER MASTER MASTELIQUID ML240 SIVI SOGUTMA KITI |
| MSI MAG FORGE 112R |
| Gigabyte 3060 Ti Vision |
| COUGAR GEX850 850W 80PLUS GOLD GÜÇ KAYNAĞI |
Bazen durduk yere, bazen Chrome kullanırken, bazen Steam üzerinden oyuna çalıştır dediğim anda, bazen oyun içerisinden ana-menüye dönerken değişik ve random zamanlarda mavi ekran hatası alıyorum. Bazense, sistem mavi ekran hatası vermeden direkt kendini resetliyor.
Forumda gördüğüm ve araştırabildiğim her yöntemi denedim. (Sfcscan, DISM, sistemi formatlayıp sıfırdan kurma, tüm driverlar ve Windows güncel, BIOS güncel, GPU'da herhangi bir OC yok, CPU Max: 72 derece, GPU sıcaklığı Max: 85)
Memtest86 sonucu temiz çıktı, sonuca ilişkin görüntü:
-BIOS'ta yaptığım tek ayar, AI Overclock Tuner => Expo2 ve CPU Core Ratio = AI Optimized. Bu iki değişiklikten başka BIOS'ta bir değişiklik yapmadım.
Minidump Dosyalarından birkaçı:
minidump.rar
 drive.google.com
drive.google.com
Mavi ekran almadığım zamanlar için olay görüntüleyiciden birkaç örnek:
Zahmet verip vaktinizden ayırıp okuduğunuz için teşekkür ederim. Gerçekten çözüm noktasında fikrim kalmadı.
OC ve Undervoltage konularında oldukça zayıfım. Hele ki yeni seri işlemciler konusunda epey uzak kaldım.
Bu nedenle stok ayarlar dışında pek bir değişiklik yapmadım/yapamadım.
Kıymetli geri dönüşleriniz için şimdiden teşekkürler.
Son düzenleme: