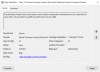
SYSTEM_SERVICE_EXCEPTION (3b)
An exception happened while executing a system service routine.
Arguments:
Arg1: 00000000c0000005, Exception code that caused the bugcheck
Arg2: fffff80247c25de0, Address of the instruction which caused the bugcheck
Arg3: ffffe90d9ee5e4c0, Address of the context record for the exception that caused the bugcheck
Arg4: 0000000000000000, zero.
Debugging Details:
------------------
Page 258e08 not present in the dump file. Type ".hh dbgerr004" for details
Page 258e08 not present in the dump file. Type ".hh dbgerr004" for details
KEY_VALUES_STRING: 1
PROCESSES_ANALYSIS: 1
SERVICE_ANALYSIS: 1
STACKHASH_ANALYSIS: 1
TIMELINE_ANALYSIS: 1
DUMP_CLASS: 1
DUMP_QUALIFIER: 401
BUILD_VERSION_STRING: 19041.1.amd64fre.vb_release.191206-1406
SYSTEM_MANUFACTURER: MONSTER
SYSTEM_PRODUCT_NAME: ABRA A5 V13.4
SYSTEM_SKU: 0001
SYSTEM_VERSION: Standard
BIOS_VENDOR: American Megatrends Inc.
BIOS_VERSION: N.1.10
BIOS_DATE: 01/23/2019
BASEBOARD_MANUFACTURER: Standard
BASEBOARD_PRODUCT: Standard
BASEBOARD_VERSION: Standard
DUMP_TYPE: 1
BUGCHECK_P1: c0000005
BUGCHECK_P2: fffff80247c25de0
BUGCHECK_P3: ffffe90d9ee5e4c0
BUGCHECK_P4: 0
EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - <Unable to get error code text>
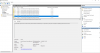
FAULTING_IP:
nt!MmGetSessionIdEx+0
fffff802`47c25de0 488b8158050000 mov rax,qword ptr [rcx+558h]
CONTEXT: ffffe90d9ee5e4c0 -- (.cxr 0xffffe90d9ee5e4c0)
rax=0000000000000000 rbx=ffff9a0351b94ca0 rcx=ff9a035eba22c000
rdx=00000000000012cd rsi=0000000000000000 rdi=0000000000000000
rip=fffff80247c25de0 rsp=ffffe90d9ee5eec8 rbp=ff9a035eba22c000
r8=0000000000000960 r9=0000000000000000 r10=fffff80247cf60c0
r11=0000000000000008 r12=0000000000000001 r13=0000000000000006
r14=0000000000000002 r15=ffff9a0354efe058
iopl=0 nv up ei ng nz na pe nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00050282
nt!MmGetSessionIdEx:
fffff802`47c25de0 488b8158050000 mov rax,qword ptr [rcx+558h] ds:002b:ff9a035e`ba22c558=????????????????
Resetting default scope
BUGCHECK_STR: 0x3B_c0000005
CPU_COUNT: c
CPU_MHZ: 8a0
CPU_VENDOR: GenuineIntel
CPU_FAMILY: 6
CPU_MODEL: 9e
CPU_STEPPING: a
CPU_MICROCODE: 6,9e,a,0 (F,M,S,R) SIG: B4'00000000 (cache) B4'00000000 (init)
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
DEFAULT_BUCKET_ID: CODE_CORRUPTION
PROCESS_NAME: Battle.net.exe
CURRENT_IRQL: 0
ANALYSIS_SESSION_HOST: DESKTOP-JC78BRD
ANALYSIS_SESSION_TIME: 06-11-2020 18:05:54.0645
ANALYSIS_VERSION: 10.0.18362.1 amd64fre
LAST_CONTROL_TRANSFER: from fffff80247cf60c9 to fffff80247c25de0
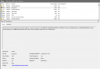
STACK_TEXT:
ffffe90d`9ee5eec8 fffff802`47cf60c9 : ffff9a03`54efe058 00000000`00000002 00000000`00000006 00000000`00000001 : nt!MmGetSessionIdEx
ffffe90d`9ee5eed0 fffff802`4aaaf7c9 : ffff9a03`51b94ca0 00000000`00000000 00000000`00000000 ffffab01`46cdb740 : nt!PsGetProcessSessionId+0x9
ffffe90d`9ee5ef00 fffff802`4aa82018 : ffff9a03`54efe058 ffffe90d`9ee5efe0 00000000`00000001 ffff9a03`5eba22c0 : tcpip!WfpAleEndpointCreationHandler+0x269
ffffe90d`9ee5ef70 fffff802`4aa81f17 : ffff9a03`3b6e40c0 00000000`00000000 ffff9a03`5eba22c0 ffff9a03`54efe010 : tcpip!TcpCreateEndpointWorkQueueRoutine+0x98
ffffe90d`9ee5f000 fffff802`4aa81b68 : 00000000`00000000 ffff9a03`613a48b0 ffff9a03`337dabc8 ffff9a03`337daa20 : tcpip!TcpCreateEndpoint+0x3a3
ffffe90d`9ee5f100 fffff802`5d91259c : 00000000`00000000 00000000`00000000 ffffe90d`9ee5f230 01000000`00100000 : tcpip!TcpTlProviderEndpoint+0x38
ffffe90d`9ee5f150 fffff802`5d8f26e3 : ffff9a03`613a48b0 00000000`00000001 ffffe90d`9ee5f2d0 00000000`00000000 : afd!AfdTLCreateEndpoint+0x94
ffffe90d`9ee5f1d0 fffff802`5d90fb8f : 00000000`00000000 ffff9a03`4dcb5218 ffff9a03`613a48b0 ffffe90d`9ee5f368 : afd!AfdCreate+0x2fb
ffffe90d`9ee5f320 fffff802`47c46d25 : ffff9a03`4dcb5218 ffffe90d`9ee5f660 ffff9a03`4dcb5180 ffff9a03`61053ae0 : afd!AfdDispatch+0x5f
ffffe90d`9ee5f360 fffff802`47c48314 : 00000000`00000003 ffff9a03`391cdb00 00000000`6d4e6f49 fffff802`47c47f43 : nt!IofCallDriver+0x55
ffffe90d`9ee5f3a0 fffff802`4800f75c : ffffe90d`9ee5f660 ffff9a03`4dcb5218 ffff9a03`4dcb5180 00000000`00000000 : nt!IoCallDriverWithTracing+0x34
ffffe90d`9ee5f3f0 fffff802`47ff554e : ffff9a03`391cdb00 00000000`00000000 ffff9a03`60cf6010 00000000`00000001 : nt!IopParseDevice+0x6ac
ffffe90d`9ee5f560 fffff802`47ff0faa : ffff9a03`60cf6000 ffffe90d`9ee5f7c8 00000000`00000042 ffff9a03`33159640 : nt!ObpLookupObjectName+0x3fe
ffffe90d`9ee5f730 fffff802`4808f3df : ffff9a03`00000000 00000000`04e0ecb0 00000000`04e0e3f8 00000000`00000001 : nt!ObOpenObjectByNameEx+0x1fa
ffffe90d`9ee5f860 fffff802`4808efb9 : 00000000`04e0e3e0 fffff802`47ff8f91 00000000`04e0ecb0 00000000`04e0e3f8 : nt!IopCreateFile+0x40f
ffffe90d`9ee5f900 fffff802`47def375 : 00000000`00000000 00000000`77a64630 00000000`00000102 ffff9a03`4958b660 : nt!NtCreateFile+0x79
ffffe90d`9ee5f990 00007ff8`0b68b834 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x25
00000000`04e0e368 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x00007ff8`0b68b834
CHKIMG_EXTENSION: !chkimg -lo 50 -d !tcpip
fffff8024aa82010 - tcpip!TcpCreateEndpointWorkQueueRoutine+90
[ 20:21 ]
1 error : !tcpip (fffff8024aa82010)
MODULE_NAME: memory_corruption
IMAGE_NAME: memory_corruption
FOLLOWUP_NAME: memory_corruption
DEBUG_FLR_IMAGE_TIMESTAMP: 0
MEMORY_CORRUPTOR: ONE_BIT
STACK_COMMAND: .cxr 0xffffe90d9ee5e4c0 ; kb
FAILURE_BUCKET_ID: MEMORY_CORRUPTION_ONE_BIT
BUCKET_ID: MEMORY_CORRUPTION_ONE_BIT
PRIMARY_PROBLEM_CLASS: MEMORY_CORRUPTION_ONE_BIT
TARGET_TIME: 2020-06-11T14:14:14.000Z
OSBUILD: 19041
OSSERVICEPACK: 0
SERVICEPACK_NUMBER: 0
OS_REVISION: 0
SUITE_MASK: 272
PRODUCT_TYPE: 1
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
OSEDITION: Windows 10 WinNt TerminalServer SingleUserTS
OS_LOCALE:
USER_LCID: 0
OSBUILD_TIMESTAMP: unknown_date
BUILDDATESTAMP_STR: 191206-1406
BUILDLAB_STR: vb_release
BUILDOSVER_STR: 10.0.19041.1.amd64fre.vb_release.191206-1406
ANALYSIS_SESSION_ELAPSED_TIME: e820
ANALYSIS_SOURCE: KM
FAILURE_ID_HASH_STRING: km:memory_corruption_one_bit
FAILURE_ID_HASH: {e3faf315-c3d0-81db-819a-6c43d23c63a7}
Followup: memory_corruption
---------