*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
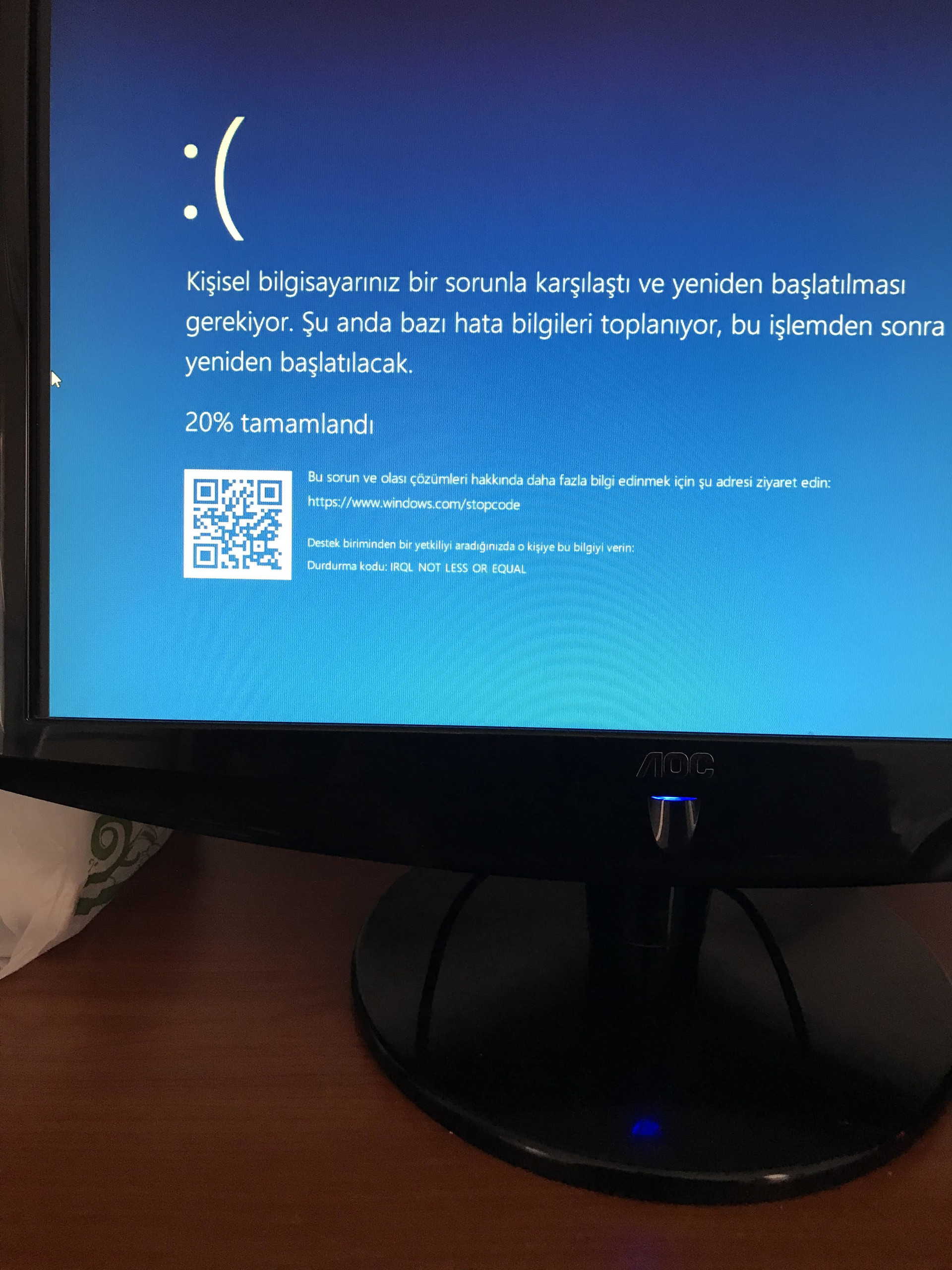
IRQL_NOT_LESS_OR_EQUAL (a)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If a kernel debugger is available get the stack backtrace.
Arguments:
Arg1: 0000000000000000, memory referenced
Arg2: 0000000000000002, IRQL
Arg3: 0000000000000000, bitfield :
bit 0 : value 0 = read operation, 1 = write operation
bit 3 : value 0 = not an execute operation, 1 = execute operation (only on chips which support this level of status)
Arg4: fffff8075b628185, address which referenced memory
Debugging Details:
------------------
KEY_VALUES_STRING: 1
PROCESSES_ANALYSIS: 1
SERVICE_ANALYSIS: 1
STACKHASH_ANALYSIS: 1
TIMELINE_ANALYSIS: 1
DUMP_CLASS: 1
DUMP_QUALIFIER: 400
BUILD_VERSION_STRING: 18362.1.amd64fre.19h1_release.190318-1202
SYSTEM_MANUFACTURER: System manufacturer
SYSTEM_PRODUCT_NAME: System Product Name
SYSTEM_SKU: SKU
SYSTEM_VERSION: System Version
BIOS_VENDOR: American Megatrends Inc.
BIOS_VERSION: 1823
BIOS_DATE: 10/15/2019
BASEBOARD_MANUFACTURER: ASUSTeK COMPUTER INC.
BASEBOARD_PRODUCT: TUF B450-PLUS GAMING
BASEBOARD_VERSION: Rev X.0x
DUMP_TYPE: 2
BUGCHECK_P1: 0
BUGCHECK_P2: 2
BUGCHECK_P3: 0
BUGCHECK_P4: fffff8075b628185
READ_ADDRESS: fffff8075bb733b8: Unable to get MiVisibleState
Unable to get NonPagedPoolStart
Unable to get NonPagedPoolEnd
Unable to get PagedPoolStart
Unable to get PagedPoolEnd
0000000000000000
CURRENT_IRQL: 2
FAULTING_IP:
nt!KiIntSteerCalculateDistribution+1a5
fffff807`5b628185 66413906 cmp word ptr [r14],ax
CPU_COUNT: c
CPU_MHZ: d42
CPU_VENDOR: AuthenticAMD
CPU_FAMILY: 17
CPU_MODEL: 8
CPU_STEPPING: 2
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: CODE_CORRUPTION
BUGCHECK_STR: AV
PROCESS_NAME: AMDRSServ.exe
ANALYSIS_SESSION_HOST: DESKTOP-18V31A3
ANALYSIS_SESSION_TIME: 11-24-2019 13:27:58.0739
ANALYSIS_VERSION: 10.0.18362.1 x86fre
DPC_STACK_BASE: FFFFFD020163EFB0
TRAP_FRAME: fffffd020163e3f0 -- (.trap 0xfffffd020163e3f0)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=0000000000000000 rbx=0000000000000000 rcx=0000000000000001
rdx=0000000000000000 rsi=0000000000000000 rdi=0000000000000000
rip=fffff8075b628185 rsp=fffffd020163e580 rbp=fffffd020163e6b0
r8=0000000000000008 r9=fffff8075b716880 r10=0000000000000001
r11=fffffd020163e6a0 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl zr na po nc
nt!KiIntSteerCalculateDistribution+0x1a5:
fffff807`5b628185 66413906 cmp word ptr [r14],ax ds:00000000`00000000=????
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff8075b7d32e9 to fffff8075b7c14e0
STACK_TEXT:
fffffd02`0163e2a8 fffff807`5b7d32e9 : 00000000`0000000a 00000000`00000000 00000000`00000002 00000000`00000000 : nt!KeBugCheckEx
fffffd02`0163e2b0 fffff807`5b7cf62b : fffffd02`017a7768 00000000`00000001 ffffb28f`851c7102 ffffb28f`851c7180 : nt!KiBugCheckDispatch+0x69
fffffd02`0163e3f0 fffff807`5b628185 : ffffb28f`8591ad40 ffffb28f`859195a0 ffffb28f`859194c0 ffffb28f`85919140 : nt!KiPageFault+0x46b
fffffd02`0163e580 fffff807`5b6273be : 00000000`00000001 0f0f0f0f`0f0f0f0f 00000000`00000002 00000000`00000002 : nt!KiIntSteerCalculateDistribution+0x1a5
fffffd02`0163e6f0 fffff807`5b704b80 : fffff807`5ba3b5c0 ffffc481`c758d180 00000000`00000000 ffffc481`c758d180 : nt!PpmParkSteerInterrupts+0x45e
fffffd02`0163ebb0 fffff807`5b66ae95 : ffffc481`c758ff80 ffffb28f`7f7f5000 ffffc481`c7592f90 ffffc481`00000002 : nt!PpmCheckRun+0x40
fffffd02`0163ec40 fffff807`5b66a4ef : 00000000`0000001c 00000000`00989680 00000000`0000cee0 00000000`000000f8 : nt!KiExecuteAllDpcs+0x305
fffffd02`0163ed80 fffff807`5b7c8525 : e5e8d233`0774c985 ffffc481`c758d180 00000000`00000000 00000180`455037f0 : nt!KiRetireDpcList+0x1ef
fffffd02`0163efb0 fffff807`5b7c8310 : ffffffff`ffffff94 fffffd02`046dfa78 00000000`00000010 00000000`00040246 : nt!KxRetireDpcList+0x5
fffffd02`046dfad0 fffff807`5b7c79e0 : 00000180`455011b0 fffffd02`046dfb80 ffffc481`c8360140 ffffb28f`8a4b4460 : nt!KiDispatchInterruptContinue
fffffd02`046dfb00 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiDpcInterrupt+0x2f0
CHKIMG_EXTENSION: !chkimg -lo 50 -d !nt
fffff8075b628240 - nt!KiIntSteerCalculateDistribution+260
[ 7d:75 ]
1 error : !nt (fffff8075b628240)
MODULE_NAME: memory_corruption
IMAGE_NAME: memory_corruption
FOLLOWUP_NAME: memory_corruption
DEBUG_FLR_IMAGE_TIMESTAMP: 0
MEMORY_CORRUPTOR: ONE_BIT
STACK_COMMAND: .thread ; .cxr ; kb
FAILURE_BUCKET_ID: MEMORY_CORRUPTION_ONE_BIT
BUCKET_ID: MEMORY_CORRUPTION_ONE_BIT
PRIMARY_PROBLEM_CLASS: MEMORY_CORRUPTION_ONE_BIT
TARGET_TIME: 2019-11-24T09:31:48.000Z
OSBUILD: 18362
OSSERVICEPACK: 476
SERVICEPACK_NUMBER: 0
OS_REVISION: 0
SUITE_MASK: 272
PRODUCT_TYPE: 1
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
OSEDITION: Windows 10 WinNt TerminalServer SingleUserTS
OS_LOCALE:
USER_LCID: 0
OSBUILD_TIMESTAMP: 2011-12-30 02:28:41
BUILDDATESTAMP_STR: 190318-1202
BUILDLAB_STR: 19h1_release
BUILDOSVER_STR: 10.0.18362.1.amd64fre.19h1_release.190318-1202
ANALYSIS_SESSION_ELAPSED_TIME: 318e
ANALYSIS_SOURCE: KM
FAILURE_ID_HASH_STRING: km:memory_corruption_one_bit
FAILURE_ID_HASH: {e3faf315-c3d0-81db-819a-6c43d23c63a7}
Followup: memory_corruption
---------