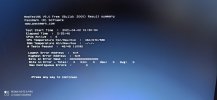
Microsoft (R) Windows Debugger Version 10.0.21306.1007 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\WINDOWS\MEMORY.DMP]
Kernel Bitmap Dump File: Full address space is available
************* Path validation summary **************
Response Time (ms) Location
Deferred srv*
Symbol search path is: srv*
Executable search path is:
Windows 10 Kernel Version 19041 MP (6 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Edition build lab: 19041.1.amd64fre.vb_release.191206-1406
Machine Name:
Kernel base = 0xfffff803`59800000 PsLoadedModuleList = 0xfffff803`5a42a490
Debug session time: Fri Apr 2 00:26:12.574 2021 (UTC + 3:00)
System Uptime: 0 days 0:06:53.196
Loading Kernel Symbols
...............................................................
................................................................
........................................................
Loading User Symbols
................................
Loading unloaded module list
.........
For analysis of this file, run !analyze -v
nt!KeBugCheckEx:
fffff803`59bf5db0 48894c2408 mov qword ptr [rsp+8],rcx ss:0018:ffffe604`a5d23950=0000000000000001
3: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
APC_INDEX_MISMATCH (1)
This is a kernel internal error. The most common reason to see this
bugcheck is when a filesystem or a driver has a mismatched number of
calls to disable and re-enable APCs. The key data item is the
Thread->CombinedApcDisable field. This consists of two separate 16-bit
fields, the SpecialApcDisable and the KernelApcDisable. A negative value
of either indicates that a driver has disabled special or normal APCs
(respectively) without re-enabling them; a positive value indicates that
a driver has enabled special or normal APCs (respectively) too many times.
Arguments:
Arg1: 00007ffccba4cef4, Address of system call function or worker routine
Arg2: 0000000000000000, Thread->ApcStateIndex
Arg3: 000000000000ffff, (Thread->SpecialApcDisable << 16) | Thread->KernelApcDisable
Arg4: ffffe604a5d23b80, Call type (0 - system call, 1 - worker routine)
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 3062
Key : Analysis.DebugAnalysisManager
Value: Create
Key : Analysis.Elapsed.mSec
Value: 54881
Key : Analysis.Init.CPU.mSec
Value: 531
Key : Analysis.Init.Elapsed.mSec
Value: 140287
Key : Analysis.Memory.CommitPeak.Mb
Value: 93
Key : WER.OS.Branch
Value: vb_release
Key : WER.OS.Timestamp
Value: 2019-12-06T14:06:00Z
Key : WER.OS.Version
Value: 10.0.19041.1
BUGCHECK_CODE: 1
BUGCHECK_P1: 7ffccba4cef4
BUGCHECK_P2: 0
BUGCHECK_P3: ffff
BUGCHECK_P4: ffffe604a5d23b80
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXWINLOGON: 1
PROCESS_NAME: WMIADAP.exe
STACK_TEXT:
ffffe604`a5d23948 fffff803`59c07d69 : 00000000`00000001 00007ffc`cba4cef4 00000000`00000000 00000000`0000ffff : nt!KeBugCheckEx
ffffe604`a5d23950 fffff803`59c07c33 : 00000000`00000080 00000000`00014c81 00000000`00000000 00000000`00000000 : nt!KiBugCheckDispatch+0x69
ffffe604`a5d23a90 00007ffc`cba4cef4 : 00007ffc`c954efef 00000000`00000000 000000ed`876ef098 00000000`00000000 : nt!KiSystemServiceExitPico+0x1fe
000000ed`876eec68 00007ffc`c954efef : 00000000`00000000 000000ed`876ef098 00000000`00000000 00000000`00000000 : ntdll!NtQueryValueKey+0x14
000000ed`876eec70 00007ffc`c954e9a3 : 000000ed`876ef068 00007ffc`c13aa128 00007ffc`c13aa198 000000ed`876ef0a8 : KERNELBASE!LocalBaseRegQueryValue+0x17f
000000ed`876eefb0 00007ffc`c135e7a1 : 00000000`00000174 00000000`00000174 00000000`00000004 000000ed`876ef0c8 : KERNELBASE!RegQueryValueExW+0xf3
000000ed`876ef050 00000000`00000174 : 00000000`00000174 00000000`00000004 000000ed`876ef0c8 000000ed`876ef0ac : wbemcomn!Throttle+0x1a1
000000ed`876ef058 00000000`00000174 : 00000000`00000004 000000ed`876ef0c8 000000ed`876ef0ac 000000ed`876ef0a8 : 0x174
000000ed`876ef060 00000000`00000004 : 000000ed`876ef0c8 000000ed`876ef0ac 000000ed`876ef0a8 0000027b`8e1f0000 : 0x174
000000ed`876ef068 000000ed`876ef0c8 : 000000ed`876ef0ac 000000ed`876ef0a8 0000027b`8e1f0000 000000ed`876ef149 : 0x4
000000ed`876ef070 000000ed`876ef0ac : 000000ed`876ef0a8 0000027b`8e1f0000 000000ed`876ef149 0000000a`00000000 : 0x000000ed`876ef0c8
000000ed`876ef078 000000ed`876ef0a8 : 0000027b`8e1f0000 000000ed`876ef149 0000000a`00000000 0000012c`00000002 : 0x000000ed`876ef0ac
000000ed`876ef080 0000027b`8e1f0000 : 000000ed`876ef149 0000000a`00000000 0000012c`00000002 00000000`00000000 : 0x000000ed`876ef0a8
000000ed`876ef088 000000ed`876ef149 : 0000000a`00000000 0000012c`00000002 00000000`00000000 00000001`00000004 : 0x0000027b`8e1f0000
000000ed`876ef090 0000000a`00000000 : 0000012c`00000002 00000000`00000000 00000001`00000004 00000064`00989680 : 0x000000ed`876ef149
000000ed`876ef098 0000012c`00000002 : 00000000`00000000 00000001`00000004 00000064`00989680 00000000`00000174 : 0x0000000a`00000000
000000ed`876ef0a0 00000000`00000000 : 00000001`00000004 00000064`00989680 00000000`00000174 00000000`00000008 : 0x0000012c`00000002
SYMBOL_NAME: nt!KiSystemServiceExitPico+1fe
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
STACK_COMMAND: .thread ; .cxr ; kb
BUCKET_ID_FUNC_OFFSET: 1fe
FAILURE_BUCKET_ID: 0x1_SysCallNum_17_nt!KiSystemServiceExitPico
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: vb_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {23f7ad48-43c8-00ca-9cb7-932ab9140c73}
Followup: MachineOwner
---------
 drive.google.com
drive.google.com
 drive.google.com
drive.google.com