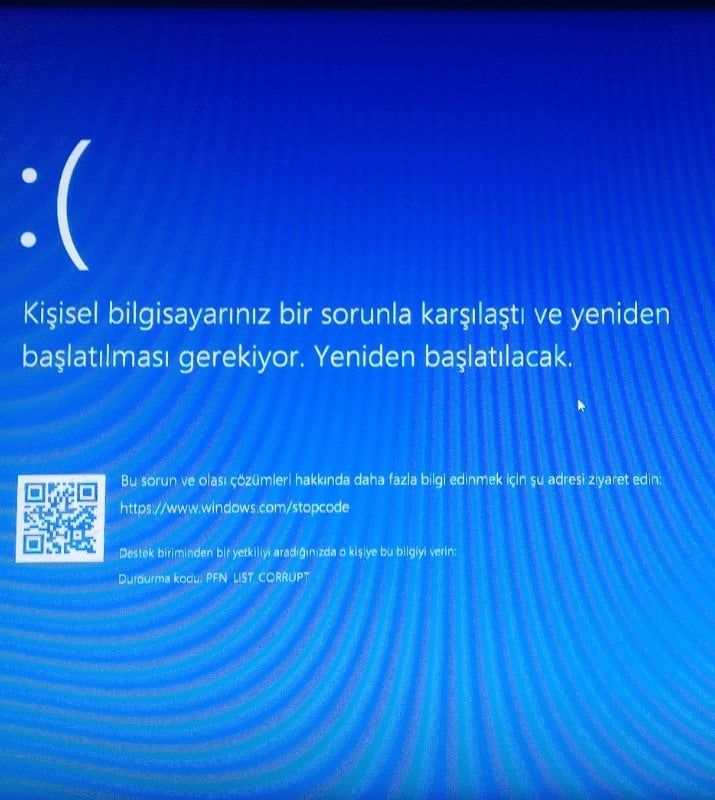
10: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
PFN_LIST_CORRUPT (4e)
Typically caused by drivers passing bad memory descriptor lists (ie: calling
MmUnlockPages twice with the same list, etc). If a kernel debugger is
available get the stack trace.
Arguments:
Arg1: 000000000000009a,
Arg2: 000000000001373f
Arg3: 0000000000000002
Arg4: 0000000000000000
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 2561
Key : Analysis.DebugAnalysisManager
Value: Create
Key : Analysis.Elapsed.mSec
Value: 3432
Key : Analysis.IO.Other.Mb
Value: 0
Key : Analysis.IO.Read.Mb
Value: 0
Key : Analysis.IO.Write.Mb
Value: 0
Key : Analysis.Init.CPU.mSec
Value: 390
Key : Analysis.Init.Elapsed.mSec
Value: 5733
Key : Analysis.Memory.CommitPeak.Mb
Value: 98
Key : Bugcheck.Code.DumpHeader
Value: 0x4e
Key : Bugcheck.Code.Register
Value: 0x4e
Key : Dump.Attributes.AsUlong
Value: 1008
Key : Dump.Attributes.DiagDataWrittenToHeader
Value: 1
Key : Dump.Attributes.ErrorCode
Value: 0
Key : Dump.Attributes.KernelGeneratedTriageDump
Value: 1
Key : Dump.Attributes.LastLine
Value: Dump completed successfully.
Key : Dump.Attributes.ProgressPercentage
Value: 0
FILE_IN_CAB: 043023-14328-01.dmp
DUMP_FILE_ATTRIBUTES: 0x1008
Kernel Generated Triage Dump
BUGCHECK_CODE: 4e
BUGCHECK_P1: 9a
BUGCHECK_P2: 1373f
BUGCHECK_P3: 2
BUGCHECK_P4: 0
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: RGBFusion.exe
STACK_TEXT:
fffffc0f`0e586ed8 fffff804`4da39652 : 00000000`0000004e 00000000`0000009a 00000000`0001373f 00000000`00000002 : nt!KeBugCheckEx
fffffc0f`0e586ee0 fffff804`4d69213b : 00000000`00000000 00000000`00000000 ffff09bb`c43228e0 00000000`00000000 : nt!MiBadRefCount+0x42
fffffc0f`0e586f20 fffff804`4d789f51 : 00000000`00000000 ffff9a00`003a5bd0 ffff9a00`003a5bd0 ffffd180`0002f280 : nt!MiRemoveLockedPageChargeAndDecRef+0x1ab
fffffc0f`0e586f50 fffff804`4d6fa86a : ffff9a00`003a5bd0 fffff804`4d6fe26e ffff9a00`003a5bd0 fffffc0f`00000005 : nt!MiDoubleUnlockMdlPage+0x1d
fffffc0f`0e586f80 fffff804`4d6fd0e5 : ffffa80a`00000001 00000000`00000000 00000000`05e50000 fffffc0f`0e5872b0 : nt!MiDeletePteRun+0xd0a
fffffc0f`0e587180 fffff804`4d6fe7dd : ffffd180`0002f288 00000000`00000000 00000000`00000000 ffffd1e8`c0000178 : nt!MiDeleteVaTail+0x55
fffffc0f`0e5871b0 fffff804`4d657ff2 : 00000000`00000000 fffff804`4d6581bd fffffc0f`0e587578 ffffa80a`877f3080 : nt!MiDeletePagablePteRange+0x53d
fffffc0f`0e5874e0 fffff804`4dac17f8 : 00000000`00000000 00000000`00000001 ffffa80a`87089740 fffffc0f`0e5875b0 : nt!MiDeleteVirtualAddresses+0x52
fffffc0f`0e587530 fffff804`4db2b226 : ffffa80a`870890c0 ffffa80a`89c45c10 ffffa80a`00000000 00000000`00000000 : nt!MiDeleteVad+0x1a8
fffffc0f`0e5875f0 fffff804`4db2ad8d : ffffa80a`8ad2ad00 ffffa80a`8ad2ad00 ffffa80a`8ad2ad00 ffffa80a`870890c0 : nt!MiCleanVad+0x42
fffffc0f`0e587620 fffff804`4dba590d : ffffffff`00000000 ffffffff`ffffffff 00000000`00000001 ffffa80a`870890c0 : nt!MmCleanProcessAddressSpace+0x10d
fffffc0f`0e5876a0 fffff804`4da93c54 : ffffa80a`870890c0 ffffd302`5ed7f930 fffffc0f`0e5878c9 00000000`00000000 : nt!PspRundownSingleProcess+0xc1
fffffc0f`0e587730 fffff804`4dbe6d88 : 00000000`ffffffff 00000000`00000001 ffffa80a`877f30f4 00000000`00dac000 : nt!PspExitThread+0x63c
fffffc0f`0e587830 fffff804`4d60d497 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSchedulerApcTerminate+0x38
fffffc0f`0e587870 fffff804`4d82f540 : 00000000`00000001 fffffc0f`0e587930 00000000`00000000 00000000`00000000 : nt!KiDeliverApc+0x4a7
fffffc0f`0e587930 fffff804`4d83e18f : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00dad498 : nt!KiInitiateUserApc+0x70
fffffc0f`0e587a70 00007fff`9bfdb984 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceExit+0x9f
00000000`1440e538 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x00007fff`9bfdb984
SYMBOL_NAME: nt!MiBadRefCount+42
MODULE_NAME: nt
IMAGE_VERSION: 10.0.22621.1555
STACK_COMMAND: .cxr; .ecxr ; kb
IMAGE_NAME: ntkrnlmp.exe
BUCKET_ID_FUNC_OFFSET: 42
FAILURE_BUCKET_ID: 0x4E_9a_nt!MiBadRefCount
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {4c6c82ad-5a0e-fdfd-2072-9de1e8578958}
Followup: MachineOwner
---------