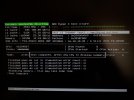
PAGE_FAULT_IN_NONPAGED_AREA (50)
Invalid system memory was referenced. This cannot be protected by try-except.
Typically the address is just plain bad or it is pointing at freed memory.
Arguments:
Arg1: ffffffff8b410d7d, memory referenced.
Arg2: 0000000000000002, value 0 = read operation, 1 = write operation.
Arg3: fffff8073e39bb2e, If non-zero, the instruction address which referenced the bad memory
address.
Arg4: 0000000000000002, (reserved)
Debugging Details:
------------------
Could not read faulting driver name
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 5952
Key : Analysis.DebugAnalysisProvider.CPP
Value: Create: 8007007e on DESKTOP-62N06FT
Key : Analysis.DebugData
Value: CreateObject
Key : Analysis.DebugModel
Value: CreateObject
Key : Analysis.Elapsed.mSec
Value: 17295
Key : Analysis.Memory.CommitPeak.Mb
Value: 79
Key : Analysis.System
Value: CreateObject
Key : WER.OS.Branch
Value: vb_release
Key : WER.OS.Timestamp
Value: 2019-12-06T14:06:00Z
Key : WER.OS.Version
Value: 10.0.19041.1
ADDITIONAL_XML: 1
OS_BUILD_LAYERS: 1
BUGCHECK_CODE: 50
BUGCHECK_P1: ffffffff8b410d7d
BUGCHECK_P2: 2
BUGCHECK_P3: fffff8073e39bb2e
BUGCHECK_P4: 2
READ_ADDRESS: fffff80731efb390: Unable to get MiVisibleState
Unable to get NonPagedPoolStart
Unable to get NonPagedPoolEnd
Unable to get PagedPoolStart
Unable to get PagedPoolEnd
fffff80731e0f340: Unable to get Flags value from nt!KdVersionBlock
fffff80731e0f340: Unable to get Flags value from nt!KdVersionBlock
unable to get nt!MmSpecialPagesInUse
ffffffff8b410d7d
MM_INTERNAL_CODE: 2
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: RuntimeBroker.exe
DEVICE_OBJECT: 0000000000000334
TRAP_FRAME: ffff84811bfb83a0 -- (.trap 0xffff84811bfb83a0)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=ffff84811bfb8598 rbx=0000000000000000 rcx=ffff84811bfb8598
rdx=0000000000000001 rsi=0000000000000000 rdi=0000000000000000
rip=fffff8073e39bb2e rsp=ffff84811bfb8538 rbp=ffff84811bfb85c9
r8=ffffd482d780215c r9=0000000000000034 r10=fffff8072dbdcb80
r11=0000000000000180 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl zr na po nc
bindflt!BfPreDirectoryControl+0x25e:
fffff807`3e39bb2e 1184d2740d418b adc dword ptr [rdx+rdx*8-74BEF28Ch],eax ds:ffffffff`8b410d7d=????????
Resetting default scope
STACK_TEXT:
ffff8481`1bfb80f8 fffff807`3167a665 : 00000000`00000050 ffffffff`8b410d7d 00000000`00000002 ffff8481`1bfb83a0 : nt!KeBugCheckEx
ffff8481`1bfb8100 fffff807`314ea4a0 : 00000000`00000000 00000000`00000002 ffff8481`1bfb8420 00000000`00000000 : nt!MiSystemFault+0x172315
ffff8481`1bfb8200 fffff807`3160335e : 00000000`00000103 00000000`00000000 00000000`00000000 00000000`00000000 : nt!MmAccessFault+0x400
ffff8481`1bfb83a0 fffff807`3e39bb2e : ffff8481`1bfb85c9 ffffbd8e`45ca68a0 ffffbd8e`45ca6800 ffff8481`1bfb85c9 : nt!KiPageFault+0x35e
ffff8481`1bfb8538 ffff8481`1bfb86e9 : fffff807`2dba608b ffffbd8e`45ca6988 ffffbd8e`45ca6988 ffff8481`00000000 : bindflt!BfPreDirectoryControl+0x25e
ffff8481`1bfb8628 fffff807`2dba608b : ffffbd8e`45ca6988 ffffbd8e`45ca6988 ffff8481`00000000 ffffbd8e`46fe0603 : 0xffff8481`1bfb86e9
ffff8481`1bfb8630 fffff807`2dba5b37 : ffff8481`1bfb8800 00000000`0000000c ffffbd8e`47392400 00000000`00000000 : FLTMGR!FltpPerformPreCallbacksWorker+0x36b
ffff8481`1bfb8750 fffff807`2dba4b46 : ffff8481`1bfb9000 ffff8481`1bfb3000 00000000`00000000 ffff8481`1bfb8870 : FLTMGR!FltpPassThroughInternal+0xc7
ffff8481`1bfb87a0 fffff807`2dba48bb : ffffbd8e`44433340 00000000`00000000 00000000`00000020 00000000`00000001 : FLTMGR!FltpPassThrough+0x1d6
ffff8481`1bfb8840 fffff807`314cd6c5 : ffffbd8e`4604eb80 00007fff`ffff0004 ffff8481`1bfb8a00 00000000`00000001 : FLTMGR!FltpDispatch+0x8b
ffff8481`1bfb88a0 fffff807`318c2528 : ffff8481`1bfb89f9 ffffbd8e`4604eb80 00000000`00000001 fffff807`314d9797 : nt!IofCallDriver+0x55
ffff8481`1bfb88e0 fffff807`318ba11f : 00000000`00000334 00000000`00000000 00000000`00000000 ffff8481`1bfb89f9 : nt!IopSynchronousServiceTail+0x1a8
ffff8481`1bfb8980 fffff807`31879d5a : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!NtQueryDirectoryFileEx+0xaf
ffff8481`1bfb8a30 fffff807`31606bb8 : 00000000`00000000 00000069`092fdc30 00000069`092fdce0 00000000`00000074 : nt!NtQueryDirectoryFile+0x7a
ffff8481`1bfb8a90 00007ff8`1774c444 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x28
00000069`092fdc48 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x00007ff8`1774c444
CHKIMG_EXTENSION: !chkimg -lo 50 -d !bindflt
fffff8073e39bb2d - bindflt!BfPreDirectoryControl+25d
[ 75:55 ]
1 error : !bindflt (fffff8073e39bb2d)
MODULE_NAME: memory_corruption
IMAGE_NAME: memory_corruption
MEMORY_CORRUPTOR: ONE_BIT
STACK_COMMAND: .thread ; .cxr ; kb
FAILURE_BUCKET_ID: MEMORY_CORRUPTION_ONE_BIT
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: vb_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {e3faf315-c3d0-81db-819a-6c43d23c63a7}
Followup: memory_corruption
---------