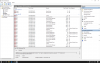
MEMORY_MANAGEMENT (1a)
# Any other values for parameter 1 must be individually examined.
Arguments:
Arg1: 0000000000041790, A page table page has been corrupted. On a 64 bit OS, parameter 2
contains the address of the PFN for the corrupted page table page.
On a 32 bit OS, parameter 2 contains a pointer to the number of used
PTEs, and parameter 3 contains the number of used PTEs.
Arg2: ffff978000ab1e00
Arg3: 00000000000000be
Arg4: 00000000000000bf
Debugging Details:
------------------
KEY_VALUES_STRING: 1
PROCESSES_ANALYSIS: 1
SERVICE_ANALYSIS: 1
STACKHASH_ANALYSIS: 1
TIMELINE_ANALYSIS: 1
DUMP_CLASS: 1
DUMP_QUALIFIER: 400
BUILD_VERSION_STRING: 18362.1.amd64fre.19h1_release.190318-1202
SYSTEM_MANUFACTURER: Gigabyte Technology Co., Ltd.
SYSTEM_PRODUCT_NAME: B450M S2H
SYSTEM_SKU: Default string
SYSTEM_VERSION: Default string
BIOS_VENDOR: American Megatrends Inc.
BIOS_VERSION: F50
BIOS_DATE: 11/27/2019
BASEBOARD_MANUFACTURER: Gigabyte Technology Co., Ltd.
BASEBOARD_PRODUCT: B450M S2H
BASEBOARD_VERSION: x.x
DUMP_TYPE: 2
BUGCHECK_P1: 41790
BUGCHECK_P2: ffff978000ab1e00
BUGCHECK_P3: be
BUGCHECK_P4: bf
BUGCHECK_STR: 0x1a_41790
CPU_COUNT: 10
CPU_MHZ: e6d
CPU_VENDOR: AuthenticAMD
CPU_FAMILY: 17
CPU_MODEL: 8
CPU_STEPPING: 2
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: WIN8_DRIVER_FAULT
PROCESS_NAME: MicrosoftEdgeCP.exe
CURRENT_IRQL: 2
ANALYSIS_SESSION_HOST: DESKTOP-18V31A3
ANALYSIS_SESSION_TIME: 02-09-2020 18:25:43.0265
ANALYSIS_VERSION: 10.0.18362.1 x86fre
LAST_CONTROL_TRANSFER: from fffff8043dbe9748 to fffff8043dbc14e0
STACK_TEXT:
ffffaf07`e282ea28 fffff804`3dbe9748 : 00000000`0000001a 00000000`00041790 ffff9780`00ab1e00 00000000`000000be : nt!KeBugCheckEx
ffffaf07`e282ea30 fffff804`3dab11f7 : 00000000`00000003 ffffaf07`e282f180 ffffaf07`e282f180 ffffaf07`e282f0d0 : nt!MiDeletePteRun+0x1d34a8
ffffaf07`e282ec50 fffff804`3daacd12 : ffffd98f`52df5580 ffff9c3f`fd86d000 00000000`00004000 00000000`00000000 : nt!MiDeleteVaTail+0x77
ffffaf07`e282ec80 fffff804`3daacea1 : ffffaf07`e282f0d0 ffff9c4e`1ffec360 00000000`00000000 0a000000`390a0867 : nt!MiWalkPageTablesRecursively+0x512
ffffaf07`e282ed40 fffff804`3daacea1 : ffffaf07`e282f0d0 ffff9c4e`270fff60 00000000`00000000 0a000000`389ee867 : nt!MiWalkPageTablesRecursively+0x6a1
ffffaf07`e282ee00 fffff804`3daacea1 : ffffaf07`e282f0d0 ffff9c4e`271387f8 ffff9c4e`00000000 0a000000`37bd9867 : nt!MiWalkPageTablesRecursively+0x6a1
ffffaf07`e282eec0 fffff804`3daac62c : ffffaf07`e282f0d0 00000000`00000000 00000000`00000000 00000000`00000000 : nt!MiWalkPageTablesRecursively+0x6a1
ffffaf07`e282ef80 fffff804`3daaaa98 : ffffaf07`e282f0d0 ffffd98f`00000002 00000000`00000001 00000000`00000000 : nt!MiWalkPageTables+0x36c
ffffaf07`e282f080 fffff804`3dab8bf0 : ffffffff`ffffffff ffffd98f`52df53f8 ffffaf07`00000001 00000000`00000000 : nt!MiDeletePagablePteRange+0x268
ffffaf07`e282f420 fffff804`3dfc7a5d : ffffd98f`52b2c080 ffffd98f`52b2c080 ffffd98f`53a88f00 ffffd98f`52df53f0 : nt!MiDeleteVad+0x860
ffffaf07`e282f5e0 fffff804`3dfd9e14 : ffffd98f`53a88f00 ffffd98f`5258a930 ffffd98f`52b2c080 00000000`00000000 : nt!MiUnmapVad+0x49
ffffaf07`e282f610 fffff804`3dfd98cf : ffffd98f`4a397840 ffffd98f`4a397840 ffffd98f`52df5080 fffff804`3de6a400 : nt!MiCleanVad+0x30
ffffaf07`e282f640 fffff804`3e038771 : ffffffff`00000000 ffffffff`ffffffff ffffaf07`e282f801 ffffd98f`52df5080 : nt!MmCleanProcessAddressSpace+0x137
ffffaf07`e282f6c0 fffff804`3e05e6d3 : ffffd98f`52df5080 ffffc309`64c48060 ffffaf07`e282f8e9 00000000`00000000 : nt!PspRundownSingleProcess+0x139
ffffaf07`e282f740 fffff804`3e0cd143 : 00000000`00000000 00000000`00000001 0000004c`f6528000 00000000`00000000 : nt!PspExitThread+0x60b
ffffaf07`e282f850 fffff804`3da3e551 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSchedulerApcTerminate+0x33
ffffaf07`e282f890 fffff804`3dbc5a60 : 00000000`00000001 ffffaf07`e282f950 00000000`00000000 00000000`00000000 : nt!KiDeliverApc+0x481
ffffaf07`e282f950 fffff804`3dbd2dbf : ffffd98f`52b2c080 0000004c`f697f318 ffffaf07`ffffffff 00000000`00001cff : nt!KiInitiateUserApc+0x70
ffffaf07`e282fa90 00007ffb`31a69a84 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceExit+0x9f
0000004c`f697f2f8 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x00007ffb`31a69a84
THREAD_SHA1_HASH_MOD_FUNC: cf5c972d8494816023066845de37f86a3bfa7253
THREAD_SHA1_HASH_MOD_FUNC_OFFSET: 017204202c55dcdc874341af0c5057e43ce16f6b
THREAD_SHA1_HASH_MOD: a9ca63faa9e43cc61ef524ad38163e6a9ae5c358
FOLLOWUP_IP:
nt!MiDeletePteRun+1d34a8
fffff804`3dbe9748 cc int 3
FAULT_INSTR_CODE: 4d8d48cc
SYMBOL_STACK_INDEX: 1
SYMBOL_NAME: nt!MiDeletePteRun+1d34a8
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: nt
DEBUG_FLR_IMAGE_TIMESTAMP: 4f6eba0
IMAGE_VERSION: 10.0.18362.592
STACK_COMMAND: .thread ; .cxr ; kb
IMAGE_NAME: memory_corruption
BUCKET_ID_FUNC_OFFSET: 1d34a8
FAILURE_BUCKET_ID: 0x1a_41790_nt!MiDeletePteRun
BUCKET_ID: 0x1a_41790_nt!MiDeletePteRun
PRIMARY_PROBLEM_CLASS: 0x1a_41790_nt!MiDeletePteRun
TARGET_TIME: 2020-02-09T01:09:03.000Z
OSBUILD: 18362
OSSERVICEPACK: 592
SERVICEPACK_NUMBER: 0
OS_REVISION: 0
SUITE_MASK: 272
PRODUCT_TYPE: 1
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
OSEDITION: Windows 10 WinNt TerminalServer SingleUserTS
OS_LOCALE:
USER_LCID: 0
OSBUILD_TIMESTAMP: 1972-08-22 03:24:00
BUILDDATESTAMP_STR: 190318-1202
BUILDLAB_STR: 19h1_release
BUILDOSVER_STR: 10.0.18362.1.amd64fre.19h1_release.190318-1202
ANALYSIS_SESSION_ELAPSED_TIME: 16e5
ANALYSIS_SOURCE: KM
FAILURE_ID_HASH_STRING: km:0x1a_41790_nt!mideletepterun
FAILURE_ID_HASH: {27ce5d5a-97b1-faf0-183f-c86809269d56}
Followup: MachineOwner
---------
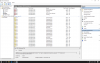
PFN_LIST_CORRUPT (4e)
Typically caused by drivers passing bad memory descriptor lists (ie: calling
MmUnlockPages twice with the same list, etc). If a kernel debugger is
available get the stack trace.
Arguments:
Arg1: 0000000000000099, A PTE or PFN is corrupt
Arg2: 000000000016399b, page frame number
Arg3: 0000000000000003, current page state
Arg4: 0e0000000009de10, 0
Debugging Details:
------------------
KEY_VALUES_STRING: 1
PROCESSES_ANALYSIS: 1
SERVICE_ANALYSIS: 1
STACKHASH_ANALYSIS: 1
TIMELINE_ANALYSIS: 1
DUMP_CLASS: 1
DUMP_QUALIFIER: 400
BUILD_VERSION_STRING: 18362.1.amd64fre.19h1_release.190318-1202
DUMP_TYPE: 2
BUGCHECK_P1: 99
BUGCHECK_P2: 16399b
BUGCHECK_P3: 3
BUGCHECK_P4: e0000000009de10
BUGCHECK_STR: 0x4E_99
CPU_COUNT: 10
CPU_MHZ: e6d
CPU_VENDOR: AuthenticAMD
CPU_FAMILY: 17
CPU_MODEL: 8
CPU_STEPPING: 2
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: WIN8_DRIVER_FAULT
PROCESS_NAME: LeagueClientUxRender.exe
CURRENT_IRQL: 2
ANALYSIS_SESSION_HOST: DESKTOP-18V31A3
ANALYSIS_SESSION_TIME: 02-09-2020 18:25:39.0917
ANALYSIS_VERSION: 10.0.18362.1 x86fre
LAST_CONTROL_TRANSFER: from fffff8034b3e970e to fffff8034b3c14e0
STACK_TEXT:
ffff978a`765f6a98 fffff803`4b3e970e : 00000000`0000004e 00000000`00000099 00000000`0016399b 00000000`00000003 : nt!KeBugCheckEx
ffff978a`765f6aa0 fffff803`4b2b11f7 : 00000000`00000003 ffff978a`765f71f0 ffff978a`765f71f0 ffff978a`765f7140 : nt!MiDeletePteRun+0x1d346e
ffff978a`765f6cc0 fffff803`4b2acd12 : ffffaa81`53cb6580 ffff9400`00111000 00000000`00004000 00000000`00000000 : nt!MiDeleteVaTail+0x77
ffff978a`765f6cf0 fffff803`4b2acea1 : ffff978a`765f7140 ffff944a`00000880 00000000`00000000 0a000000`785ab867 : nt!MiWalkPageTablesRecursively+0x512
ffff978a`765f6db0 fffff803`4b2acea1 : ffff978a`765f7140 ffff944a`25000000 00000000`00000000 0a000001`186ee867 : nt!MiWalkPageTablesRecursively+0x6a1
ffff978a`765f6e70 fffff803`4b2acea1 : ffff978a`765f7140 ffff944a`25128000 ffff944a`00000000 0a000000`5eced867 : nt!MiWalkPageTablesRecursively+0x6a1
ffff978a`765f6f30 fffff803`4b2ac62c : ffff978a`765f7140 ffff944a`25128940 ffff978a`00000000 ffff978a`765f70b9 : nt!MiWalkPageTablesRecursively+0x6a1
ffff978a`765f6ff0 fffff803`4b2aaa98 : ffff978a`765f7140 ffffaa81`00000002 00000000`00000001 00000000`00000000 : nt!MiWalkPageTables+0x36c
ffff978a`765f70f0 fffff803`4b2b8bf0 : ffffffff`ffffffff ffffaa81`53cb63f8 00000000`00000001 00000000`00000000 : nt!MiDeletePagablePteRange+0x268
ffff978a`765f7490 fffff803`4b7c7a5d : ffffaa81`53e6b080 ffffaa81`53e6b080 ffffaa81`527602c0 ffffaa81`53cb63f0 : nt!MiDeleteVad+0x860
ffff978a`765f7650 fffff803`4b7d9e14 : ffffaa81`527602c0 ffffaa81`50d59980 ffffaa81`53e6b080 00000000`00000000 : nt!MiUnmapVad+0x49
ffff978a`765f7680 fffff803`4b7d98cf : ffffaa81`52b47460 ffffaa81`52b47460 ffffaa81`53cb6080 fffff803`4b66a400 : nt!MiCleanVad+0x30
ffff978a`765f76b0 fffff803`4b838771 : ffffffff`00000000 ffffffff`ffffffff ffff978a`765f7901 ffffaa81`53cb6080 : nt!MmCleanProcessAddressSpace+0x137
ffff978a`765f7730 fffff803`4b85e6d3 : ffffaa81`53cb6080 ffffba81`34873060 ffff978a`765f7959 00000000`00000000 : nt!PspRundownSingleProcess+0x139
ffff978a`765f77b0 fffff803`4b8cd143 : 00000000`00000000 ffffaa81`53e6b001 00000000`003c6000 00000000`0000ffff : nt!PspExitThread+0x60b
ffff978a`765f78c0 fffff803`4b23e551 : ffffaa81`53e6b180 00000000`00000001 00000000`00000000 00000000`00000100 : nt!KiSchedulerApcTerminate+0x33
ffff978a`765f7900 fffff803`4b3c5a60 : ffffaa81`53e6b001 ffff978a`765f79c0 ffffaa81`53e6b080 fffff803`00000000 : nt!KiDeliverApc+0x481
ffff978a`765f79c0 fffff803`4b3d2dbf : ffffaa81`53e6b080 00000000`00000000 00000000`00000000 ffffaa81`53116260 : nt!KiInitiateUserApc+0x70
ffff978a`765f7b00 00000000`77db1cbc : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceExit+0x9f
00000000`083fec08 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x77db1cbc
THREAD_SHA1_HASH_MOD_FUNC: cf5c972d8494816023066845de37f86a3bfa7253
THREAD_SHA1_HASH_MOD_FUNC_OFFSET: 7eac0e25ab0a3c7bf17d78cad802b63736e6c240
THREAD_SHA1_HASH_MOD: a9ca63faa9e43cc61ef524ad38163e6a9ae5c358
FOLLOWUP_IP:
nt!MiDeletePteRun+1d346e
fffff803`4b3e970e cc int 3
FAULT_INSTR_CODE: 448b49cc
SYMBOL_STACK_INDEX: 1
SYMBOL_NAME: nt!MiDeletePteRun+1d346e
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: nt
DEBUG_FLR_IMAGE_TIMESTAMP: 4f6eba0
IMAGE_VERSION: 10.0.18362.592
STACK_COMMAND: .thread ; .cxr ; kb
IMAGE_NAME: memory_corruption
BUCKET_ID_FUNC_OFFSET: 1d346e
FAILURE_BUCKET_ID: 0x4E_99_nt!MiDeletePteRun
BUCKET_ID: 0x4E_99_nt!MiDeletePteRun
PRIMARY_PROBLEM_CLASS: 0x4E_99_nt!MiDeletePteRun
TARGET_TIME: 2020-02-08T23:47:49.000Z
OSBUILD: 18362
OSSERVICEPACK: 592
SERVICEPACK_NUMBER: 0
OS_REVISION: 0
SUITE_MASK: 272
PRODUCT_TYPE: 1
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
OSEDITION: Windows 10 WinNt TerminalServer SingleUserTS
OS_LOCALE:
USER_LCID: 0
OSBUILD_TIMESTAMP: 1972-08-22 03:24:00
BUILDDATESTAMP_STR: 190318-1202
BUILDLAB_STR: 19h1_release
BUILDOSVER_STR: 10.0.18362.1.amd64fre.19h1_release.190318-1202
ANALYSIS_SESSION_ELAPSED_TIME: 2a7c
ANALYSIS_SOURCE: KM
FAILURE_ID_HASH_STRING: km:0x4e_99_nt!mideletepterun
FAILURE_ID_HASH: {826a8dfe-b402-47c5-bb75-e9ab5230289f}
Followup: MachineOwner
---------
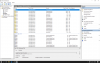
MEMORY_MANAGEMENT (1a)
# Any other values for parameter 1 must be individually examined.
Arguments:
Arg1: 0000000000041201, The subtype of the bugcheck.
Arg2: ffff948149b22df0
Arg3: 810000002145a847
Arg4: ffff9b8148c9a100
Debugging Details:
------------------
KEY_VALUES_STRING: 1
PROCESSES_ANALYSIS: 1
SERVICE_ANALYSIS: 1
STACKHASH_ANALYSIS: 1
TIMELINE_ANALYSIS: 1
DUMP_CLASS: 1
DUMP_QUALIFIER: 400
BUILD_VERSION_STRING: 18362.1.amd64fre.19h1_release.190318-1202
DUMP_TYPE: 2
BUGCHECK_P1: 41201
BUGCHECK_P2: ffff948149b22df0
BUGCHECK_P3: 810000002145a847
BUGCHECK_P4: ffff9b8148c9a100
BUGCHECK_STR: 0x1a_41201
CPU_COUNT: 10
CPU_MHZ: e6d
CPU_VENDOR: AuthenticAMD
CPU_FAMILY: 17
CPU_MODEL: 8
CPU_STEPPING: 2
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: WIN8_DRIVER_FAULT
PROCESS_NAME: svchost.exe
CURRENT_IRQL: 2
ANALYSIS_SESSION_HOST: DESKTOP-18V31A3
ANALYSIS_SESSION_TIME: 02-09-2020 18:25:37.0840
ANALYSIS_VERSION: 10.0.18362.1 x86fre
LAST_CONTROL_TRANSFER: from fffff8004d20ab7c to fffff8004d1c14e0
STACK_TEXT:
ffffbb8a`d03db548 fffff800`4d20ab7c : 00000000`0000001a 00000000`00041201 ffff9481`49b22df0 81000000`2145a847 : nt!KeBugCheckEx
ffffbb8a`d03db550 fffff800`4d06ef41 : ffff9481`49b22df8 81000000`2145a847 00000293`00000002 ffff94ca`40a4d910 : nt!MiGetPageProtection+0x19c6fc
ffffbb8a`d03db5c0 fffff800`4d100df0 : 00000000`00000000 00000000`00000000 9b8146f6`30507849 00000000`001fffff : nt!MiQueryAddressState+0x5c1
ffffbb8a`d03db7e0 fffff800`4d659787 : ffffbb8a`d03dbb80 00000293`645b7000 ffffbb8a`00000000 000000f5`00000001 : nt!MiQueryAddressSpan+0x140
ffffbb8a`d03db8a0 fffff800`4d659225 : 00000201`81a60080 fffff800`4d622a9b ffff9b81`4961c080 000000f5`e6f97bb8 : nt!MmQueryVirtualMemory+0x557
ffffbb8a`d03dba40 fffff800`4d1d2d18 : 00000000`00000000 00000000`00000000 00000000`00000000 000000f5`e6f978c8 : nt!NtQueryVirtualMemory+0x25
ffffbb8a`d03dba90 00007ff8`2aafc524 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x28
000000f5`e6f97ca8 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x00007ff8`2aafc524
THREAD_SHA1_HASH_MOD_FUNC: daeab5d68ba3ecb3234b5b8938d47aee75235996
THREAD_SHA1_HASH_MOD_FUNC_OFFSET: c56f3dafc6ff4a7d1f1b3184dff87764b5fb1880
THREAD_SHA1_HASH_MOD: 30a3e915496deaace47137d5b90c3ecc03746bf6
FOLLOWUP_IP:
nt!MiGetPageProtection+19c6fc
fffff800`4d20ab7c cc int 3
FAULT_INSTR_CODE: d8b48cc
SYMBOL_STACK_INDEX: 1
SYMBOL_NAME: nt!MiGetPageProtection+19c6fc
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: nt
DEBUG_FLR_IMAGE_TIMESTAMP: 4f6eba0
IMAGE_VERSION: 10.0.18362.592
STACK_COMMAND: .thread ; .cxr ; kb
IMAGE_NAME: memory_corruption
BUCKET_ID_FUNC_OFFSET: 19c6fc
FAILURE_BUCKET_ID: 0x1a_41201_nt!MiGetPageProtection
BUCKET_ID: 0x1a_41201_nt!MiGetPageProtection
PRIMARY_PROBLEM_CLASS: 0x1a_41201_nt!MiGetPageProtection
TARGET_TIME: 2020-02-08T21:41:50.000Z
OSBUILD: 18362
OSSERVICEPACK: 592
SERVICEPACK_NUMBER: 0
OS_REVISION: 0
SUITE_MASK: 272
PRODUCT_TYPE: 1
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
OSEDITION: Windows 10 WinNt TerminalServer SingleUserTS
OS_LOCALE:
USER_LCID: 0
OSBUILD_TIMESTAMP: 1972-08-22 03:24:00
BUILDDATESTAMP_STR: 190318-1202
BUILDLAB_STR: 19h1_release
BUILDOSVER_STR: 10.0.18362.1.amd64fre.19h1_release.190318-1202
ANALYSIS_SESSION_ELAPSED_TIME: 3146
ANALYSIS_SOURCE: KM
FAILURE_ID_HASH_STRING: km:0x1a_41201_nt!migetpageprotection
FAILURE_ID_HASH: {c1fe3b27-3ba8-d99e-656f-85f3d58dc669}
Followup: MachineOwner
---------