darkVE
Kilopat
- Katılım
- 3 Mart 2017
- Mesajlar
- 115
- Çözümler
- 2
16 GB RAM ile birlikte bilgisayarımı aldım ve sonrasında 16 GB RAM eklemek istedim fakat RAM'leri takıp XMP açtığımda, bilgisayarda belli bir süre geçirdikten sonra mavi ekran hatası alıyorum. Aynı marka aynı model sadece üreticileri farklı 3200MHz çıkabilecek RAM'i 3000MHz çıkartıyorum yine de mavi ekran alıyorum.
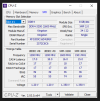
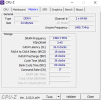
8 GB Kingston Fury DDR4 3200MHz KF432C16BB/8 4x8G
Samsung SSD 970 EVO 250GB
ASUS DUAL-RTX3070-O8G-V2 8 GB GDDR6 HDMI DP 256Bit
ASUS Prime B550M-K DDR4 4600(O.C)/2133MHz mATXAM4
AMD Ryzen 5 5600 3.5 GHz 35MB AM4
Windows 10 Pro 21H2.
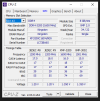
8 GB Kingston Fury DDR4 3200MHz KF432C16BB/8 4x8G
Samsung SSD 970 EVO 250GB
ASUS DUAL-RTX3070-O8G-V2 8 GB GDDR6 HDMI DP 256Bit
ASUS Prime B550M-K DDR4 4600(O.C)/2133MHz mATXAM4
AMD Ryzen 5 5600 3.5 GHz 35MB AM4
Windows 10 Pro 21H2.
Microsoft (R) Windows Debugger Version 10.0.25200.1003 AMD64
Copyright (C) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Windows\Minidump\121722-7265-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
************* Path validation summary **************
Response Time (ms) Location
Deferred srv*
Symbol Search path is: Srv*
Executable Search path is:
Windows 10 Kernel Version 19041 MP (12 procs) Free X64
Product: WinNt, Suite: TerminalServer SingleUserTS
Edition Build lab: 19041.1.AMD64fre. Vb_release. 191206-1406
Machine Name:
Kernel base = 0xfffff800`82e00000 PsLoadedModuleList = 0xfffff800`83a2a290
Debug session time: Sat Dec 17 15:03:33.455 2022 (UTC + 3:00)
System Uptime: 0 days 0:18:45.061
Loading Kernel Symbols
Loading User Symbols
Loading unloaded module list
For analysis of this file, run! Analyze -v
NT! KeBugCheckEx:
Fffff800'831F92a0 48894C2408 mov qword ptr [rsp+8],rcx SS:0018:ffff828D'703162F0 = 000000000000003B
8: Kd>!analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
SYSTEM_SERVICE_EXCEPTION (3b)
An exception happened while executing a System service routine.
Arguments:
Arg1: 00000000C0000005, Exception code that caused the BugCheck
Arg2: FffFF800830F50EA, Address of the instruction which caused the BugCheck
Arg3: FfFF828D70316BF0, Address of the context record for the exception that caused the BugCheck
Arg4: 0000000000000000, Zero.
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key: Analysis. CPU. MSec
Value: 2514
Key: Analysis. DebugAnalysisManager
Value: Create
Key: Analysis. Elapsed. MSec
Value: 17808
Key: Analysis. IO. Other. MB
Value: 21
Key: Analysis. IO. Read. MB
Value: 0
Key: Analysis. IO. Write. MB
Value: 25
Key: Analysis. Init. CPU. MSec
Value: 499
Key: Analysis. Init. Elapsed. MSec
Value: 37445
Key: Analysis. Memory.commitPeak. MB
Value: 82
Key: Bugcheck. Code. DumpHeader
Value: 0x3b
Key: Bugcheck. Code. Register
Value: 0x3b
Key: WER. OS. Branch
Value: Vb_release
Key: WER. OS. Timestamp
Value: 2019-12-06T14:06:00Z
Key: WER. OS. Version
Value: 10.0.19041.1
FILE_IN_CAB: 121722-7265-01.dmp
BUGCHECK_CODE: 3B
BUGCHECK_P1: C0000005
BUGCHECK_P2: FffFF800830F50EA
BUGCHECK_P3: FfFF828D70316BF0
BUGCHECK_P4: 0
CONTEXT: FfFF828D70316BF0 -- (.cxr 0xffff828d70316bf0)
Rax = 00000000000000F2 rbx = 0000000000007bED rcx = 0000000000000000
Rdx = 0000000000006B8D rsi = fffFA68C69D9C000 rdi = ffffffffffffffff
Rip = fffFF800830F50EA rsp = ffFF828D703175F0 rbp = 0000000000000000
R8 = 0000000000006823 R9 = 0000000000000000 R10 = fffFA68C69Da93b0
R11 = 0000000000000FFF R12 = 0000000000000001 R13 = 00000000ffffffff
R14 = fffFA68C57010340 R15 = 0000000000000000
İopl = 0 nv up ei pl nz AC pe cy
CS = 0010 SS = 0018 DS = 002b es = 002b fs = 0053 GS = 002b efl = 00050213
NT! RtlpHpLfhSubsegmentFreeBlock+0x8a:
Fffff800'830F50EA 8B4148 mov eax, dword ptr [rcx+48h] DS:002b:00000000'00000048=?
Resetting default scope
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: Discord.exe
STACK_TEXT:
Ffff828D'703175F0 fffff800'830242B2: Ffffa68C'57010340 00000000'000000FF ffffa68C'674ec7C0 ffffa68C'00000000: NT! RtlpHpLfhSubsegmentFreeBlock+0x8a
Ffff828D'703176A0 fffff800'837b5019: 00000000'00000000 00000000'00000000 00000000'00000000 01000000'00100000: NT! ExFreeHeapPool+0x362
Ffff828D'70317780 fffff800'830dcf84: 00000000'00000000 ffffa68C'69da93C0 ffffa68C'69da93C0 01000000'00100000: NT! ExFreePool+0x9
Ffff828D'703177B0 fffff800'830CF2a4: 00000000'00000001 ffffca0a'00000001 ffffa68C'00000001 ffffa68C'00000000: NT! MiFinishVadDeletion+0x554
Ffff828D'70317850 fffff800'83491749: 00000000'00000000 00000000'00000000 00000000'00000000 00000000'00000000: NT! MiDeleteVad+0xae4
Ffff828D'70317960 fffff800'83491522: Ffffa68C'69da93C0 00000000'00000000 ffffa68C'674ec080 00000000'00000000: NT! MiUnmapVad+0x49
Ffff828D'70317990 fffff800'83491399: 00000000'5B2aaeb4 00000000'5B23CA40 00000000'00000098 00000000'00000000: NT! MiUnmapViewOfSection+0x152
Ffff828D'70317A70 fffff800'8320CAF8: Ffffa68C'65ad52C0 00007FFF'86ef7F01 ffff828D'70317AD8 ffffa68C'674ec080: NT! NtUnmapViewOfSectionEx+0x99
Ffff828D'70317AC0 00007FFF'87C50a34: 00000000'00000000 00000000'00000000 00000000'00000000 00000000'00000000: NT! KiSystemServiceCopyEnd+0x28
00000000'0F7FE648 00000000'00000000: 00000000'00000000 00000000'00000000 00000000'00000000 00000000'00000000: 0x00007fff`87c50a34
SYMBOL_NAME: NT! RtlpHpLfhSubsegmentFreeBlock+8a
MODULE_NAME: NT
IMAGE_NAME: ntkrnlmp.exe
IMAGE_VERSION: 10.0.19041.2364
STACK_COMMAND: Cxr 0xffff828d70316bf0; KB
BUCKET_ID_FUNC_OFFSET: 8A
FAILURE_BUCKET_ID: AV_nt! RtlpHpLfhSubsegmentFreeBlock
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: Vb_release
OSPLATFORM_TYPE: X64
OSNAME: Windows 10
FAILURE_ID_HASH: {0C706EF1-02BF-81B2-1C3A-D61BE746C53F}
Followup: MachineOwner
---------
Copyright (C) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Windows\Minidump\121722-7265-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
************* Path validation summary **************
Response Time (ms) Location
Deferred srv*
Symbol Search path is: Srv*
Executable Search path is:
Windows 10 Kernel Version 19041 MP (12 procs) Free X64
Product: WinNt, Suite: TerminalServer SingleUserTS
Edition Build lab: 19041.1.AMD64fre. Vb_release. 191206-1406
Machine Name:
Kernel base = 0xfffff800`82e00000 PsLoadedModuleList = 0xfffff800`83a2a290
Debug session time: Sat Dec 17 15:03:33.455 2022 (UTC + 3:00)
System Uptime: 0 days 0:18:45.061
Loading Kernel Symbols
Loading User Symbols
Loading unloaded module list
For analysis of this file, run! Analyze -v
NT! KeBugCheckEx:
Fffff800'831F92a0 48894C2408 mov qword ptr [rsp+8],rcx SS:0018:ffff828D'703162F0 = 000000000000003B
8: Kd>!analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
SYSTEM_SERVICE_EXCEPTION (3b)
An exception happened while executing a System service routine.
Arguments:
Arg1: 00000000C0000005, Exception code that caused the BugCheck
Arg2: FffFF800830F50EA, Address of the instruction which caused the BugCheck
Arg3: FfFF828D70316BF0, Address of the context record for the exception that caused the BugCheck
Arg4: 0000000000000000, Zero.
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key: Analysis. CPU. MSec
Value: 2514
Key: Analysis. DebugAnalysisManager
Value: Create
Key: Analysis. Elapsed. MSec
Value: 17808
Key: Analysis. IO. Other. MB
Value: 21
Key: Analysis. IO. Read. MB
Value: 0
Key: Analysis. IO. Write. MB
Value: 25
Key: Analysis. Init. CPU. MSec
Value: 499
Key: Analysis. Init. Elapsed. MSec
Value: 37445
Key: Analysis. Memory.commitPeak. MB
Value: 82
Key: Bugcheck. Code. DumpHeader
Value: 0x3b
Key: Bugcheck. Code. Register
Value: 0x3b
Key: WER. OS. Branch
Value: Vb_release
Key: WER. OS. Timestamp
Value: 2019-12-06T14:06:00Z
Key: WER. OS. Version
Value: 10.0.19041.1
FILE_IN_CAB: 121722-7265-01.dmp
BUGCHECK_CODE: 3B
BUGCHECK_P1: C0000005
BUGCHECK_P2: FffFF800830F50EA
BUGCHECK_P3: FfFF828D70316BF0
BUGCHECK_P4: 0
CONTEXT: FfFF828D70316BF0 -- (.cxr 0xffff828d70316bf0)
Rax = 00000000000000F2 rbx = 0000000000007bED rcx = 0000000000000000
Rdx = 0000000000006B8D rsi = fffFA68C69D9C000 rdi = ffffffffffffffff
Rip = fffFF800830F50EA rsp = ffFF828D703175F0 rbp = 0000000000000000
R8 = 0000000000006823 R9 = 0000000000000000 R10 = fffFA68C69Da93b0
R11 = 0000000000000FFF R12 = 0000000000000001 R13 = 00000000ffffffff
R14 = fffFA68C57010340 R15 = 0000000000000000
İopl = 0 nv up ei pl nz AC pe cy
CS = 0010 SS = 0018 DS = 002b es = 002b fs = 0053 GS = 002b efl = 00050213
NT! RtlpHpLfhSubsegmentFreeBlock+0x8a:
Fffff800'830F50EA 8B4148 mov eax, dword ptr [rcx+48h] DS:002b:00000000'00000048=?
Resetting default scope
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: Discord.exe
STACK_TEXT:
Ffff828D'703175F0 fffff800'830242B2: Ffffa68C'57010340 00000000'000000FF ffffa68C'674ec7C0 ffffa68C'00000000: NT! RtlpHpLfhSubsegmentFreeBlock+0x8a
Ffff828D'703176A0 fffff800'837b5019: 00000000'00000000 00000000'00000000 00000000'00000000 01000000'00100000: NT! ExFreeHeapPool+0x362
Ffff828D'70317780 fffff800'830dcf84: 00000000'00000000 ffffa68C'69da93C0 ffffa68C'69da93C0 01000000'00100000: NT! ExFreePool+0x9
Ffff828D'703177B0 fffff800'830CF2a4: 00000000'00000001 ffffca0a'00000001 ffffa68C'00000001 ffffa68C'00000000: NT! MiFinishVadDeletion+0x554
Ffff828D'70317850 fffff800'83491749: 00000000'00000000 00000000'00000000 00000000'00000000 00000000'00000000: NT! MiDeleteVad+0xae4
Ffff828D'70317960 fffff800'83491522: Ffffa68C'69da93C0 00000000'00000000 ffffa68C'674ec080 00000000'00000000: NT! MiUnmapVad+0x49
Ffff828D'70317990 fffff800'83491399: 00000000'5B2aaeb4 00000000'5B23CA40 00000000'00000098 00000000'00000000: NT! MiUnmapViewOfSection+0x152
Ffff828D'70317A70 fffff800'8320CAF8: Ffffa68C'65ad52C0 00007FFF'86ef7F01 ffff828D'70317AD8 ffffa68C'674ec080: NT! NtUnmapViewOfSectionEx+0x99
Ffff828D'70317AC0 00007FFF'87C50a34: 00000000'00000000 00000000'00000000 00000000'00000000 00000000'00000000: NT! KiSystemServiceCopyEnd+0x28
00000000'0F7FE648 00000000'00000000: 00000000'00000000 00000000'00000000 00000000'00000000 00000000'00000000: 0x00007fff`87c50a34
SYMBOL_NAME: NT! RtlpHpLfhSubsegmentFreeBlock+8a
MODULE_NAME: NT
IMAGE_NAME: ntkrnlmp.exe
IMAGE_VERSION: 10.0.19041.2364
STACK_COMMAND: Cxr 0xffff828d70316bf0; KB
BUCKET_ID_FUNC_OFFSET: 8A
FAILURE_BUCKET_ID: AV_nt! RtlpHpLfhSubsegmentFreeBlock
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: Vb_release
OSPLATFORM_TYPE: X64
OSNAME: Windows 10
FAILURE_ID_HASH: {0C706EF1-02BF-81B2-1C3A-D61BE746C53F}
Followup: MachineOwner
---------