*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
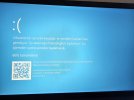
SYSTEM_SERVICE_EXCEPTION (3b)
An exception happened while executing a system service routine.
Arguments:
Arg1: 00000000c0000005, Exception code that caused the BugCheck
Arg2: fffff80367166902, Address of the instruction which caused the BugCheck
Arg3: ffffb18ae428e000, Address of the context record for the exception that caused the BugCheck
Arg4: 0000000000000000, zero.
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 937
Key : Analysis.Elapsed.mSec
Value: 12043
Key : Analysis.IO.Other.Mb
Value: 0
Key : Analysis.IO.Read.Mb
Value: 0
Key : Analysis.IO.Write.Mb
Value: 1
Key : Analysis.Init.CPU.mSec
Value: 77
Key : Analysis.Init.Elapsed.mSec
Value: 3693
Key : Analysis.Memory.CommitPeak.Mb
Value: 83
Key : Bugcheck.Code.LegacyAPI
Value: 0x3b
Key : Bugcheck.Code.TargetModel
Value: 0x3b
Key : Failure.Bucket
Value: AV_IntcUSB!unknown_function
Key : Failure.Hash
Value: {b07a1076-2d6a-a573-8c76-b0ee84d5e88c}
Key : WER.OS.Branch
Value: vb_release
Key : WER.OS.Version
Value: 10.0.19041.1
BUGCHECK_CODE: 3b
BUGCHECK_P1: c0000005
BUGCHECK_P2: fffff80367166902
BUGCHECK_P3: ffffb18ae428e000
BUGCHECK_P4: 0
FILE_IN_CAB: 041724-5843-01.dmp
CONTEXT: ffffb18ae428e000 -- (.cxr 0xffffb18ae428e000)
rax=0000000000000000 rbx=0000000000000001 rcx=ffffb18ae428e980
rdx=0000000000000000 rsi=0000000000000103 rdi=0000000000000004
rip=fffff80367166902 rsp=ffffb18ae428ea00 rbp=ffffb68c887209a0
r8=0000000000000001 r9=0000000000000058 r10=0000000000000000
r11=fffff80335000000 r12=0000000000000000 r13=ffffb68c883271d0
r14=ffffb68c7cbeab10 r15=ffffb68c7cf44590
iopl=0 nv up ei ng nz na po nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00050286
IntcUSB+0x56902:
fffff803`67166902 488b0f mov rcx,qword ptr [rdi] ds:002b:00000000`00000004=????????????????
Resetting default scope
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: svchost.exe
STACK_TEXT:
ffffb18a`e428ea00 ffffb68c`883271a8 : ffffb68c`00000000 00000000`00000000 ffffb68c`88327100 ffffb18a`00000002 : IntcUSB+0x56902
ffffb18a`e428ea08 ffffb68c`00000000 : 00000000`00000000 ffffb68c`88327100 ffffb18a`00000002 00000000`00000001 : 0xffffb68c`883271a8
ffffb18a`e428ea10 00000000`00000000 : ffffb68c`88327100 ffffb18a`00000002 00000000`00000001 00000000`00000001 : 0xffffb68c`00000000
SYMBOL_NAME: IntcUSB+56902
MODULE_NAME: IntcUSB
IMAGE_NAME: IntcUSB.sys
STACK_COMMAND: .cxr 0xffffb18ae428e000 ; kb
BUCKET_ID_FUNC_OFFSET: 56902
FAILURE_BUCKET_ID: AV_IntcUSB!unknown_function
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: vb_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {b07a1076-2d6a-a573-8c76-b0ee84d5e88c}
Followup: MachineOwner
---------