NTFS_FILE_SYSTEM (24)
If you see NtfsExceptionFilter on the stack then the 2nd and 3rd
parameters are the exception record and context record. Do a .cxr
on the 3rd parameter and then kb to obtain a more informative stack
trace.
Arguments:
Arg1: 00000000001904fb
Arg2: fffff88008e59008
Arg3: fffff88008e58860
Arg4: fffff8800120a2d7
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : AV.Dereference
Value: NullClassPtr
Key : AV.Fault
Value: Read
PROCESSES_ANALYSIS: 1
SERVICE_ANALYSIS: 1
STACKHASH_ANALYSIS: 1
TIMELINE_ANALYSIS: 1
DUMP_CLASS: 1
DUMP_QUALIFIER: 400
BUILD_VERSION_STRING: 7601.18409.amd64fre.win7sp1_gdr.140303-2144
SYSTEM_MANUFACTURER: Hewlett-Packard
SYSTEM_PRODUCT_NAME: HP Pavilion dv6 Notebook PC
SYSTEM_SKU: VY104EA#AB8
SYSTEM_VERSION: 049D210000241210000020000
BIOS_VENDOR: Hewlett-Packard
BIOS_VERSION: F.1C
BIOS_DATE: 05/17/2010
BASEBOARD_MANUFACTURER: Hewlett-Packard
BASEBOARD_PRODUCT: 3659
BASEBOARD_VERSION: 32.25
DUMP_TYPE: 2
BUGCHECK_P1: 1904fb
BUGCHECK_P2: fffff88008e59008
BUGCHECK_P3: fffff88008e58860
BUGCHECK_P4: fffff8800120a2d7
EXCEPTION_RECORD: fffff88008e59008 -- (.exr 0xfffff88008e59008)
ExceptionAddress: fffff8800120a2d7 (Ntfs! ?? ::FNODOBFM::`string'+0x0000000000003b12)
ExceptionCode: c0000005 (Access violation)
ExceptionFlags: 00000000
NumberParameters: 2
Parameter[0]: 0000000000000000
Parameter[1]: 0000000000000037
Attempt to read from address 0000000000000037
CONTEXT: fffff88008e58860 -- (.cxr 0xfffff88008e58860)
rax=ffffffffffffffff rbx=fffff8a0027d1370 rcx=0000000010000000
rdx=00000000ffffffff rsi=0000000000000000 rdi=fffff880024c2000
rip=fffff8800120a2d7 rsp=fffff88008e59240 rbp=0000000000004000
r8=0000000000000000 r9=0000000000004000 r10=fffffa80068e9330
r11=0000000000000000 r12=00000000ffffffff r13=fffff880024c2000
r14=0000000000137c00 r15=00000000007fffff
iopl=0 nv up ei ng nz na po nc
cs=0010 ss=0000 ds=002b es=002b fs=0053 gs=002b efl=00010286
Ntfs! ?? ::FNODOBFM::`string'+0x3b12:
fffff880`0120a2d7 483b5838 cmp rbx,qword ptr [rax+38h] ds:002b:00000000`00000037=????????????????
Resetting default scope
CPU_COUNT: 8
CPU_MHZ: 63c
CPU_VENDOR: GenuineIntel
CPU_FAMILY: 6
CPU_MODEL: 1e
CPU_STEPPING: 5
CPU_MICROCODE: 6,1e,5,0 (F,M,S,R) SIG: 4'00000000 (cache) 3'00000000 (init)
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: chrome.exe
CURRENT_IRQL: 0
FOLLOWUP_IP:
Ntfs! ?? ::FNODOBFM::`string'+3b12
fffff880`0120a2d7 483b5838 cmp rbx,qword ptr [rax+38h]
FAULTING_IP:
Ntfs! ?? ::FNODOBFM::`string'+3b12
fffff880`0120a2d7 483b5838 cmp rbx,qword ptr [rax+38h]
BUGCHECK_STR: 0x24
READ_ADDRESS: GetPointerFromAddress: unable to read from fffff800032b8100
Unable to get MmSystemRangeStart
GetUlongPtrFromAddress: unable to read from fffff800032b82e0
GetUlongPtrFromAddress: unable to read from fffff800032b8490
0000000000000037
DEFAULT_BUCKET_ID: NULL_CLASS_PTR_DEREFERENCE
ERROR_CODE: (NTSTATUS) 0xc0000005 - <Unable to get error code text>
EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - <Unable to get error code text>
EXCEPTION_CODE_STR: c0000005
EXCEPTION_PARAMETER1: 0000000000000000
EXCEPTION_PARAMETER2: 0000000000000037
ANALYSIS_SESSION_HOST: DESKTOP-BKJR0DQ
ANALYSIS_SESSION_TIME: 03-14-2020 21:34:48.0543
ANALYSIS_VERSION: 10.0.18362.1 amd64fre
LAST_CONTROL_TRANSFER: from fffff88001218703 to fffff8800120a2d7
STACK_TEXT:
fffff880`08e59240 fffff880`01218703 : fffff880`08e59690 fffff8a0`027d1370 fffffa80`068e9330 00000000`00000001 : Ntfs! ?? ::FNODOBFM::`string'+0x3b12
fffff880`08e59330 fffff880`01211ec8 : fffff880`08e59690 fffffa80`068e9330 fffff8a0`027d1208 fffff800`03073b94 : Ntfs!NtfsNonCachedIo+0x8a1
fffff880`08e594f0 fffff880`01212398 : fffff880`08e59690 fffffa80`068e9330 fffff880`08e59701 fffffa80`05960c01 : Ntfs!NtfsCommonRead+0x18df
fffff880`08e59660 fffff880`0106bbcf : fffffa80`068e96d0 fffffa80`068e9330 fffffa80`05960c30 00000000`00000000 : Ntfs!NtfsFsdRead+0x1b8
fffff880`08e59870 fffff880`0106a6df : fffffa80`04c92890 fffffa80`03fcbb01 fffffa80`04c92800 fffffa80`068e9330 : fltmgr!FltpLegacyProcessingAfterPreCallbacksCompleted+0x24f
fffff880`08e59900 fffff800`030a7e15 : fffffa80`068e9350 fffffa80`07461230 fffffa80`0581a350 fffff880`030f7180 : fltmgr!FltpDispatch+0xcf
fffff880`08e59960 fffff800`030a78e9 : 00000000`00000001 00000000`00000001 fffffa80`0581a290 fffffa80`0581a290 : nt!IoPageRead+0x255
fffff880`08e599f0 fffff800`0308e28a : 00000000`00000000 00000000`00000000 ffffffff`ffffffff fffff800`00000000 : nt!MiIssueHardFault+0x255
fffff880`08e59ac0 fffff800`0307ecee : 00000000`00000000 00000001`3fda9490 fffff880`00000001 00000000`00fd1c20 : nt!MmAccessFault+0x146a
fffff880`08e59c20 00000001`3fd76a80 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiPageFault+0x16e
00000000`0675f1a0 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x00000001`3fd76a80
THREAD_SHA1_HASH_MOD_FUNC: b6427b8714dcbeda0391f6bbcead73c60263a062
THREAD_SHA1_HASH_MOD_FUNC_OFFSET: 1957418a9beca955f88dbcdccb0ad4fea67063fa
THREAD_SHA1_HASH_MOD: 458206b0e973bff1b0b9213428f52545f3537fa3
FAULT_INSTR_CODE: 38583b48
SYMBOL_STACK_INDEX: 0
SYMBOL_NAME: Ntfs! ?? ::FNODOBFM::`string'+3b12
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: Ntfs
IMAGE_NAME: Ntfs.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 52e1be8a
IMAGE_VERSION: 6.1.7601.18378
STACK_COMMAND: .cxr 0xfffff88008e58860 ; kb
FAILURE_BUCKET_ID: X64_0x24_Ntfs!_??_::FNODOBFM::_string_+3b12
BUCKET_ID: X64_0x24_Ntfs!_??_::FNODOBFM::_string_+3b12
PRIMARY_PROBLEM_CLASS: X64_0x24_Ntfs!_??_::FNODOBFM::_string_+3b12
TARGET_TIME: 2019-12-27T15:13:14.000Z
OSBUILD: 7601
OSSERVICEPACK: 1000
SERVICEPACK_NUMBER: 0
OS_REVISION: 0
SUITE_MASK: 272
PRODUCT_TYPE: 1
OSPLATFORM_TYPE: x64
OSNAME: Windows 7
OSEDITION: Windows 7 WinNt (Service Pack 1) TerminalServer SingleUserTS
OS_LOCALE:
USER_LCID: 0
OSBUILD_TIMESTAMP: 2014-03-04 11:38:19
BUILDDATESTAMP_STR: 140303-2144
BUILDLAB_STR: win7sp1_gdr
BUILDOSVER_STR: 6.1.7601.18409.amd64fre.win7sp1_gdr.140303-2144
ANALYSIS_SESSION_ELAPSED_TIME: 364
ANALYSIS_SOURCE: KM
FAILURE_ID_HASH_STRING: km:x64_0x24_ntfs!_??_::fnodobfm::_string_+3b12
FAILURE_ID_HASH: {cac6093b-eb14-b534-9595-ba44a5888d3f}
Followup: MachineOwner
---------
DRIVER_CORRUPTED_EXPOOL (c5)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is
caused by drivers that have corrupted the system pool. Run the driver
verifier against any new (or suspect) drivers, and if that doesn't turn up
the culprit, then use gflags to enable special pool.
Arguments:
Arg1: ffffffffffffffff, memory referenced
Arg2: 0000000000000002, IRQL
Arg3: 0000000000000000, value 0 = read operation, 1 = write operation
Arg4: fffff800031f39bc, address which referenced memory
Debugging Details:
------------------
*** WARNING: Unable to verify timestamp for avgSP.sys
KEY_VALUES_STRING: 1
PROCESSES_ANALYSIS: 1
SERVICE_ANALYSIS: 1
STACKHASH_ANALYSIS: 1
TIMELINE_ANALYSIS: 1
DUMP_CLASS: 1
DUMP_QUALIFIER: 400
BUILD_VERSION_STRING: 7601.18409.amd64fre.win7sp1_gdr.140303-2144
SYSTEM_MANUFACTURER: Hewlett-Packard
SYSTEM_PRODUCT_NAME: HP Pavilion dv6 Notebook PC
SYSTEM_SKU: VY104EA#AB8
SYSTEM_VERSION: 049D210000241210000020000
BIOS_VENDOR: Hewlett-Packard
BIOS_VERSION: F.1C
BIOS_DATE: 05/17/2010
BASEBOARD_MANUFACTURER: Hewlett-Packard
BASEBOARD_PRODUCT: 3659
BASEBOARD_VERSION: 32.25
DUMP_TYPE: 2
BUGCHECK_P1: ffffffffffffffff
BUGCHECK_P2: 2
BUGCHECK_P3: 0
BUGCHECK_P4: fffff800031f39bc
BUGCHECK_STR: 0xC5_2
CURRENT_IRQL: 2
FAULTING_IP:
nt!ExDeferredFreePool+100
fffff800`031f39bc 4c8b02 mov r8,qword ptr [rdx]
CPU_COUNT: 8
CPU_MHZ: 63c
CPU_VENDOR: GenuineIntel
CPU_FAMILY: 6
CPU_MODEL: 1e
CPU_STEPPING: 5
CPU_MICROCODE: 6,1e,5,0 (F,M,S,R) SIG: 4'00000000 (cache) 3'00000000 (init)
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: WIN7_DRIVER_FAULT
PROCESS_NAME: aswidsagent.ex
ANALYSIS_SESSION_HOST: DESKTOP-BKJR0DQ
ANALYSIS_SESSION_TIME: 03-14-2020 21:34:40.0713
ANALYSIS_VERSION: 10.0.18362.1 amd64fre
TRAP_FRAME: fffff880093b86d0 -- (.trap 0xfffff880093b86d0)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=fffff8000324f6a0 rbx=0000000000000000 rcx=fffff8000324f6a0
rdx=ffffffffffffffff rsi=0000000000000000 rdi=0000000000000000
rip=fffff800031f39bc rsp=fffff880093b8860 rbp=0000000000000000
r8=ffffffffffffffff r9=fffffa8008004a00 r10=0000000000000000
r11=0000000000000000 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl zr na po nc
nt!ExDeferredFreePool+0x100:
fffff800`031f39bc 4c8b02 mov r8,qword ptr [rdx] ds:ffffffff`ffffffff=????????????????
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff800030be169 to fffff800030bebc0
STACK_TEXT:
fffff880`093b8588 fffff800`030be169 : 00000000`0000000a ffffffff`ffffffff 00000000`00000002 00000000`00000000 : nt!KeBugCheckEx
fffff880`093b8590 fffff800`030bcde0 : 00000000`81ea972e 00000000`00000004 00000000`00000008 00000000`000000ff : nt!KiBugCheckDispatch+0x69
fffff880`093b86d0 fffff800`031f39bc : fffff880`093b8a48 fffffa80`07879930 fffff880`093b8ab0 fffff880`093b89e0 : nt!KiPageFault+0x260
fffff880`093b8860 fffff800`031f24f1 : fffffa80`07de9460 fffffa80`0563c790 00000000`00000000 00000000`00000000 : nt!ExDeferredFreePool+0x100
fffff880`093b88f0 fffff880`042c4746 : 00000000`000fce74 fffff880`093b89c0 00000000`2b2b7741 fffff880`093b89c0 : nt!ExFreePoolWithTag+0x411
fffff880`093b89a0 00000000`000fce74 : fffff880`093b89c0 00000000`2b2b7741 fffff880`093b89c0 00000000`00000080 : avgSP+0x2c746
fffff880`093b89a8 fffff880`093b89c0 : 00000000`2b2b7741 fffff880`093b89c0 00000000`00000080 fffffa80`0563c7a0 : 0xfce74
fffff880`093b89b0 00000000`2b2b7741 : fffff880`093b89c0 00000000`00000080 fffffa80`0563c7a0 fffff880`00000000 : 0xfffff880`093b89c0
fffff880`093b89b8 fffff880`093b89c0 : 00000000`00000080 fffffa80`0563c7a0 fffff880`00000000 fffff880`00000080 : 0x2b2b7741
fffff880`093b89c0 00000000`00000080 : fffffa80`0563c7a0 fffff880`00000000 fffff880`00000080 fffffa80`0568a820 : 0xfffff880`093b89c0
fffff880`093b89c8 fffffa80`0563c7a0 : fffff880`00000000 fffff880`00000080 fffffa80`0568a820 fffffa80`00000000 : 0x80
fffff880`093b89d0 fffff880`00000000 : fffff880`00000080 fffffa80`0568a820 fffffa80`00000000 00000000`00000000 : 0xfffffa80`0563c7a0
fffff880`093b89d8 fffff880`00000080 : fffffa80`0568a820 fffffa80`00000000 00000000`00000000 00000000`00000000 : 0xfffff880`00000000
fffff880`093b89e0 fffffa80`0568a820 : fffffa80`00000000 00000000`00000000 00000000`00000000 00000000`00000040 : 0xfffff880`00000080
fffff880`093b89e8 fffffa80`00000000 : 00000000`00000000 00000000`00000000 00000000`00000040 fffff880`042c4d8c : 0xfffffa80`0568a820
fffff880`093b89f0 00000000`00000000 : 00000000`00000000 00000000`00000040 fffff880`042c4d8c fffff880`093b8bc0 : 0xfffffa80`00000000
THREAD_SHA1_HASH_MOD_FUNC: bdbd3cb545ace004cdd5edbffcfecd9d5e7d9be8
THREAD_SHA1_HASH_MOD_FUNC_OFFSET: 66ff7a61e14997cc58077ab3e3bf956cc39a2045
THREAD_SHA1_HASH_MOD: 7c4fe05f48b5d8f686a7a08d89906fed3d38ed36
FOLLOWUP_IP:
nt!ExDeferredFreePool+100
fffff800`031f39bc 4c8b02 mov r8,qword ptr [rdx]
FAULT_INSTR_CODE: f028b4c
SYMBOL_STACK_INDEX: 3
SYMBOL_NAME: nt!ExDeferredFreePool+100
FOLLOWUP_NAME: Pool_corruption
IMAGE_NAME: Pool_Corruption
DEBUG_FLR_IMAGE_TIMESTAMP: 0
IMAGE_VERSION: 6.1.7601.18409
MODULE_NAME: Pool_Corruption
STACK_COMMAND: .thread ; .cxr ; kb
FAILURE_BUCKET_ID: X64_0xC5_2_nt!ExDeferredFreePool+100
BUCKET_ID: X64_0xC5_2_nt!ExDeferredFreePool+100
PRIMARY_PROBLEM_CLASS: X64_0xC5_2_nt!ExDeferredFreePool+100
TARGET_TIME: 2019-11-09T19:58:06.000Z
OSBUILD: 7601
OSSERVICEPACK: 1000
SERVICEPACK_NUMBER: 0
OS_REVISION: 0
SUITE_MASK: 272
PRODUCT_TYPE: 1
OSPLATFORM_TYPE: x64
OSNAME: Windows 7
OSEDITION: Windows 7 WinNt (Service Pack 1) TerminalServer SingleUserTS
OS_LOCALE:
USER_LCID: 0
OSBUILD_TIMESTAMP: 2014-03-04 11:38:19
BUILDDATESTAMP_STR: 140303-2144
BUILDLAB_STR: win7sp1_gdr
BUILDOSVER_STR: 6.1.7601.18409.amd64fre.win7sp1_gdr.140303-2144
ANALYSIS_SESSION_ELAPSED_TIME: a6e
ANALYSIS_SOURCE: KM
FAILURE_ID_HASH_STRING: km:x64_0xc5_2_nt!exdeferredfreepool+100
FAILURE_ID_HASH: {525ba40d-3955-0874-581b-565c2c10b0b2}
Followup: Pool_corruption
---------
IRQL_NOT_LESS_OR_EQUAL (a)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If a kernel debugger is available get the stack backtrace.
Arguments:
Arg1: 0000007c50045da8, memory referenced
Arg2: 0000000000000002, IRQL
Arg3: 0000000000000001, bitfield :
bit 0 : value 0 = read operation, 1 = write operation
bit 3 : value 0 = not an execute operation, 1 = execute operation (only on chips which support this level of status)
Arg4: fffff80002ee4877, address which referenced memory
Debugging Details:
------------------
KEY_VALUES_STRING: 1
PROCESSES_ANALYSIS: 1
SERVICE_ANALYSIS: 1
STACKHASH_ANALYSIS: 1
TIMELINE_ANALYSIS: 1
DUMP_CLASS: 1
DUMP_QUALIFIER: 400
BUILD_VERSION_STRING: 7601.18409.amd64fre.win7sp1_gdr.140303-2144
SYSTEM_MANUFACTURER: Hewlett-Packard
SYSTEM_PRODUCT_NAME: HP Pavilion dv6 Notebook PC
SYSTEM_SKU: VY104EA#AB8
SYSTEM_VERSION: 049D210000241210000020000
BIOS_VENDOR: Hewlett-Packard
BIOS_VERSION: F.1C
BIOS_DATE: 05/17/2010
BASEBOARD_MANUFACTURER: Hewlett-Packard
BASEBOARD_PRODUCT: 3659
BASEBOARD_VERSION: 32.25
DUMP_TYPE: 2
BUGCHECK_P1: 7c50045da8
BUGCHECK_P2: 2
BUGCHECK_P3: 1
BUGCHECK_P4: fffff80002ee4877
WRITE_ADDRESS: GetPointerFromAddress: unable to read from fffff800030fe100
Unable to get MmSystemRangeStart
GetUlongPtrFromAddress: unable to read from fffff800030fe2e0
GetUlongPtrFromAddress: unable to read from fffff800030fe490
GetPointerFromAddress: unable to read from fffff800030fe0b8
0000007c50045da8
CURRENT_IRQL: 2
FAULTING_IP:
nt!MiResolveProtoPteFault+67
fffff800`02ee4877 0000 add byte ptr [rax],al
CPU_COUNT: 8
CPU_MHZ: 63c
CPU_VENDOR: GenuineIntel
CPU_FAMILY: 6
CPU_MODEL: 1e
CPU_STEPPING: 5
CPU_MICROCODE: 6,1e,5,0 (F,M,S,R) SIG: 4'00000000 (cache) 3'00000000 (init)
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: CODE_CORRUPTION
BUGCHECK_STR: 0xA
PROCESS_NAME: chrome.exe
ANALYSIS_SESSION_HOST: DESKTOP-BKJR0DQ
ANALYSIS_SESSION_TIME: 03-14-2020 21:34:46.0103
ANALYSIS_VERSION: 10.0.18362.1 amd64fre
TRAP_FRAME: fffff8800aee46c0 -- (.trap 0xfffff8800aee46c0)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=0000007c50045da8 rbx=0000000000000000 rcx=0000007ffffffff8
rdx=000007fed5fac160 rsi=0000000000000000 rdi=0000000000000000
rip=fffff80002ee4877 rsp=fffff8800aee485f rbp=fffff8800aee4918
r8=fffff8800aee4c20 r9=0000058000000000 r10=0000000fffffffff
r11=fffff68000000000 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl nz na pe nc
nt!MiResolveProtoPteFault+0x67:
fffff800`02ee4877 0000 add byte ptr [rax],al ds:0000007c`50045da8=??
Resetting default scope
UNALIGNED_STACK_POINTER: fffff8800aee485f
LAST_CONTROL_TRANSFER: from fffff80002ec6169 to fffff80002ec6bc0
STACK_TEXT:
fffff880`0aee4578 fffff800`02ec6169 : 00000000`0000000a 0000007c`50045da8 00000000`00000002 00000000`00000001 : nt!KeBugCheckEx
fffff880`0aee4580 fffff800`02ec4de0 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`000b61ea : nt!KiBugCheckDispatch+0x69
fffff880`0aee46c0 fffff800`02ee4877 : fff88002`f63180ff fffa8003`d75b50ff 00000000`000000ff fff80003`101cf000 : nt!KiPageFault+0x260
fffff880`0aee485f fffa8003`d75b5000 : fff80003`04b110ff fff80003`04b110ff 00000000`000002ff 00000000`00000000 : nt!MiResolveProtoPteFault+0x67
fffff880`0aee48ef fff80003`04b110ff : fff80003`04b110ff 00000000`000002ff 00000000`00000000 0000ba0a`8387d000 : 0xfffa8003`d75b5000
fffff880`0aee48f7 fff80003`04b110ff : 00000000`000002ff 00000000`00000000 0000ba0a`8387d000 fff8a008`bb57a800 : 0xfff80003`04b110ff
fffff880`0aee48ff 00000000`000002ff : 00000000`00000000 0000ba0a`8387d000 fff8a008`bb57a800 00000000`000000ff : 0xfff80003`04b110ff
fffff880`0aee4907 00000000`00000000 : 0000ba0a`8387d000 fff8a008`bb57a800 00000000`000000ff 00000000`00000000 : 0x2ff
CHKIMG_EXTENSION: !chkimg -lo 50 -d !nt
fffff80002ee4873 - nt!MiResolveProtoPteFault+63
[ 48:c8 ]
1 error : !nt (fffff80002ee4873)
MODULE_NAME: memory_corruption
IMAGE_NAME: memory_corruption
FOLLOWUP_NAME: memory_corruption
DEBUG_FLR_IMAGE_TIMESTAMP: 0
MEMORY_CORRUPTOR: ONE_BIT
STACK_COMMAND: .thread ; .cxr ; kb
FAILURE_BUCKET_ID: X64_MEMORY_CORRUPTION_ONE_BIT
BUCKET_ID: X64_MEMORY_CORRUPTION_ONE_BIT
PRIMARY_PROBLEM_CLASS: X64_MEMORY_CORRUPTION_ONE_BIT
TARGET_TIME: 2019-05-20T13:48:10.000Z
OSBUILD: 7601
OSSERVICEPACK: 1000
SERVICEPACK_NUMBER: 0
OS_REVISION: 0
SUITE_MASK: 272
PRODUCT_TYPE: 1
OSPLATFORM_TYPE: x64
OSNAME: Windows 7
OSEDITION: Windows 7 WinNt (Service Pack 1) TerminalServer SingleUserTS
OS_LOCALE:
USER_LCID: 0
OSBUILD_TIMESTAMP: 2014-03-04 11:38:19
BUILDDATESTAMP_STR: 140303-2144
BUILDLAB_STR: win7sp1_gdr
BUILDOSVER_STR: 6.1.7601.18409.amd64fre.win7sp1_gdr.140303-2144
ANALYSIS_SESSION_ELAPSED_TIME: 97dd
ANALYSIS_SOURCE: KM
FAILURE_ID_HASH_STRING: km:x64_memory_corruption_one_bit
FAILURE_ID_HASH: {2dbb898e-c425-bad1-90fe-71c78117521f}
Followup: memory_corruption
---------
SYSTEM_THREAD_EXCEPTION_NOT_HANDLED_M (1000007e)
This is a very common bugcheck. Usually the exception address pinpoints
the driver/function that caused the problem. Always note this address
as well as the link date of the driver/image that contains this address.
Some common problems are exception code 0x80000003. This means a hard
coded breakpoint or assertion was hit, but this system was booted
/NODEBUG. This is not supposed to happen as developers should never have
hardcoded breakpoints in retail code, but ...
If this happens, make sure a debugger gets connected, and the
system is booted /DEBUG. This will let us see why this breakpoint is
happening.
Arguments:
Arg1: ffffffffc0000005, The exception code that was not handled
Arg2: fffff88004822d20, The address that the exception occurred at
Arg3: fffff88005dfa6d8, Exception Record Address
Arg4: fffff88005df9f30, Context Record Address
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : AV.Fault
Value: Read
PROCESSES_ANALYSIS: 1
SERVICE_ANALYSIS: 1
STACKHASH_ANALYSIS: 1
TIMELINE_ANALYSIS: 1
DUMP_CLASS: 1
DUMP_QUALIFIER: 400
BUILD_VERSION_STRING: 7601.18409.amd64fre.win7sp1_gdr.140303-2144
SYSTEM_MANUFACTURER: Hewlett-Packard
SYSTEM_PRODUCT_NAME: HP Pavilion dv6 Notebook PC
SYSTEM_SKU: VY104EA#AB8
SYSTEM_VERSION: 049D210000241210000020000
BIOS_VENDOR: Hewlett-Packard
BIOS_VERSION: F.1C
BIOS_DATE: 05/17/2010
BASEBOARD_MANUFACTURER: Hewlett-Packard
BASEBOARD_PRODUCT: 3659
BASEBOARD_VERSION: 32.25
DUMP_TYPE: 2
BUGCHECK_P1: ffffffffc0000005
BUGCHECK_P2: fffff88004822d20
BUGCHECK_P3: fffff88005dfa6d8
BUGCHECK_P4: fffff88005df9f30
EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - <Unable to get error code text>
FAULTING_IP:
dxgmms1!VIDMM_GLOBAL::PrepareDmaBuffer+168
fffff880`04822d20 8b9000030000 mov edx,dword ptr [rax+300h]
EXCEPTION_RECORD: fffff88005dfa6d8 -- (.exr 0xfffff88005dfa6d8)
ExceptionAddress: fffff88004822d20 (dxgmms1!VIDMM_GLOBAL::PrepareDmaBuffer+0x0000000000000168)
ExceptionCode: c0000005 (Access violation)
ExceptionFlags: 00000000
NumberParameters: 2
Parameter[0]: 0000000000000000
Parameter[1]: ffffffffffffffff
Attempt to read from address ffffffffffffffff
CONTEXT: fffff88005df9f30 -- (.cxr 0xfffff88005df9f30)
rax=7ffffa800649b000 rbx=00000000c0000001 rcx=fffff8a0030a5980
rdx=01d4f2377b39c8ec rsi=fffffa8005bdc370 rdi=fffffa80064a5000
rip=fffff88004822d20 rsp=fffff88005dfa910 rbp=fffff8a0034ef340
r8=00000000000011b6 r9=fffffa800416ec40 r10=0000000000000000
r11=000000000000000b r12=0000000000000000 r13=fffffa800416ec40
r14=fffffa800416ec40 r15=0000000000000001
iopl=0 nv up ei pl zr na po nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00010246
dxgmms1!VIDMM_GLOBAL::PrepareDmaBuffer+0x168:
fffff880`04822d20 8b9000030000 mov edx,dword ptr [rax+300h] ds:002b:7ffffa80`0649b300=????????
Resetting default scope
CPU_COUNT: 8
CPU_MHZ: 63c
CPU_VENDOR: GenuineIntel
CPU_FAMILY: 6
CPU_MODEL: 1e
CPU_STEPPING: 5
CPU_MICROCODE: 6,1e,5,0 (F,M,S,R) SIG: 4'00000000 (cache) 3'00000000 (init)
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: WIN7_DRIVER_FAULT
PROCESS_NAME: System
CURRENT_IRQL: 0
FOLLOWUP_IP:
dxgmms1!VIDMM_GLOBAL::PrepareDmaBuffer+168
fffff880`04822d20 8b9000030000 mov edx,dword ptr [rax+300h]
BUGCHECK_STR: 0x7E
READ_ADDRESS: GetPointerFromAddress: unable to read from fffff800030ff100
Unable to get MmSystemRangeStart
GetUlongPtrFromAddress: unable to read from fffff800030ff2e0
GetUlongPtrFromAddress: unable to read from fffff800030ff490
GetPointerFromAddress: unable to read from fffff800030ff0b8
ffffffffffffffff
ERROR_CODE: (NTSTATUS) 0xc0000005 - <Unable to get error code text>
EXCEPTION_CODE_STR: c0000005
EXCEPTION_PARAMETER1: 0000000000000000
EXCEPTION_PARAMETER2: ffffffffffffffff
ANALYSIS_SESSION_HOST: DESKTOP-BKJR0DQ
ANALYSIS_SESSION_TIME: 03-14-2020 21:34:50.0288
ANALYSIS_VERSION: 10.0.18362.1 amd64fre
LAST_CONTROL_TRANSFER: from fffff8800483d7d9 to fffff88004822d20
STACK_TEXT:
fffff880`05dfa910 fffff880`0483d7d9 : 00000000`00000000 fffff8a0`034ef340 fffffa80`00000000 fffffa80`0416ec40 : dxgmms1!VIDMM_GLOBAL::PrepareDmaBuffer+0x168
fffff880`05dfaae0 fffff880`0483d514 : fffff800`00b96080 fffff880`0483cf00 fffffa80`00000000 fffffa80`00000000 : dxgmms1!VidSchiSubmitRenderCommand+0x241
fffff880`05dfacd0 fffff880`0483d012 : 00000000`00005e6c fffffa80`03f246e0 00000000`00000080 fffffa80`05bdc370 : dxgmms1!VidSchiSubmitQueueCommand+0x50
fffff880`05dfad00 fffff800`0316373a : 00000000`01c9507a fffffa80`05bb4a00 fffffa80`03c72b30 fffffa80`05bb4a00 : dxgmms1!VidSchiWorkerThread+0xd6
fffff880`05dfad40 fffff800`02eb88e6 : fffff800`03042e80 fffffa80`05bb4a00 fffff800`03050cc0 00000004`f0742400 : nt!PspSystemThreadStartup+0x5a
fffff880`05dfad80 00000000`00000000 : fffff880`05dfb000 fffff880`05df5000 fffff880`05dfa680 00000000`00000000 : nt!KxStartSystemThread+0x16
THREAD_SHA1_HASH_MOD_FUNC: ae2eef96d9685f336598baea99a06a86a5bd78d6
THREAD_SHA1_HASH_MOD_FUNC_OFFSET: 327f73de7f8071ce7ddf917691ebb5dbe8bf1b6b
THREAD_SHA1_HASH_MOD: 6575fcd5d8995a3abb6d236ae80c4d3ec9bd00ed
FAULT_INSTR_CODE: 300908b
SYMBOL_STACK_INDEX: 0
SYMBOL_NAME: dxgmms1!VIDMM_GLOBAL::PrepareDmaBuffer+168
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: dxgmms1
IMAGE_NAME: dxgmms1.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 5164dc13
IMAGE_VERSION: 6.1.7601.18126
STACK_COMMAND: .cxr 0xfffff88005df9f30 ; kb
FAILURE_BUCKET_ID: X64_0x7E_dxgmms1!VIDMM_GLOBAL::PrepareDmaBuffer+168
BUCKET_ID: X64_0x7E_dxgmms1!VIDMM_GLOBAL::PrepareDmaBuffer+168
PRIMARY_PROBLEM_CLASS: X64_0x7E_dxgmms1!VIDMM_GLOBAL::PrepareDmaBuffer+168
TARGET_TIME: 2019-04-13T20:28:41.000Z
OSBUILD: 7601
OSSERVICEPACK: 1000
SERVICEPACK_NUMBER: 0
OS_REVISION: 0
SUITE_MASK: 272
PRODUCT_TYPE: 1
OSPLATFORM_TYPE: x64
OSNAME: Windows 7
OSEDITION: Windows 7 WinNt (Service Pack 1) TerminalServer SingleUserTS
OS_LOCALE:
USER_LCID: 0
OSBUILD_TIMESTAMP: 2014-03-04 11:38:19
BUILDDATESTAMP_STR: 140303-2144
BUILDLAB_STR: win7sp1_gdr
BUILDOSVER_STR: 6.1.7601.18409.amd64fre.win7sp1_gdr.140303-2144
ANALYSIS_SESSION_ELAPSED_TIME: 44e
ANALYSIS_SOURCE: KM
FAILURE_ID_HASH_STRING: km:x64_0x7e_dxgmms1!vidmm_global::preparedmabuffer+168
FAILURE_ID_HASH: {ce4a5d2c-b946-63d0-5e26-c2a40bbac3ea}
Followup: MachineOwner
---------
IRQL_NOT_LESS_OR_EQUAL (a)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If a kernel debugger is available get the stack backtrace.
Arguments:
Arg1: 0000000000120028, memory referenced
Arg2: 0000000000000002, IRQL
Arg3: 0000000000000001, bitfield :
bit 0 : value 0 = read operation, 1 = write operation
bit 3 : value 0 = not an execute operation, 1 = execute operation (only on chips which support this level of status)
Arg4: fffff800030866e3, address which referenced memory
Debugging Details:
------------------
KEY_VALUES_STRING: 1
PROCESSES_ANALYSIS: 1
SERVICE_ANALYSIS: 1
STACKHASH_ANALYSIS: 1
TIMELINE_ANALYSIS: 1
DUMP_CLASS: 1
DUMP_QUALIFIER: 400
BUILD_VERSION_STRING: 7601.18409.amd64fre.win7sp1_gdr.140303-2144
SYSTEM_MANUFACTURER: Hewlett-Packard
SYSTEM_PRODUCT_NAME: HP Pavilion dv6 Notebook PC
SYSTEM_SKU: VY104EA#AB8
SYSTEM_VERSION: 049D210000241210000020000
BIOS_VENDOR: Hewlett-Packard
BIOS_VERSION: F.1C
BIOS_DATE: 05/17/2010
BASEBOARD_MANUFACTURER: Hewlett-Packard
BASEBOARD_PRODUCT: 3659
BASEBOARD_VERSION: 32.25
DUMP_TYPE: 2
BUGCHECK_P1: 120028
BUGCHECK_P2: 2
BUGCHECK_P3: 1
BUGCHECK_P4: fffff800030866e3
WRITE_ADDRESS: GetPointerFromAddress: unable to read from fffff800032cc100
Unable to get MmSystemRangeStart
GetUlongPtrFromAddress: unable to read from fffff800032cc2e0
GetUlongPtrFromAddress: unable to read from fffff800032cc490
GetPointerFromAddress: unable to read from fffff800032cc0b8
0000000000120028
CURRENT_IRQL: 2
FAULTING_IP:
nt!KiInsertQueueApc+133
fffff800`030866e3 f083402801 lock add dword ptr [rax+28h],1
CPU_COUNT: 8
CPU_MHZ: 63c
CPU_VENDOR: GenuineIntel
CPU_FAMILY: 6
CPU_MODEL: 1e
CPU_STEPPING: 5
CPU_MICROCODE: 6,1e,5,0 (F,M,S,R) SIG: 4'00000000 (cache) 3'00000000 (init)
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: WIN7_DRIVER_FAULT
BUGCHECK_STR: 0xA
PROCESS_NAME: chrome.exe
ANALYSIS_SESSION_HOST: DESKTOP-BKJR0DQ
ANALYSIS_SESSION_TIME: 03-14-2020 21:34:54.0925
ANALYSIS_VERSION: 10.0.18362.1 amd64fre
TRAP_FRAME: fffff88008f618e0 -- (.trap 0xfffff88008f618e0)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=0000000000120000 rbx=0000000000000000 rcx=0000000000000000
rdx=fffffa8003ec0230 rsi=0000000000000000 rdi=0000000000000000
rip=fffff800030866e3 rsp=fffff88008f61a70 rbp=fffff88002f63180
r8=0000000000000000 r9=fffffa8003eb10b0 r10=fffff80003224501
r11=fffff88008f61a00 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl nz na po nc
nt!KiInsertQueueApc+0x133:
fffff800`030866e3 f083402801 lock add dword ptr [rax+28h],1 ds:00000000`00120028=????????
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff80003094169 to fffff80003094bc0
STACK_TEXT:
fffff880`08f61798 fffff800`03094169 : 00000000`0000000a 00000000`00120028 00000000`00000002 00000000`00000001 : nt!KeBugCheckEx
fffff880`08f617a0 fffff800`03092de0 : 00000000`00000000 0000000f`ffffffff 00000000`00000000 fffffa80`03eb1060 : nt!KiBugCheckDispatch+0x69
fffff880`08f618e0 fffff800`030866e3 : fffff880`02f63180 fffffa80`04116501 fffff800`03224720 00000000`00000000 : nt!KiPageFault+0x260
fffff880`08f61a70 fffff800`030756a4 : fffffa80`03eb1060 00000000`00000000 fffffa80`03ec0220 fffffa80`03ec0220 : nt!KiInsertQueueApc+0x133
fffff880`08f61aa0 fffff800`0336a4bb : fffffa80`03eb1060 00000000`c0000005 fffffa80`03ec0220 00000000`000007ff : nt!KeInsertQueueApc+0x80
fffff880`08f61b00 fffff800`0334c79d : 00000000`00000008 fffffa80`03e73420 fffffa80`03eb1060 fffffa80`04014760 : nt!PspTerminateThreadByPointer+0xd7
fffff880`08f61b50 fffff800`0334cf04 : ffffffff`ffffffff 00000000`00000001 fffffa80`04014760 0000007f`00000008 : nt!PspTerminateAllThreads+0x1a9
fffff880`08f61ba0 fffff800`03093e53 : fffffa80`04014760 00000000`c0000005 fffffa80`03e73420 00000000`00000026 : nt!NtTerminateProcess+0xf4
fffff880`08f61c20 00000000`76d8157a : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x13
00000000`05bdfda8 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x76d8157a
THREAD_SHA1_HASH_MOD_FUNC: 7d4e23a8d4c34053283dbe305f49c3fddeb839e9
THREAD_SHA1_HASH_MOD_FUNC_OFFSET: a61dae48b140de6553a13563edd53ea1082ef171
THREAD_SHA1_HASH_MOD: 9f457f347057f10e1df248e166a3e95e6570ecfe
FOLLOWUP_IP:
nt!KiInsertQueueApc+133
fffff800`030866e3 f083402801 lock add dword ptr [rax+28h],1
FAULT_INSTR_CODE: 284083f0
SYMBOL_STACK_INDEX: 3
SYMBOL_NAME: nt!KiInsertQueueApc+133
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
DEBUG_FLR_IMAGE_TIMESTAMP: 531590fb
IMAGE_VERSION: 6.1.7601.18409
STACK_COMMAND: .thread ; .cxr ; kb
FAILURE_BUCKET_ID: X64_0xA_nt!KiInsertQueueApc+133
BUCKET_ID: X64_0xA_nt!KiInsertQueueApc+133
PRIMARY_PROBLEM_CLASS: X64_0xA_nt!KiInsertQueueApc+133
TARGET_TIME: 2020-03-10T18:00:20.000Z
OSBUILD: 7601
OSSERVICEPACK: 1000
SERVICEPACK_NUMBER: 0
OS_REVISION: 0
SUITE_MASK: 272
PRODUCT_TYPE: 1
OSPLATFORM_TYPE: x64
OSNAME: Windows 7
OSEDITION: Windows 7 WinNt (Service Pack 1) TerminalServer SingleUserTS
OS_LOCALE:
USER_LCID: 0
OSBUILD_TIMESTAMP: 2014-03-04 11:38:19
BUILDDATESTAMP_STR: 140303-2144
BUILDLAB_STR: win7sp1_gdr
BUILDOSVER_STR: 6.1.7601.18409.amd64fre.win7sp1_gdr.140303-2144
ANALYSIS_SESSION_ELAPSED_TIME: 454
ANALYSIS_SOURCE: KM
FAILURE_ID_HASH_STRING: km:x64_0xa_nt!kiinsertqueueapc+133
FAILURE_ID_HASH: {bc41732c-6aae-9c2d-d51d-e6cc1a1d0a09}
Followup: MachineOwner
---------
DRIVER_IRQL_NOT_LESS_OR_EQUAL (d1)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If kernel debugger is available get stack backtrace.
Arguments:
Arg1: fffffa7f91b36060, memory referenced
Arg2: 0000000000000002, IRQL
Arg3: 0000000000000001, value 0 = read operation, 1 = write operation
Arg4: fffff88005e2af0c, address which referenced memory
Debugging Details:
------------------
*** WARNING: Unable to verify timestamp for win32k.sys
KEY_VALUES_STRING: 1
PROCESSES_ANALYSIS: 1
SERVICE_ANALYSIS: 1
STACKHASH_ANALYSIS: 1
TIMELINE_ANALYSIS: 1
DUMP_CLASS: 1
DUMP_QUALIFIER: 400
BUILD_VERSION_STRING: 7601.18409.amd64fre.win7sp1_gdr.140303-2144
SYSTEM_MANUFACTURER: Hewlett-Packard
SYSTEM_PRODUCT_NAME: HP Pavilion dv6 Notebook PC
SYSTEM_SKU: VY104EA#AB8
SYSTEM_VERSION: 049D210000241210000020000
BIOS_VENDOR: Hewlett-Packard
BIOS_VERSION: F.1C
BIOS_DATE: 05/17/2010
BASEBOARD_MANUFACTURER: Hewlett-Packard
BASEBOARD_PRODUCT: 3659
BASEBOARD_VERSION: 32.25
DUMP_TYPE: 2
BUGCHECK_P1: fffffa7f91b36060
BUGCHECK_P2: 2
BUGCHECK_P3: 1
BUGCHECK_P4: fffff88005e2af0c
WRITE_ADDRESS: GetPointerFromAddress: unable to read from fffff800032fc100
Unable to get MmSystemRangeStart
GetUlongPtrFromAddress: unable to read from fffff800032fc2e0
GetUlongPtrFromAddress: unable to read from fffff800032fc490
GetPointerFromAddress: unable to read from fffff800032fc0b8
fffffa7f91b36060
CURRENT_IRQL: 2
FAULTING_IP:
usbccgp!UsbcForwardIrp+2c
fffff880`05e2af0c 80b10020488bd6 xor byte ptr [rcx-74B7E000h],0D6h
CPU_COUNT: 8
CPU_MHZ: 63c
CPU_VENDOR: GenuineIntel
CPU_FAMILY: 6
CPU_MODEL: 1e
CPU_STEPPING: 5
CPU_MICROCODE: 6,1e,5,0 (F,M,S,R) SIG: 4'00000000 (cache) 4'00000000 (init)
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: CODE_CORRUPTION
BUGCHECK_STR: 0xD1
PROCESS_NAME: System
ANALYSIS_SESSION_HOST: DESKTOP-BKJR0DQ
ANALYSIS_SESSION_TIME: 03-14-2020 21:34:58.0756
ANALYSIS_VERSION: 10.0.18362.1 amd64fre
TRAP_FRAME: fffff8800318f5d0 -- (.trap 0xfffff8800318f5d0)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=00000000f06b4fd5 rbx=0000000000000000 rcx=fffffa80066b4060
rdx=fffffa8006687240 rsi=0000000000000000 rdi=0000000000000000
rip=fffff88005e2af0c rsp=fffff8800318f760 rbp=0000000000000000
r8=fffffa8006687240 r9=0000000000000009 r10=fffff88003167b20
r11=0000000000000002 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei ng nz ac pe cy
usbccgp!UsbcForwardIrp+0x2c:
fffff880`05e2af0c 80b10020488bd6 xor byte ptr [rcx-74B7E000h],0D6h ds:fffffa7f`91b36060=??
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff800030c4169 to fffff800030c4bc0
STACK_TEXT:
fffff880`0318f488 fffff800`030c4169 : 00000000`0000000a fffffa7f`91b36060 00000000`00000002 00000000`00000001 : nt!KeBugCheckEx
fffff880`0318f490 fffff800`030c2de0 : fffff880`0316000b fffff880`0318f628 00000000`00000008 fffffa80`06a16b58 : nt!KiBugCheckDispatch+0x69
fffff880`0318f5d0 fffff880`05e2af0c : 00000000`00000000 fffffa80`06a162b8 00000000`00000002 fffffa80`06a161b8 : nt!KiPageFault+0x260
fffff880`0318f760 fffff880`05e276d6 : fffffa80`06a16b58 fffffa80`06687240 00000000`00000324 fffffa80`06687240 : usbccgp!UsbcForwardIrp+0x2c
fffff880`0318f790 fffff880`05e2797e : fffffa80`06a161b8 00000000`00220003 fffffa80`06687240 fffffa80`06a16b58 : usbccgp!DispatchPdoUrb+0xfa
fffff880`0318f7d0 fffff880`05e2572e : 00000000`0000000f fffffa80`06a16b50 fffffa80`06a16b58 fffffa80`06687240 : usbccgp!DispatchPdoInternalDeviceControl+0x17a
fffff880`0318f800 fffff880`05e4548f : fffffa80`06a16a00 fffffa80`06687201 00000000`00000000 00000000`000007ff : usbccgp!USBC_Dispatch+0x2de
fffff880`0318f880 fffff880`05e44f5b : fffffa80`06687598 fffffa80`06867601 fffff880`0318f940 fffffa80`06867540 : hidusb!HumReadReport+0x13f
fffff880`0318f8d0 fffff880`05fea555 : fffffa80`0695d001 fffffa80`0695d0f0 fffffa80`06687240 00000000`00000008 : hidusb!HumInternalIoctl+0x137
fffff880`0318f940 fffff880`05fead75 : fffffa80`0695d0f0 fffffa80`068676b0 00000000`00000000 00000000`00000008 : HIDCLASS!HidpSubmitInterruptRead+0xdd
fffff880`0318f9a0 fffff800`030c85d1 : fffffa80`0668759b 00000000`00000000 fffffa80`06867501 fffffa80`06687200 : HIDCLASS!HidpInterruptReadComplete+0x37d
fffff880`0318fa30 fffff880`04a8f631 : fffffa80`0607e050 fffffa80`06010a00 00000000`00000000 00000000`00000000 : nt!IopfCompleteRequest+0x341
fffff880`0318fb20 fffff880`04a8fb0f : fffffa80`046f9c02 fffffa80`06687240 00000000`ffffffff fffffa80`0607eeb0 : USBPORT!USBPORT_Core_iCompleteDoneTransfer+0xa15
fffff880`0318fc00 fffff880`04a8d66f : fffffa80`0607eeb0 fffffa80`0607e1a0 fffffa80`0607f050 00000000`00000000 : USBPORT!USBPORT_Core_iIrpCsqCompleteDoneTransfer+0x3a7
fffff880`0318fc60 fffff880`04a7ef89 : fffffa80`0607e050 00000000`00000000 fffffa80`0607ee02 fffffa80`0607eeb0 : USBPORT!USBPORT_Core_UsbIocDpc_Worker+0xf3
fffff880`0318fca0 fffff800`030cf30c : fffff880`03167180 fffffa80`0607eeb0 fffffa80`0607eec8 00000000`00000000 : USBPORT!USBPORT_Xdpc_Worker+0x1d9
fffff880`0318fcd0 fffff800`030bc8ca : fffff880`03167180 fffff880`031720c0 00000000`00000000 fffff880`04a7edb0 : nt!KiRetireDpcList+0x1bc
fffff880`0318fd80 00000000`00000000 : fffff880`03190000 fffff880`0318a000 fffff880`0318fd40 00000000`00000000 : nt!KiIdleLoop+0x5a
CHKIMG_EXTENSION: !chkimg -lo 50 -db !usbccgp
8 errors : !usbccgp (fffff88005e2af07-fffff88005e2af3f)
fffff88005e2af00 f9 49 8b d0 48 8b c8 *1d 8b f0 ff 15 80 b1 00 *20 .I..H..........
fffff88005e2af10 48 8b d6 48 8b cf 8b *00 e8 3b ff ff ff 48 8d *cc H..H.....;...H..
fffff88005e2af20 c8 00 00 00 41 b8 20 *8b 00 00 48 8b d6 ff 15 *00 ....A. ...H.....
fffff88005e2af30 b1 00 00 48 8b 74 24 *8b 8b c3 48 8b 5c 24 30 *d8 ...H.t$...H.\$0.
MODULE_NAME: memory_corruption
IMAGE_NAME: memory_corruption
FOLLOWUP_NAME: memory_corruption
DEBUG_FLR_IMAGE_TIMESTAMP: 0
MEMORY_CORRUPTOR: STRIDE
STACK_COMMAND: .thread ; .cxr ; kb
FAILURE_BUCKET_ID: X64_MEMORY_CORRUPTION_STRIDE
BUCKET_ID: X64_MEMORY_CORRUPTION_STRIDE
PRIMARY_PROBLEM_CLASS: X64_MEMORY_CORRUPTION_STRIDE
TARGET_TIME: 2020-02-20T18:53:46.000Z
OSBUILD: 7601
OSSERVICEPACK: 1000
SERVICEPACK_NUMBER: 0
OS_REVISION: 0
SUITE_MASK: 272
PRODUCT_TYPE: 1
OSPLATFORM_TYPE: x64
OSNAME: Windows 7
OSEDITION: Windows 7 WinNt (Service Pack 1) TerminalServer SingleUserTS
OS_LOCALE:
USER_LCID: 0
OSBUILD_TIMESTAMP: 2014-03-04 11:38:19
BUILDDATESTAMP_STR: 140303-2144
BUILDLAB_STR: win7sp1_gdr
BUILDOSVER_STR: 6.1.7601.18409.amd64fre.win7sp1_gdr.140303-2144
ANALYSIS_SESSION_ELAPSED_TIME: 426c
ANALYSIS_SOURCE: KM
FAILURE_ID_HASH_STRING: km:x64_memory_corruption_stride
FAILURE_ID_HASH: {54f6a81e-bd17-9afc-f167-0352818951c1}
Followup: memory_corruption
---------
SYSTEM_THREAD_EXCEPTION_NOT_HANDLED_M (1000007e)
This is a very common bugcheck. Usually the exception address pinpoints
the driver/function that caused the problem. Always note this address
as well as the link date of the driver/image that contains this address.
Some common problems are exception code 0x80000003. This means a hard
coded breakpoint or assertion was hit, but this system was booted
/NODEBUG. This is not supposed to happen as developers should never have
hardcoded breakpoints in retail code, but ...
If this happens, make sure a debugger gets connected, and the
system is booted /DEBUG. This will let us see why this breakpoint is
happening.
Arguments:
Arg1: ffffffffc0000005, The exception code that was not handled
Arg2: fffff88004cf1aa3, The address that the exception occurred at
Arg3: fffff880082d1918, Exception Record Address
Arg4: fffff880082d1170, Context Record Address
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : AV.Fault
Value: Read
PROCESSES_ANALYSIS: 1
SERVICE_ANALYSIS: 1
STACKHASH_ANALYSIS: 1
TIMELINE_ANALYSIS: 1
DUMP_CLASS: 1
DUMP_QUALIFIER: 400
BUILD_VERSION_STRING: 7601.18409.amd64fre.win7sp1_gdr.140303-2144
DUMP_TYPE: 2
BUGCHECK_P1: ffffffffc0000005
BUGCHECK_P2: fffff88004cf1aa3
BUGCHECK_P3: fffff880082d1918
BUGCHECK_P4: fffff880082d1170
EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - <Unable to get error code text>
FAULTING_IP:
+0
fffff880`04cf1aa3 488b10 mov rdx,qword ptr [rax]
EXCEPTION_RECORD: fffff880082d1918 -- (.exr 0xfffff880082d1918)
ExceptionAddress: fffff88004cf1aa3
ExceptionCode: c0000005 (Access violation)
ExceptionFlags: 00000000
NumberParameters: 2
Parameter[0]: 0000000000000000
Parameter[1]: ffffffffffffffff
Attempt to read from address ffffffffffffffff
CONTEXT: fffff880082d1170 -- (.cxr 0xfffff880082d1170)
rax=ffff018006000050 rbx=0000000000000000 rcx=fffffa80057b9690
rdx=0000000000000000 rsi=fffffa80057b9690 rdi=0000000000000000
rip=fffff88004cf1aa3 rsp=fffff880082d1b50 rbp=0000000000000000
r8=0000000000000000 r9=0000000000000000 r10=ffffffffffffffef
r11=0000000000000000 r12=0000000000000000 r13=0000000000000001
r14=fffff880082d1ce8 r15=0000000000000001
iopl=0 nv up ei pl zr na po nc
cs=0010 ss=0000 ds=002b es=002b fs=0053 gs=002b efl=00010246
fffff880`04cf1aa3 488b10 mov rdx,qword ptr [rax] ds:002b:ffff0180`06000050=????????????????
Resetting default scope
CPU_COUNT: 8
CPU_MHZ: 63c
CPU_VENDOR: GenuineIntel
CPU_FAMILY: 6
CPU_MODEL: 1e
CPU_STEPPING: 5
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: WIN7_DRIVER_FAULT
CURRENT_IRQL: 0
FOLLOWUP_IP:
nt!KiCommitThreadWait+1d2
fffff800`030ca5f2 0fb6e8 movzx ebp,al
BUGCHECK_STR: 0x7E
READ_ADDRESS: GetPointerFromAddress: unable to read from fffff8000330c100
Unable to get MmSystemRangeStart
GetUlongPtrFromAddress: unable to read from fffff8000330c2e0
GetUlongPtrFromAddress: unable to read from fffff8000330c490
GetPointerFromAddress: unable to read from fffff8000330c0b8
ffffffffffffffff
ERROR_CODE: (NTSTATUS) 0xc0000005 - <Unable to get error code text>
EXCEPTION_CODE_STR: c0000005
EXCEPTION_PARAMETER1: 0000000000000000
EXCEPTION_PARAMETER2: ffffffffffffffff
ANALYSIS_SESSION_HOST: DESKTOP-BKJR0DQ
ANALYSIS_SESSION_TIME: 03-14-2020 21:33:46.0951
ANALYSIS_VERSION: 10.0.18362.1 amd64fre
LAST_CONTROL_TRANSFER: from fffffa80043c3148 to fffff88004cf1aa3
STACK_TEXT:
fffff880`082d1b50 fffffa80`043c3148 : fffff800`030ca5f2 fffffa80`043c3040 fffffa80`043c3040 00000000`00000001 : 0xfffff880`04cf1aa3
fffff880`082d1b58 fffff800`030ca5f2 : fffffa80`043c3040 fffffa80`043c3040 00000000`00000001 fffff880`082d1ce8 : 0xfffffa80`043c3148
fffff880`082d1b60 fffff880`04c8bacf : 00000000`00000001 fffffa80`0617c510 fffffa80`0617c5a0 00000000`00000000 : nt!KiCommitThreadWait+0x1d2
fffff880`082d1bf0 00000000`00000001 : fffffa80`0617c510 fffffa80`0617c5a0 00000000`00000000 fffff800`0327a280 : 0xfffff880`04c8bacf
fffff880`082d1bf8 fffffa80`0617c510 : fffffa80`0617c5a0 00000000`00000000 fffff800`0327a280 fffff880`04c8c2bb : 0x1
fffff880`082d1c00 fffffa80`0617c5a0 : 00000000`00000000 fffff800`0327a280 fffff880`04c8c2bb fffffa80`056f4000 : 0xfffffa80`0617c510
fffff880`082d1c08 00000000`00000000 : fffff800`0327a280 fffff880`04c8c2bb fffffa80`056f4000 fffffa80`056f4000 : 0xfffffa80`0617c5a0
THREAD_SHA1_HASH_MOD_FUNC: 7f5cec5671ab3d45f4bc410b3e21c0f0d9773478
THREAD_SHA1_HASH_MOD_FUNC_OFFSET: 0fea2dac7eee85e1fd78a9899b3af529d0c2ff2c
THREAD_SHA1_HASH_MOD: 76cd06466d098060a9eb26e5fd2a25cb1f3fe0a3
FAULT_INSTR_CODE: 48e8b60f
SYMBOL_STACK_INDEX: 2
SYMBOL_NAME: nt!KiCommitThreadWait+1d2
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
DEBUG_FLR_IMAGE_TIMESTAMP: 531590fb
IMAGE_VERSION: 6.1.7601.18409
STACK_COMMAND: .cxr 0xfffff880082d1170 ; kb
FAILURE_BUCKET_ID: X64_0x7E_nt!KiCommitThreadWait+1d2
BUCKET_ID: X64_0x7E_nt!KiCommitThreadWait+1d2
PRIMARY_PROBLEM_CLASS: X64_0x7E_nt!KiCommitThreadWait+1d2
TARGET_TIME: 2020-02-17T17:50:25.000Z
OSBUILD: 7601
OSSERVICEPACK: 1000
SERVICEPACK_NUMBER: 0
OS_REVISION: 0
SUITE_MASK: 272
PRODUCT_TYPE: 1
OSPLATFORM_TYPE: x64
OSNAME: Windows 7
OSEDITION: Windows 7 WinNt (Service Pack 1) TerminalServer SingleUserTS
OS_LOCALE:
USER_LCID: 0
OSBUILD_TIMESTAMP: 2014-03-04 11:38:19
BUILDDATESTAMP_STR: 140303-2144
BUILDLAB_STR: win7sp1_gdr
BUILDOSVER_STR: 6.1.7601.18409.amd64fre.win7sp1_gdr.140303-2144
ANALYSIS_SESSION_ELAPSED_TIME: 44e
ANALYSIS_SOURCE: KM
FAILURE_ID_HASH_STRING: km:x64_0x7e_nt!kicommitthreadwait+1d2
FAILURE_ID_HASH: {390b439e-4e8c-0fd0-ad5e-8840007cbb13}
Followup: MachineOwner
---------
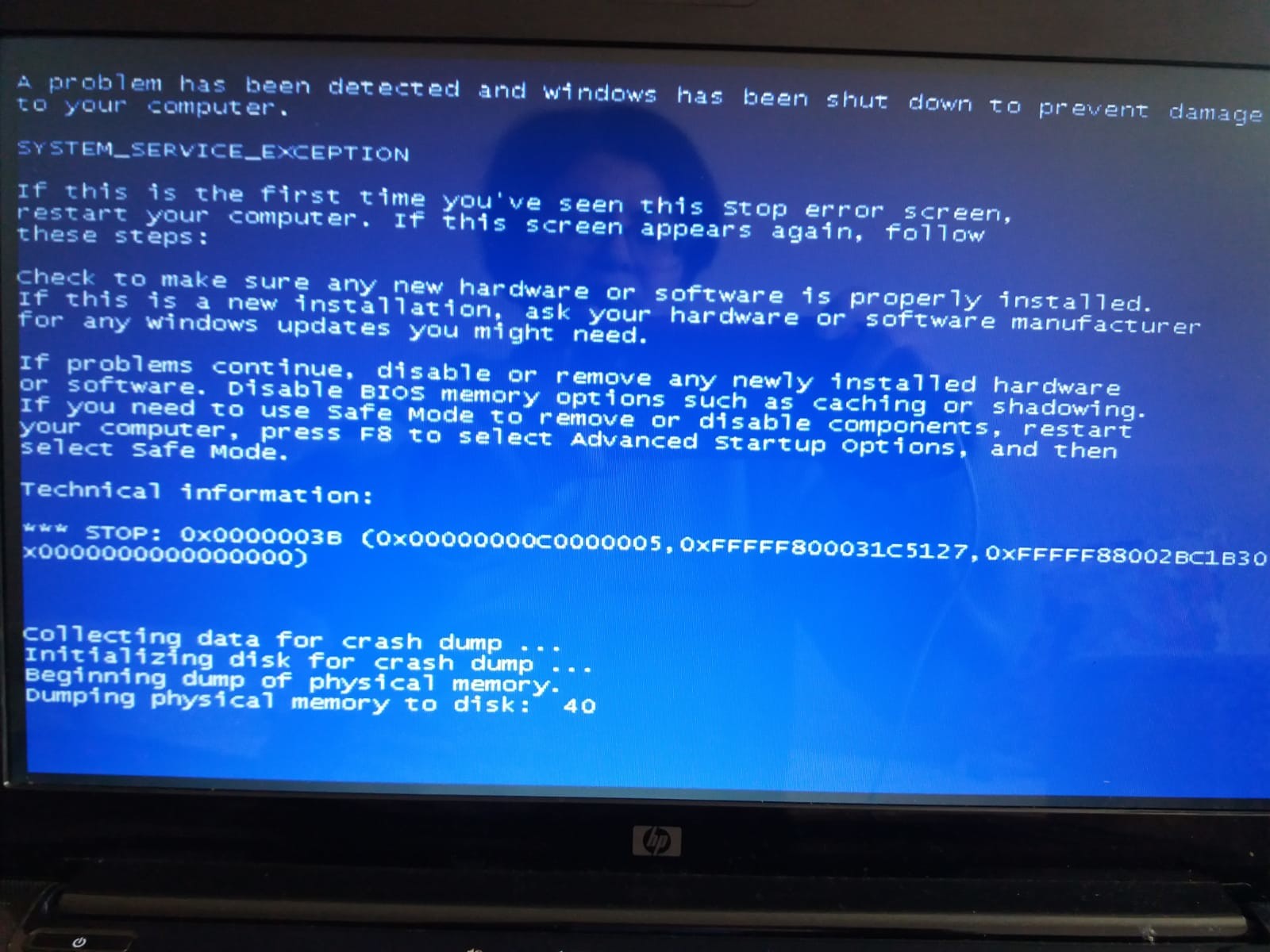
SYSTEM_SERVICE_EXCEPTION (3b)
An exception happened while executing a system service routine.
Arguments:
Arg1: 00000000c0000005, Exception code that caused the bugcheck
Arg2: fffff800030c25f5, Address of the instruction which caused the bugcheck
Arg3: fffff880079300a0, Address of the context record for the exception that caused the bugcheck
Arg4: 0000000000000000, zero.
Debugging Details:
------------------
KEY_VALUES_STRING: 1
PROCESSES_ANALYSIS: 1
SERVICE_ANALYSIS: 1
STACKHASH_ANALYSIS: 1
TIMELINE_ANALYSIS: 1
DUMP_CLASS: 1
DUMP_QUALIFIER: 400
BUILD_VERSION_STRING: 7601.18409.amd64fre.win7sp1_gdr.140303-2144
SYSTEM_MANUFACTURER: Hewlett-Packard
SYSTEM_PRODUCT_NAME: HP Pavilion dv6 Notebook PC
SYSTEM_SKU: VY104EA#AB8
SYSTEM_VERSION: 049D210000241210000020000
BIOS_VENDOR: Hewlett-Packard
BIOS_VERSION: F.1C
BIOS_DATE: 05/17/2010
BASEBOARD_MANUFACTURER: Hewlett-Packard
BASEBOARD_PRODUCT: 3659
BASEBOARD_VERSION: 32.25
DUMP_TYPE: 2
BUGCHECK_P1: c0000005
BUGCHECK_P2: fffff800030c25f5
BUGCHECK_P3: fffff880079300a0
BUGCHECK_P4: 0
EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - <Unable to get error code text>
FAULTING_IP:
nt!KiCommitThreadWait+1d5
fffff800`030c25f5 488bbb90000000 mov rdi,qword ptr [rbx+90h]
CONTEXT: fffff880079300a0 -- (.cxr 0xfffff880079300a0)
rax=000007fffffa8000 rbx=7ffffa800401f750 rcx=fffff88007930a40
rdx=00000000000007ff rsi=fffffa800401f810 rdi=fffff880030f7180
rip=fffff800030c25f5 rsp=fffff88007930a80 rbp=0000000000000000
r8=fffffa80079080e8 r9=0000000000000000 r10=fffffffffffffffe
r11=fffff80003247e00 r12=0000000000000000 r13=0000000000000000
r14=0000000000000001 r15=fffffa800401f858
iopl=0 nv up ei ng nz na po nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00010286
nt!KiCommitThreadWait+0x1d5:
fffff800`030c25f5 488bbb90000000 mov rdi,qword ptr [rbx+90h] ds:002b:7ffffa80`0401f7e0=????????????????
Resetting default scope
BUGCHECK_STR: 0x3B_c0000005
CPU_COUNT: 8
CPU_MHZ: 63c
CPU_VENDOR: GenuineIntel
CPU_FAMILY: 6
CPU_MODEL: 1e
CPU_STEPPING: 5
CPU_MICROCODE: 6,1e,5,0 (F,M,S,R) SIG: 4'00000000 (cache) 3'00000000 (init)
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: WIN7_DRIVER_FAULT
PROCESS_NAME: chrome.exe
CURRENT_IRQL: 2
ANALYSIS_SESSION_HOST: DESKTOP-BKJR0DQ
ANALYSIS_SESSION_TIME: 03-14-2020 21:33:41.0678
ANALYSIS_VERSION: 10.0.18362.1 amd64fre
LAST_CONTROL_TRANSFER: from fffff800030d399f to fffff800030c25f5
STACK_TEXT:
fffff880`07930a80 fffff800`030d399f : 00000000`000002c4 00000000`00000000 fffffa80`00000005 00000000`00000000 : nt!KiCommitThreadWait+0x1d5
fffff880`07930b10 fffff800`033c36fe : fffff880`07930c00 fffffa80`00000006 00000000`00000001 00000000`0a1d8c00 : nt!KeWaitForSingleObject+0x19f
fffff880`07930bb0 fffff800`030cbe53 : fffffa80`0401f750 00000000`00000010 fffff880`07930bf8 fffffa80`040147a0 : nt!NtWaitForSingleObject+0xde
fffff880`07930c20 00000000`778a12fa : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x13
00000000`0a1afb28 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x778a12fa
THREAD_SHA1_HASH_MOD_FUNC: 6ad81c87d6cb15dc35f0e88ffacc5cba6298b080
THREAD_SHA1_HASH_MOD_FUNC_OFFSET: 733eaf96b7974c66e9a0d491641ca86946ff6da0
THREAD_SHA1_HASH_MOD: d084f7dfa548ce4e51810e4fd5914176ebc66791
FOLLOWUP_IP:
nt!KiCommitThreadWait+1d5
fffff800`030c25f5 488bbb90000000 mov rdi,qword ptr [rbx+90h]
FAULT_INSTR_CODE: 90bb8b48
SYMBOL_STACK_INDEX: 0
SYMBOL_NAME: nt!KiCommitThreadWait+1d5
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
DEBUG_FLR_IMAGE_TIMESTAMP: 531590fb
IMAGE_VERSION: 6.1.7601.18409
STACK_COMMAND: .cxr 0xfffff880079300a0 ; kb
FAILURE_BUCKET_ID: X64_0x3B_c0000005_nt!KiCommitThreadWait+1d5
BUCKET_ID: X64_0x3B_c0000005_nt!KiCommitThreadWait+1d5
PRIMARY_PROBLEM_CLASS: X64_0x3B_c0000005_nt!KiCommitThreadWait+1d5
TARGET_TIME: 2020-02-03T15:51:49.000Z
OSBUILD: 7601
OSSERVICEPACK: 1000
SERVICEPACK_NUMBER: 0
OS_REVISION: 0
SUITE_MASK: 272
PRODUCT_TYPE: 1
OSPLATFORM_TYPE: x64
OSNAME: Windows 7
OSEDITION: Windows 7 WinNt (Service Pack 1) TerminalServer SingleUserTS
OS_LOCALE:
USER_LCID: 0
OSBUILD_TIMESTAMP: 2014-03-04 11:38:19
BUILDDATESTAMP_STR: 140303-2144
BUILDLAB_STR: win7sp1_gdr
BUILDOSVER_STR: 6.1.7601.18409.amd64fre.win7sp1_gdr.140303-2144
ANALYSIS_SESSION_ELAPSED_TIME: 45e
ANALYSIS_SOURCE: KM
FAILURE_ID_HASH_STRING: km:x64_0x3b_c0000005_nt!kicommitthreadwait+1d5
FAILURE_ID_HASH: {5478952e-c8a9-47f3-3433-875136cfabbc}
Followup: MachineOwner
---------
REFERENCE_BY_POINTER (18)
Arguments:
Arg1: 0000000000000000, Object type of the object whose reference count is being lowered
Arg2: fffffa80040b9640, Object whose reference count is being lowered
Arg3: 0000000000000002, Reserved
Arg4: ffffffffffffffff, Reserved
The reference count of an object is illegal for the current state of the object.
Each time a driver uses a pointer to an object the driver calls a kernel routine
to increment the reference count of the object. When the driver is done with the
pointer the driver calls another kernel routine to decrement the reference count.
Drivers must match calls to the increment and decrement routines. This bugcheck
can occur because an object's reference count goes to zero while there are still
open handles to the object, in which case the fourth parameter indicates the number
of opened handles. It may also occur when the object's reference count drops below zero
whether or not there are open handles to the object, and in that case the fourth parameter
contains the actual value of the pointer references count.
Debugging Details:
------------------
KEY_VALUES_STRING: 1
PROCESSES_ANALYSIS: 1
SERVICE_ANALYSIS: 1
STACKHASH_ANALYSIS: 1
TIMELINE_ANALYSIS: 1
DUMP_CLASS: 1
DUMP_QUALIFIER: 400
BUILD_VERSION_STRING: 7601.18409.amd64fre.win7sp1_gdr.140303-2144
SYSTEM_MANUFACTURER: Hewlett-Packard
SYSTEM_PRODUCT_NAME: HP Pavilion dv6 Notebook PC
SYSTEM_SKU: VY104EA#AB8
SYSTEM_VERSION: 049D210000241210000020000
BIOS_VENDOR: Hewlett-Packard
BIOS_VERSION: F.1C
BIOS_DATE: 05/17/2010
BASEBOARD_MANUFACTURER: Hewlett-Packard
BASEBOARD_PRODUCT: 3659
BASEBOARD_VERSION: 32.25
DUMP_TYPE: 2
BUGCHECK_P1: 0
BUGCHECK_P2: fffffa80040b9640
BUGCHECK_P3: 2
BUGCHECK_P4: ffffffffffffffff
CPU_COUNT: 8
CPU_MHZ: 63c
CPU_VENDOR: GenuineIntel
CPU_FAMILY: 6
CPU_MODEL: 1e
CPU_STEPPING: 5
CPU_MICROCODE: 6,1e,5,0 (F,M,S,R) SIG: 4'00000000 (cache) 3'00000000 (init)
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: WIN7_DRIVER_FAULT
BUGCHECK_STR: 0x18
PROCESS_NAME: chrome.exe
CURRENT_IRQL: 0
ANALYSIS_SESSION_HOST: DESKTOP-BKJR0DQ
ANALYSIS_SESSION_TIME: 03-14-2020 21:38:01.0560
ANALYSIS_VERSION: 10.0.18362.1 amd64fre
LAST_CONTROL_TRANSFER: from fffff80003069e14 to fffff800030c3bc0
STACK_TEXT:
fffff880`098e3a98 fffff800`03069e14 : 00000000`00000018 00000000`00000000 fffffa80`040b9640 00000000`00000002 : nt!KeBugCheckEx
fffff880`098e3aa0 fffff800`0337ee9f : fffff880`098e3ca0 fffffa80`040b9640 00000000`0a22f960 00000000`00000001 : nt! ?? ::FNODOBFM::`string'+0x48de1
fffff880`098e3b00 fffff800`030c2e53 : fffffa80`07c6a750 00000000`0a22f938 fffff880`098e3bc8 00000000`21c4c000 : nt!NtRemoveIoCompletion+0x14f
fffff880`098e3bb0 00000000`770c134a : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x13
00000000`0a22f918 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x770c134a
THREAD_SHA1_HASH_MOD_FUNC: d482e367d73e858455011b1e0fc9229eb2f14b84
THREAD_SHA1_HASH_MOD_FUNC_OFFSET: a57f0f99ade13dfeccc06b563558edd35d5c66a6
THREAD_SHA1_HASH_MOD: d084f7dfa548ce4e51810e4fd5914176ebc66791
FOLLOWUP_IP:
nt! ?? ::FNODOBFM::`string'+48de1
fffff800`03069e14 cc int 3
FAULT_INSTR_CODE: 1b640cc
SYMBOL_STACK_INDEX: 1
SYMBOL_NAME: nt! ?? ::FNODOBFM::`string'+48de1
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
DEBUG_FLR_IMAGE_TIMESTAMP: 531590fb
IMAGE_VERSION: 6.1.7601.18409
STACK_COMMAND: .thread ; .cxr ; kb
FAILURE_BUCKET_ID: X64_0x18_OVER_DEREFERENCE_nt!_??_::FNODOBFM::_string_+48de1
BUCKET_ID: X64_0x18_OVER_DEREFERENCE_nt!_??_::FNODOBFM::_string_+48de1
PRIMARY_PROBLEM_CLASS: X64_0x18_OVER_DEREFERENCE_nt!_??_::FNODOBFM::_string_+48de1
TARGET_TIME: 2020-01-03T15:31:49.000Z
OSBUILD: 7601
OSSERVICEPACK: 1000
SERVICEPACK_NUMBER: 0
OS_REVISION: 0
SUITE_MASK: 272
PRODUCT_TYPE: 1
OSPLATFORM_TYPE: x64
OSNAME: Windows 7
OSEDITION: Windows 7 WinNt (Service Pack 1) TerminalServer SingleUserTS
OS_LOCALE:
USER_LCID: 0
OSBUILD_TIMESTAMP: 2014-03-04 11:38:19
BUILDDATESTAMP_STR: 140303-2144
BUILDLAB_STR: win7sp1_gdr
BUILDOSVER_STR: 6.1.7601.18409.amd64fre.win7sp1_gdr.140303-2144
ANALYSIS_SESSION_ELAPSED_TIME: 456
ANALYSIS_SOURCE: KM
FAILURE_ID_HASH_STRING: km:x64_0x18_over_dereference_nt!_??_::fnodobfm::_string_+48de1
FAILURE_ID_HASH: {5ba4307c-2f62-b1e1-5172-be3b6254fbd1}
Followup: MachineOwner
---------