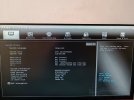
* Bu temaya dönmelerinin sebebi BIOS ROM'unun yetersiz olması. Yani güncel sürüme geçtiğinizde o rahatsız edici siyah beyaz temayla karşılaşmanız gayet normal. Bazı anakartlarda BIOS depolaması sınırlı. Benim de B450 Pro-VDH Plus anakartım varken Ryzen 3000 serisini desteklemek için bu anakarta BIOS güncellemesi çıkarmışlardı. BIOS'u güncellediğimde sizinki gibi siyah beyaz olmuştu ama 4 yıl önce. Şu an kullandığım B450 Tomahawk Max anakartta böyle bir durum yok, çünkü depolaması yeterli ve BIOS güncellemelerini arayüz tasarımından feda etmeden alabiliyor hâlâ.
* Konuyla ilgili detaylı açıklama:
Merhabalar. BIOS'a güncelleme gelmiş yapayım dedim. Her şey bitti sürümü kontrol etmek için delete tuşuna bastım çok sade bir görüntü ile karşılaştım. Eski temaya dönmek istiyorum, bu nasıl olacak? Tam ekran olan sonraki görüntü. Diğer resmi bunun olacağını bilmeden çekmiştim.
www.technopat.net
* Mavi ekran analizine dönersek, yüklediğiniz BIOS en güncel sürüm ama beta bir sürüm. Ondan önceki de aynı şekilde. O yüzden BIOS'u beta olmayan bir versiyona düşürmeniz problemi çözebilir.
* Ama bundan önce deneyebileceğiniz bazı şeyler var.
* Denetim Masası program ekle/kaldırdan eski chipset sürücülerinizi silin (AMD chipset software) ve AMD sitesinden yenisini indirin ve kurun. Yakın zamanda güncelleme geldi. Yaşadığınız problemin çözümünde yardımcı olacaktır diye düşünüyorum.
* Dosya sisteminde de problemler olabilir. O yüzden CMD'yi yönetici olarak çalıştırıp aşağıdaki komutları tek tek kopyalayın ve yapıştırın. Biri bitince diğerini yapıştırın. Tarama yapıp bir problem varsa onarsın.
SFC /scannow
DISM /Online /Cleanup-Image /RestoreHealth
* PC'de takılı kalmış bir USB var mı? Çünkü mavi ekranlardan birinde USB sürücüsü hata veriyor. Varsa USB'yi sökün. USB'nin kendisi veya sürücüsü direkt olarak arızalı olabilir. Mümkünse sağlam bir USB ile deneyin BIOS güncellemesini.
* Ayrıca, pek fayda sağlayacağını sanmam ama Aygıt Yöneticisi'ni açıp resimdeki gibi USB sürücülerine tek tek sağ tıklayıp güncelleştirmeyi deneyebilirsiniz.
Eki Görüntüle 1814652
Eki Görüntüle 1814653
Döküm:
Kod:Panoya kopyala
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
KERNEL_SECURITY_CHECK_FAILURE (139)
A kernel component has corrupted a critical data structure. The corruption.
could potentially allow a malicious user to gain control of this machine.
Arguments:
Arg1: 000000000000001d, An RTL_BALANCED_NODE RBTree entry has been corrupted.
Arg2: ffff808b431331a0, Address of the trap frame for the exception that caused the BugCheck.
Arg3: ffff808b431330f8, Address of the exception record for the exception that caused the BugCheck.
Arg4: 0000000000000000, Reserved.
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 1500.
Key : Analysis.Elapsed.mSec
Value: 3438.
Key : Analysis.IO.Other.Mb
Value: 0
Key : Analysis.IO.Read.Mb
Value: 0
Key : Analysis.IO.Write.Mb
Value: 0
Key : Analysis.Init.CPU.mSec
Value: 202.
Key : Analysis.Init.Elapsed.mSec
Value: 1630.
Key : Analysis.Memory.CommitPeak.Mb
Value: 154.
Key : Bugcheck.Code.LegacyAPI
Value: 0x139.
Key : FailFast.Name
Value: INVALID_BALANCED_TREE
Key : FailFast.Type
Value: 29.
Key : Failure.Bucket
Value: 0x139_1d_INVALID_BALANCED_TREE_win32kfull!Win32AllocPoolWithQuotaImpl
Key : Failure.Hash
Value: {c935a560-7593-e6d1-c6ad-c8562d8364d5}
Key : WER.OS.Branch
Value: vb_release.
Key : WER.OS.Version
Value: 10.0.19041.1
BUGCHECK_CODE: 139.
BUGCHECK_P1: 1d.
BUGCHECK_P2: ffff808b431331a0.
BUGCHECK_P3: ffff808b431330f8.
BUGCHECK_P4: 0
FILE_IN_CAB: 060923-6328-01.dmp
TRAP_FRAME: ffff808b431331a0 -- (.trap 0xffff808b431331a0)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=ffff88bc846c6858 rbx=0000000000000000 rcx=000000000000001d
rdx=ffff88bc846c6858 rsi=0000000000000000 rdi=0000000000000000
rip=fffff8027f622391 rsp=ffff808b43133330 rbp=0000000000000001
r8=ffff88bc84e0ff68 r9=0000000000000000 r10=ffff88bc80200290
r11=0000000000000001 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei ng nz na pe cy.
nt!RtlRbInsertNodeEx+0x20b3e1:
fffff802`7f622391 cd29 int 29h.
Resetting default scope.
EXCEPTION_RECORD: ffff808b431330f8 -- (.exr 0xffff808b431330f8)
ExceptionAddress: fffff8027f622391 (nt!RtlRbInsertNodeEx+0x000000000020b3e1)
ExceptionCode: c0000409 (Security check failure or stack buffer overrun)
ExceptionFlags: 00000001.
NumberParameters: 1
Parameter[0]: 000000000000001d.
Subcode: 0x1d FAST_FAIL_INVALID_BALANCED_TREE
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: LockApp.exe
ERROR_CODE: (NTSTATUS) 0xc0000409 - Sistem, bu uygulamada y n tabanl bir arabelle in ta t n alg lad . Bu ta ma, k t niyetli bir kullan c n n bu uygulaman n denetimini ele ge irmesine olanak verebilir.
EXCEPTION_CODE_STR: c0000409.
EXCEPTION_PARAMETER1: 000000000000001d.
EXCEPTION_STR: 0xc0000409.
STACK_TEXT:
ffff808b`43132e78 fffff802`7f60fd29 : 00000000`00000139 00000000`0000001d ffff808b`431331a0 ffff808b`431330f8 : nt!KeBugCheckEx
ffff808b`43132e80 fffff802`7f610290 : 00000000`8453ead8 00000000`00000000 ffffffff`fffffff0 00000000`00000000 : nt!KiBugCheckDispatch+0x69
ffff808b`43132fc0 fffff802`7f60e25d : 00000000`00000000 ffff808b`43133310 ffffa401`f3f79890 fffff802`7f814511 : nt!KiFastFailDispatch+0xd0
ffff808b`431331a0 fffff802`7f622391 : ffff88bc`80200280 fffff802`7f415189 ffff88bc`84761c28 ffff808b`431333b8 : nt!KiRaiseSecurityCheckFailure+0x31d
ffff808b`43133330 fffff802`7f415189 : ffff88bc`84761c28 ffff808b`431333b8 00000000`00000025 ffff88bc`846c6850 : nt!RtlRbInsertNodeEx+0x20b3e1
ffff808b`43133340 fffff802`7f4149da : 00000008`00000008 ffff88bc`846c6600 fffff802`00000008 fffff802`00000000 : nt!RtlpHpVsChunkSplit+0x5d9
ffff808b`43133400 fffff802`7f412908 : 00000000`00000000 ffffe183`00000240 ffff808b`43133541 00000000`00000240 : nt!RtlpHpVsContextAllocateInternal+0x1fa
ffff808b`43133460 fffff802`7fbb7074 : 00000000`00000000 00000000`00000008 00000042`79747355 ffff889d`f184b300 : nt!ExAllocateHeapPool+0x888
ffff808b`431335a0 fffff802`7f40a590 : ffff88bc`80602080 00000000`00000029 00000000`00000000 fffff802`00000000 : nt!ExAllocatePoolWithTag+0x64
ffff808b`431335f0 ffff889d`f1d17d07 : ffffe183`379c5080 ffff88bc`80602080 00000042`79747355 ffff88bc`847619f0 : nt!ExAllocatePoolWithQuotaTag+0x60
ffff808b`43133670 ffff889d`f16596c1 : ffff644a`79747355 ffff808b`43133b80 00000000`00000029 ffff808b`43133750 : win32kfull!Win32AllocPoolWithQuotaImpl+0x37
ffff808b`43133740 ffff889d`f1737aa0 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`0000200c : win32kbase!Win32AllocPoolWithQuotaZInit+0x41
ffff808b`43133770 ffff889d`f1a1dbd1 : ffffe183`379c5080 ffff889d`00000000 00000042`f5ff5f40 00000000`00000000 : win32kbase!NtUserSystemParametersInfo+0x2c0
ffff808b`43133ac0 fffff802`7f60f4f8 : ffffe183`379c5000 00000000`00000000 ffff808b`43133b80 00000000`000015f8 : win32k!NtUserSystemParametersInfo+0x15
ffff808b`43133b00 00007ffe`8d241884 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x28
00000042`f5ff5cf8 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x00007ffe`8d241884
SYMBOL_NAME: win32kfull!Win32AllocPoolWithQuotaImpl+37
MODULE_NAME: win32kfull.
IMAGE_NAME: win32kfull.sys
IMAGE_VERSION: 10.0.19041.2965
STACK_COMMAND: .cxr; .ecxr ; kb.
BUCKET_ID_FUNC_OFFSET: 37.
FAILURE_BUCKET_ID: 0x139_1d_INVALID_BALANCED_TREE_win32kfull!Win32AllocPoolWithQuotaImpl
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: vb_release.
OSPLATFORM_TYPE: x64.
OSNAME: Windows 10.
FAILURE_ID_HASH: {c935a560-7593-e6d1-c6ad-c8562d8364d5}
Followup: MachineOwner.
---------
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
KERNEL_SECURITY_CHECK_FAILURE (139)
A kernel component has corrupted a critical data structure. The corruption.
could potentially allow a malicious user to gain control of this machine.
Arguments:
Arg1: 0000000000000000, A stack-based buffer has been overrun.
Arg2: 0000000000000000, Address of the trap frame for the exception that caused the BugCheck.
Arg3: 0000000000000000, Address of the exception record for the exception that caused the BugCheck.
Arg4: 0074007200610047, Reserved.
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 1453.
Key : Analysis.Elapsed.mSec
Value: 3992.
Key : Analysis.IO.Other.Mb
Value: 0
Key : Analysis.IO.Read.Mb
Value: 0
Key : Analysis.IO.Write.Mb
Value: 0
Key : Analysis.Init.CPU.mSec
Value: 233.
Key : Analysis.Init.Elapsed.mSec
Value: 16925.
Key : Analysis.Memory.CommitPeak.Mb
Value: 152.
Key : Bugcheck.Code.LegacyAPI
Value: 0x139.
Key : Failure.Bucket
Value: 0x139_0_LEGACY_GS_VIOLATION_USBXHCI!Bulk_Transfer_CompleteCancelable
Key : Failure.Hash
Value: {3327d191-00d8-a6be-1f4c-9c3d0d47a0bd}
Key : WER.OS.Branch
Value: vb_release.
Key : WER.OS.Version
Value: 10.0.19041.1
BUGCHECK_CODE: 139.
BUGCHECK_P1: 0
BUGCHECK_P2: 0
BUGCHECK_P3: 0
BUGCHECK_P4: 74007200610047.
FILE_IN_CAB: 060923-7000-01.dmp
TRAP_FRAME: 0000000000000000 -- (.trap 0x0)
EXCEPTION_RECORD: 0000000000000000 -- (.exr 0x0)
Cannot read Exception record @ 0000000000000000.
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: System.
STACK_TEXT:
fffff805`612d9ee8 fffff805`5ac05eab : 00000000`00000139 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KeBugCheckEx
fffff805`612d9ef0 fffff805`5fa0580d : 00000000`00000000 ffffc904`d1924850 ffffc904`d1794b20 00000000`00000000 : nt!guard_icall_bugcheck+0x1b
fffff805`612d9f20 fffff805`5f9b50eb : ffffc904`d1924850 ffffc904`d4adb6a0 00000000`00000001 ffffc904`d4ad5770 : Wdf01000!FxMemoryBufferFromLookaside::SelfDestruct+0x3d [minkernel\wdf\framework\shared\core\fxmemorybufferfromlookaside.cpp @ 236]
fffff805`612d9f60 fffff805`5f9b4f16 : ffffc904`d4ad5770 ffffc904`d1924850 fffff805`612da0d0 00000000`00000001 : Wdf01000!FxObject::ProcessDestroy+0xb7 [minkernel\wdf\framework\shared\object\fxobjectstatemachine.cpp @ 402]
fffff805`612d9fa0 fffff805`5fa40e8f : ffffc904`d17932a0 fffff805`5fa4bee8 fffff805`5fa47eb8 00000000`00000000 : Wdf01000!FxMemoryObject::Release+0x56 [minkernel\wdf\framework\shared\inc\private\common\FxMemoryObject.hpp @ 146]
fffff805`612d9fe0 fffff805`5fa1d248 : ffffc904`d4a62a70 fffff805`612da0d0 ffffc904`d49a4db0 fffff805`612da110 : Wdf01000!FxRequestContext::ReleaseAndRestore+0xdf [minkernel\wdf\framework\shared\core\fxrequestcontext.cpp @ 112]
fffff805`612da020 fffff805`5f9b2463 : ffffc904`d17bcab0 ffffc904`d49abdc0 fffff805`612da238 00000000`00000000 : Wdf01000!FxUsbPipeTransferContext::ReleaseAndRestore+0x78 [minkernel\wdf\framework\shared\targets\usb\fxusbpipe.cpp @ 880]
fffff805`612da050 fffff805`5fa1c5cc : 00000000`00000000 ffffc904`d4a3a7b0 fffff805`612da110 ffffc904`d17932a0 : Wdf01000!FxRequest::Reuse+0x83 [minkernel\wdf\framework\shared\core\fxrequest.cpp @ 2197]
fffff805`612da0b0 fffff805`5fa1d387 : 00000000`00000000 ffffc904`d4a3a7b0 ffffc904`d4a3a888 ffffc904`d49abdc0 : Wdf01000!FxUsbPipeContinuousReader::FormatRepeater+0x68 [minkernel\wdf\framework\shared\targets\usb\fxusbpipe.cpp @ 719]
fffff805`612da130 fffff805`5fa1d943 : ffffc904`00000000 ffffc904`d4a3a888 00000000`00000000 00000000`73556f49 : Wdf01000!FxUsbPipeContinuousReader::ResubmitRepeater+0x33 [minkernel\wdf\framework\shared\targets\usb\fxusbpipe.cpp @ 154]
fffff805`612da1b0 fffff805`5f9b9248 : ffffc904`d17932a0 00000000`00000001 fffff805`5fa1d8c0 00000000`00000000 : Wdf01000!FxUsbPipeContinuousReader::_FxUsbPipeRequestComplete+0x83 [minkernel\wdf\framework\shared\targets\usb\fxusbpipe.cpp @ 302]
fffff805`612da220 fffff805`5f9bc854 : 000036fb`2e86cd58 ffffc904`d17932a0 ffffc904`d17932a0 ffffc904`d19aea00 : Wdf01000!FxRequestBase::CompleteSubmitted+0xe8 [minkernel\wdf\framework\shared\core\fxrequestbase.cpp @ 530]
fffff805`612da2b0 fffff805`5ab25726 : ffffc904`d4988de0 ffffc904`d17bca02 ffffc904`d17bcab0 00000000`00000000 : Wdf01000!FxIoTarget::_RequestCompletionRoutine+0xe4 [minkernel\wdf\framework\shared\targets\general\fxiotarget.cpp @ 2448]
fffff805`612da320 fffff805`5aa92735 : ffffc904`d17bcf73 fffff805`612da3c9 ffffc904`d17bcab0 00000000`00000000 : nt!IopUnloadSafeCompletion+0x56
fffff805`612da350 fffff805`5aa92577 : ffffc904`d17bcab0 00000000`00000000 ffffc904`d4acda20 00000000`00000002 : nt!IopfCompleteRequest+0x1a5
fffff805`612da430 fffff805`5f9b811a : 00000000`00000000 ffffc904`d19aea30 ffffc904`d17bcab0 fffff805`612da510 : nt!IofCompleteRequest+0x17
fffff805`612da460 fffff805`5f9b5bbf : ffffc904`d4ad4102 ffffc904`d190f9a0 ffffc904`d17bcab0 00000000`00000000 : Wdf01000!FxRequest::CompleteInternal+0x23a [minkernel\wdf\framework\shared\core\fxrequest.cpp @ 869]
fffff805`612da4f0 fffff805`6d22c1ec : 00000000`ffffff02 ffffc904`d4ad4020 ffffc904`d4acde00 ffffc904`d4acde00 : Wdf01000!imp_WdfRequestComplete+0x8f [minkernel\wdf\framework\shared\core\fxrequestapi.cpp @ 436]
fffff805`612da550 fffff805`6d22c0b1 : ffffc904`d4ad41c0 00000000`00000008 ffffc904`d4ad4250 fffff805`612da768 : USBXHCI!Bulk_Transfer_CompleteCancelable+0xc8
fffff805`612da5b0 fffff805`6d22bea0 : 00000000`00000004 fffff805`612da720 00000000`00000000 ffffc904`d4acd480 : USBXHCI!Bulk_ProcessTransferEventWithED1+0x1fd
fffff805`612da660 fffff805`6d226910 : 00000000`00000004 fffff805`612da738 00000000`00000008 fffff805`612da740 : USBXHCI!Bulk_EP_TransferEventHandler+0x10
fffff805`612da690 fffff805`6d226445 : 00000000`00000780 000036fb`2e849800 ffffc904`d48b9e80 ffffc904`d1746470 : USBXHCI!Endpoint_TransferEventHandler+0xb0
fffff805`612da6f0 fffff805`6d22611c : ffffc904`d1b4f328 fffff805`5921d180 000036fb`2e84d438 fffff805`612da810 : USBXHCI!Interrupter_DeferredWorkProcessor+0x315
fffff805`612da7f0 fffff805`5f9b38f5 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : USBXHCI!Interrupter_WdfEvtInterruptDpc+0xc
fffff805`612da820 fffff805`5aa8b57e : fffff805`59220240 00000000`00000000 fffff805`612dab20 fffff805`5921d180 : Wdf01000!FxInterrupt::_InterruptDpcThunk+0xa5 [minkernel\wdf\framework\shared\irphandlers\pnp\km\interruptobjectkm.cpp @ 404]
fffff805`612da860 fffff805`5aa8a864 : 00000000`00000000 00000000`00000000 00000000`00140001 00000000`00000000 : nt!KiExecuteAllDpcs+0x30e
fffff805`612da9d0 fffff805`5ac0059e : 00000000`00000000 fffff805`5921d180 00000000`00000000 fffff805`5b527a00 : nt!KiRetireDpcList+0x1f4
fffff805`612dac60 00000000`00000000 : fffff805`612db000 fffff805`612d5000 00000000`00000000 00000000`00000000 : nt!KiIdleLoop+0x9e
SYMBOL_NAME: USBXHCI!Bulk_Transfer_CompleteCancelable+c8
MODULE_NAME: USBXHCI.
IMAGE_NAME: USBXHCI.SYS
IMAGE_VERSION: 10.0.19041.2546
STACK_COMMAND: .cxr; .ecxr ; kb.
BUCKET_ID_FUNC_OFFSET: c8.
FAILURE_BUCKET_ID: 0x139_0_LEGACY_GS_VIOLATION_USBXHCI!Bulk_Transfer_CompleteCancelable
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: vb_release.
OSPLATFORM_TYPE: x64.
OSNAME: Windows 10.
FAILURE_ID_HASH: {3327d191-00d8-a6be-1f4c-9c3d0d47a0bd}
Followup: MachineOwner.
---------
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
SYSTEM_SERVICE_EXCEPTION (3b)
An exception happened while executing a system service routine.
Arguments:
Arg1: 00000000c0000005, Exception code that caused the BugCheck.
Arg2: fffff80275923610, Address of the instruction which caused the BugCheck.
Arg3: ffffde0fadb92870, Address of the context record for the exception that caused the BugCheck.
Arg4: 0000000000000000, zero.
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 1359.
Key : Analysis.Elapsed.mSec
Value: 2826.
Key : Analysis.IO.Other.Mb
Value: 0
Key : Analysis.IO.Read.Mb
Value: 0
Key : Analysis.IO.Write.Mb
Value: 0
Key : Analysis.Init.CPU.mSec
Value: 125.
Key : Analysis.Init.Elapsed.mSec
Value: 11371.
Key : Analysis.Memory.CommitPeak.Mb
Value: 144.
Key : Bugcheck.Code.LegacyAPI
Value: 0x3b.
Key : Failure.Bucket
Value: AV_nt!MiProcessCrcList
Key : Failure.Hash
Value: {d3bd1154-0054-5a81-7657-185761932858}
Key : WER.OS.Branch
Value: vb_release.
Key : WER.OS.Version
Value: 10.0.19041.1
BUGCHECK_CODE: 3b.
BUGCHECK_P1: c0000005.
BUGCHECK_P2: fffff80275923610.
BUGCHECK_P3: ffffde0fadb92870.
BUGCHECK_P4: 0
FILE_IN_CAB: 060923-6078-01.dmp
CONTEXT: ffffde0fadb92870 -- (.cxr 0xffffde0fadb92870)
rax=ffff9500da1026c0 rbx=0000000000000000 rcx=ffff830d40ac8d30
rdx=ffff830d40acbe90 rsi=00000000004149e0 rdi=ffff830d3e63ce50
rip=fffff80275923610 rsp=ffffde0fadb93270 rbp=ffffde0fadb93329
r8=0000000000000000 r9=ffff830d40ac4230 r10=0000000000000053
r11=ffff830d40acbe98 r12=ffffde0fadb93590 r13=0000000000000000
r14=0000000000000128 r15=ffff9500da102000
iopl=0 nv up ei pl nz na pe nc.
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00050202
nt!MiProcessCrcList+0x580:
fffff802`75923610 488b7610 mov rsi,qword ptr [rsi+10h] ds:002b:00000000`004149f0=????????????????
Resetting default scope.
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: svchost.exe
STACK_TEXT:
ffffde0f`adb93270 fffff802`75923d07 : 00000000`00000000 ffffe080`0cbda7d0 00000000`00000080 00000000`00000001 : nt!MiProcessCrcList+0x580
ffffde0f`adb93390 fffff802`75922e30 : 00000000`00000000 00000000`00000000 ffffde0f`adb935c0 00000000`00000000 : nt!MiCombineAllPhysicalMemory+0x4e7
ffffde0f`adb934c0 fffff802`75922c0e : 00000000`0000000d 000000a5`8f07fe90 00000000`00000000 00000000`00000002 : nt!MiCombineIdenticalPages+0x214
ffffde0f`adb93730 fffff802`758f6e8e : 00000000`00000000 00000000`00000000 fffff802`72871180 00000000`00000001 : nt!MmCombineIdenticalPages+0x42
ffffde0f`adb93770 fffff802`7560f4f8 : ffff830d`3fdfa000 00000000`00000000 ffffde0f`adb93b80 00000000`00000000 : nt!NtSetSystemInformation+0x140e
ffffde0f`adb93b00 00007ff8`6c7505b4 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x28
000000a5`8f07fe18 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x00007ff8`6c7505b4
SYMBOL_NAME: nt!MiProcessCrcList+580
MODULE_NAME: nt.
IMAGE_VERSION: 10.0.19041.2965
STACK_COMMAND: .cxr 0xffffde0fadb92870 ; kb.
IMAGE_NAME: ntkrnlmp.exe
BUCKET_ID_FUNC_OFFSET: 580.
FAILURE_BUCKET_ID: AV_nt!MiProcessCrcList
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: vb_release.
OSPLATFORM_TYPE: x64.
OSNAME: Windows 10.
FAILURE_ID_HASH: {d3bd1154-0054-5a81-7657-185761932858}
Followup: MachineOwner.
---------
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
SYSTEM_SERVICE_EXCEPTION (3b)
An exception happened while executing a system service routine.
Arguments:
Arg1: 00000000c0000005, Exception code that caused the BugCheck.
Arg2: fffff80208943796, Address of the instruction which caused the BugCheck.
Arg3: fffff2853bdefa60, Address of the context record for the exception that caused the BugCheck.
Arg4: 0000000000000000, zero.
Debugging Details:
------------------
*** WARNING: Check Image - Checksum mismatch - Dump: 0x19328, File: 0x1bef2 - C:\ProgramData\Dbg\sym\bam.sys\4BADB6B817000\bam.sys
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 1421.
Key : Analysis.Elapsed.mSec
Value: 1464.
Key : Analysis.IO.Other.Mb
Value: 0
Key : Analysis.IO.Read.Mb
Value: 0
Key : Analysis.IO.Write.Mb
Value: 0
Key : Analysis.Init.CPU.mSec
Value: 202.
Key : Analysis.Init.Elapsed.mSec
Value: 2046.
Key : Analysis.Memory.CommitPeak.Mb
Value: 134.
Key : Bugcheck.Code.LegacyAPI
Value: 0x3b.
Key : Failure.Bucket
Value: AV_nt!EtwpTrackBinaryForSession
Key : Failure.Hash
Value: {0b0a6d9c-85ab-4e6c-ce3f-0441fedc0f6d}
Key : WER.OS.Branch
Value: vb_release.
Key : WER.OS.Version
Value: 10.0.19041.1
BUGCHECK_CODE: 3b.
BUGCHECK_P1: c0000005.
BUGCHECK_P2: fffff80208943796.
BUGCHECK_P3: fffff2853bdefa60.
BUGCHECK_P4: 0
FILE_IN_CAB: 060923-5156-01.dmp
CONTEXT: fffff2853bdefa60 -- (.cxr 0xfffff2853bdefa60)
rax=000000000000009a rbx=6d536d4d03040000 rcx=000000009f3f1a60
rdx=0000000000000004 rsi=ffffb88f8ef97440 rdi=000000000000009a
rip=fffff80208943796 rsp=fffff2853bdf0460 rbp=ffffb88f8ef97040
r8=000000000000006e r9=0000000000000000 r10=0000000000000000
r11=ffffca041d17abfa r12=0000000000000200 r13=fffff2853bdf04d8
r14=000000000000009a r15=ffffb88f8ef97300
iopl=0 nv up ei pl nz na po cy.
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00050207
nt!EtwpTrackBinaryForSession+0x5a:
fffff802`08943796 8b4b10 mov ecx,dword ptr [rbx+10h] ds:002b:6d536d4d`03040010=????????
Resetting default scope.
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: explorer.exe
STACK_TEXT:
fffff285`3bdf0460 fffff802`0880fec1 : ffffb88f`8ef97040 fffff285`3bdf05b0 ffffb88f`9f6b8db8 00000000`00000000 : nt!EtwpTrackBinaryForSession+0x5a
fffff285`3bdf04b0 fffff802`088054de : ffffb88f`904fe700 ffffb88f`904fe700 fffff285`3bdf07e0 ffffb88f`9f8689b0 : nt!EtwpProviderArrivalCallback+0x160129
fffff285`3bdf0730 fffff802`0866995f : 00000000`00000000 fffff802`08c19a00 ffffb88f`9f8689b0 00000000`00000000 : nt!EtwpAddRegEntryToGroup+0x19ba7e
fffff285`3bdf08b0 fffff802`0866973c : 00000000`00000000 fffff285`3bdf0b80 ffffb88f`9f8689b0 fffff802`00000000 : nt!EtwpSetProviderTraitsCommon+0x1a7
fffff285`3bdf0970 fffff802`08620fc4 : ffffb88f`9f8689b0 00000000`00000018 00000000`50777445 ffffb88f`9f8689b0 : nt!EtwpSetProviderTraitsUm+0x150
fffff285`3bdf09f0 fffff802`0840f4f8 : 00000000`0000001e 00000000`00000000 00000000`00000018 00000000`02eaf4a0 : nt!NtTraceControl+0x6b4
fffff285`3bdf0a90 00007ff8`226308d4 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x28
00000000`02eaf448 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x00007ff8`226308d4
SYMBOL_NAME: nt!EtwpTrackBinaryForSession+5a
MODULE_NAME: nt.
IMAGE_NAME: ntkrnlmp.exe
IMAGE_VERSION: 10.0.19041.2965
STACK_COMMAND: .cxr 0xfffff2853bdefa60 ; kb.
BUCKET_ID_FUNC_OFFSET: 5a.
FAILURE_BUCKET_ID: AV_nt!EtwpTrackBinaryForSession
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: vb_release.
OSPLATFORM_TYPE: x64.
OSNAME: Windows 10.
FAILURE_ID_HASH: {0b0a6d9c-85ab-4e6c-ce3f-0441fedc0f6d}
Followup: MachineOwner.
---------