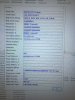
DRIVER_IRQL_NOT_LESS_OR_EQUAL (d1)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If kernel debugger is available get stack backtrace.
Arguments:
Arg1: fffff80f2a3c51be, memory referenced
Arg2: 00000000000000ff, IRQL
Arg3: 0000000000000000, value 0 = read operation, 1 = write operation
Arg4: fffff80f2a3c51be, address which referenced memory
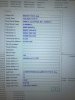
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : Analysis.CPU.Sec
Value: 2
Key : Analysis.DebugAnalysisProvider.CPP
Value: Create: 8007007e on DESKTOP-JC78BRD
Key : Analysis.DebugData
Value: CreateObject
Key : Analysis.DebugModel
Value: CreateObject
Key : Analysis.Elapsed.Sec
Value: 2
Key : Analysis.Memory.CommitPeak.Mb
Value: 69
Key : Analysis.System
Value: CreateObject
ADDITIONAL_XML: 1
BUGCHECK_CODE: d1
BUGCHECK_P1: fffff80f2a3c51be
BUGCHECK_P2: ff
BUGCHECK_P3: 0
BUGCHECK_P4: fffff80f2a3c51be
READ_ADDRESS: fffff8012a7733b8: Unable to get MiVisibleState
Unable to get NonPagedPoolStart
Unable to get NonPagedPoolEnd
Unable to get PagedPoolStart
Unable to get PagedPoolEnd
fffff8012a62a3d8: Unable to get Flags value from nt!KdVersionBlock
fffff8012a62a3d8: Unable to get Flags value from nt!KdVersionBlock
unable to get nt!MmSpecialPagesInUse
fffff80f2a3c51be
ADDITIONAL_DEBUG_TEXT: The trap occurred when interrupts are disabled on the target.
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: System
TRAP_FRAME: ffffc58617a6faa0 -- (.trap 0xffffc58617a6faa0)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=0000000000000003 rbx=0000000000000000 rcx=0000000000000002
rdx=ffff94862509a100 rsi=0000000000000000 rdi=0000000000000000
rip=fffff80f2a3c51be rsp=ffffc58617a6fc38 rbp=0000000000000000
r8=0000000000000008 r9=0000000000000000 r10=0000fffff8013756
r11=ffffc7ff77000000 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up di ng nz na po nc
fffff80f`2a3c51be ?? ???
Resetting default scope
FAILED_INSTRUCTION_ADDRESS:
+0
fffff80f`2a3c51be ?? ???
STACK_TEXT:
ffffc586`17a6f958 fffff801`2a3d41e9 : 00000000`0000000a fffff80f`2a3c51be 00000000`000000ff 00000000`00000000 : nt!KeBugCheckEx
ffffc586`17a6f960 fffff801`2a3d0529 : ffff610d`a454f498 ffffd800`d9323340 ffff9486`2509a010 00000000`00000000 : nt!KiBugCheckDispatch+0x69
ffffc586`17a6faa0 fffff80f`2a3c51be : fffff801`2a3c5e8a 00000000`00000010 00000000`00040286 ffffc586`17a6fc60 : nt!KiPageFault+0x469
ffffc586`17a6fc38 fffff801`2a3c5e8a : 00000000`00000010 00000000`00040286 ffffc586`17a6fc60 00000000`00000018 : 0xfffff80f`2a3c51be
ffffc586`17a6fc40 ffffd800`d9312180 : ffff9486`28d0c080 00000000`000011c0 ffffc586`17a6fc90 00000000`00000000 : nt!KiIdleLoop+0x4a
ffffc586`17a6fc70 ffff9486`28d0c080 : 00000000`000011c0 ffffc586`17a6fc90 00000000`00000000 ffffc586`17a70000 : 0xffffd800`d9312180
ffffc586`17a6fc78 00000000`000011c0 : ffffc586`17a6fc90 00000000`00000000 ffffc586`17a70000 ffffc586`17a6a000 : 0xffff9486`28d0c080
ffffc586`17a6fc80 ffffc586`17a6fc90 : 00000000`00000000 ffffc586`17a70000 ffffc586`17a6a000 00000000`00000000 : 0x11c0
ffffc586`17a6fc88 00000000`00000000 : ffffc586`17a70000 ffffc586`17a6a000 00000000`00000000 00000000`00000000 : 0xffffc586`17a6fc90
SYMBOL_NAME: nt!KiPageFault+469
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
IMAGE_VERSION: 10.0.18362.836
STACK_COMMAND: .thread ; .cxr ; kb
BUCKET_ID_FUNC_OFFSET: 469
FAILURE_BUCKET_ID: DISABLED_INTERRUPT_FAULT_CODE_AV_BAD_IP_nt!KiPageFault
OS_VERSION: 10.0.18362.1
BUILDLAB_STR: 19h1_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {f2ab72c5-099d-9077-bfcf-ba12aa825b36}
Followup: MachineOwner
---------