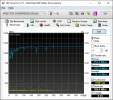
Size de iyi akşamlar Mert Bey. Öncelikle dump dosyalarınızı incelediğimde
MEMORY_MANAGEMENT başlıklı mavi dosyaları ile karşılaştım. RAM'leriniz 3200MHz frekansında çalışıyor ki bu da BIOS'ta XMP modunun açık olduğuna işaret.
Sizden ricam BIOS üzerinden XMP modunu kapatıp Memtest86 testi uygulamanızdır. Ne yazık ki RAM'inizin arızalanmış olması muhtemel. Memtest86 kullanım rehberi aşağıdaki videoda yer alıyor. Ek olarak HD Tune 5.75 indirip sistem disklerinizin Health sekmesini paylaşırsanız sevinirim. Zira sorun sanal bellekte de olabilir.
Sonuçları ve gelişmeleri bizimle paylaşırsanız sevinirim.
[CODE title="Dökümler"]*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
MEMORY_MANAGEMENT (1a)
# Any other values for parameter 1 must be individually examined.
Arguments:
Arg1: 0000000000041792, A corrupt PTE has been detected. Parameter 2 contains the address of
the PTE. Parameters 3/4 contain the low/high parts of the PTE.
Arg2: ffffea012236b720
Arg3: 0010000000000000
Arg4: 0000000000000000
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 5249
Key : Analysis.DebugAnalysisManager
Value: Create
Key : Analysis.Elapsed.mSec
Value: 6030
Key : Analysis.Init.CPU.mSec
Value: 1062
Key : Analysis.Init.Elapsed.mSec
Value: 3661
Key : Analysis.Memory.CommitPeak.Mb
Value: 71
Key : MemoryManagement.PFN
Value: 0
Key : WER.OS.Branch
Value: vb_release
Key : WER.OS.Timestamp
Value: 2019-12-06T14:06:00Z
Key : WER.OS.Version
Value: 10.0.19041.1
BUGCHECK_CODE: 1a
BUGCHECK_P1: 41792
BUGCHECK_P2: ffffea012236b720
BUGCHECK_P3: 10000000000000
BUGCHECK_P4: 0
MEMORY_CORRUPTOR: ONE_BIT
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: dwm.exe
STACK_TEXT:
ffff8385`f41bd128 fffff804`68c9d0fa : 00000000`0000001a 00000000`00041792 ffffea01`2236b720 00100000`00000000 : nt!KeBugCheckEx
ffff8385`f41bd130 fffff804`68c0b9e6 : 00000000`00000000 ffff8385`f41bd700 00000000`000005f8 ffffea01`2236b720 : nt!MiDeleteVa+0x153a
ffff8385`f41bd230 fffff804`68c0bafb : ffffea75`00000000 ffffda0f`f0f6f700 ffff8385`00000000 ffff8385`f41bd6a0 : nt!MiWalkPageTablesRecursively+0x776
ffff8385`f41bd2d0 fffff804`68c0bafb : ffffea75`3a804888 ffffda0f`f0f6f700 ffff8385`00000001 ffff8385`f41bd6b0 : nt!MiWalkPageTablesRecursively+0x88b
ffff8385`f41bd370 fffff804`68c0bafb : ffffea75`3a804000 ffffda0f`f0f6f700 ffff8385`00000002 ffff8385`f41bd6c0 : nt!MiWalkPageTablesRecursively+0x88b
ffff8385`f41bd410 fffff804`68c5de6b : 000f8067`00000000 ffffda0f`f0f6f700 00000000`00000003 ffff8385`f41bd6d0 : nt!MiWalkPageTablesRecursively+0x88b
ffff8385`f41bd4b0 fffff804`68c9b991 : ffff8385`f41bd650 ffffda0f`00000000 00000000`00000002 ffffda0f`00000000 : nt!MiWalkPageTables+0x36b
ffff8385`f41bd5b0 fffff804`68c6baf0 : 00000000`00000001 ffff8385`00000000 ffffda0f`f0f6f550 ffffda0f`e42d1080 : nt!MiDeletePagablePteRange+0x4f1
ffff8385`f41bd8c0 fffff804`69036189 : ffffda0f`f067b7c0 00000000`00000000 ffffda0f`00000000 ffffda0f`00000000 : nt!MiDeleteVad+0x360
ffff8385`f41bd9d0 fffff804`69035820 : ffffda0f`f067b7c0 ffffda0f`f1d29b20 ffffda0f`e42d1080 00000000`00000000 : nt!MiUnmapVad+0x49
ffff8385`f41bda00 fffff804`69033aef : ffffda0f`e638e0e0 ffffda0f`e638e0e0 ffffda0f`f067b7c0 ffffda0f`f0f6f080 : nt!MiCleanVad+0x30
ffff8385`f41bda30 fffff804`6905dbd4 : ffffffff`00000000 ffffffff`ffffffff 00000000`00000001 ffffda0f`f0f6f080 : nt!MmCleanProcessAddressSpace+0x137
ffff8385`f41bdab0 fffff804`69306b92 : fffff804`69725440 ffffda0f`f0f6f080 fffff804`69306b60 00000000`00000200 : nt!PspRundownSingleProcess+0x20c
ffff8385`f41bdb40 fffff804`68c25975 : ffffda0f`e42d1080 fffff804`68d2a580 ffffda0f`e16a6860 ffffda0f`00000000 : nt!PspProcessRundownWorkerSingle+0x32
ffff8385`f41bdb70 fffff804`68d17e85 : ffffda0f`e42d1080 00000000`00000080 ffffda0f`e16a5040 000f8067`b4bbbdff : nt!ExpWorkerThread+0x105
ffff8385`f41bdc10 fffff804`68dfd498 : fffff804`65f46180 ffffda0f`e42d1080 fffff804`68d17e30 00000000`00000000 : nt!PspSystemThreadStartup+0x55
ffff8385`f41bdc60 00000000`00000000 : ffff8385`f41be000 ffff8385`f41b8000 00000000`00000000 00000000`00000000 : nt!KiStartSystemThread+0x28
MODULE_NAME: hardware
IMAGE_NAME: memory_corruption
STACK_COMMAND: .thread ; .cxr ; kb
FAILURE_BUCKET_ID: MEMORY_CORRUPTION_ONE_BIT
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: vb_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {e3faf315-c3d0-81db-819a-6c43d23c63a7}
Followup: MachineOwner
---------
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
SYSTEM_THREAD_EXCEPTION_NOT_HANDLED_M (1000007e)
This is a very common BugCheck. Usually the exception address pinpoints
the driver/function that caused the problem. Always note this address
as well as the link date of the driver/image that contains this address.
Some common problems are exception code 0x80000003. This means a hard
coded breakpoint or assertion was hit, but this system was booted
/NODEBUG. This is not supposed to happen as developers should never have
hardcoded breakpoints in retail code, but ...
If this happens, make sure a debugger gets connected, and the
system is booted /DEBUG. This will let us see why this breakpoint is
happening.
Arguments:
Arg1: ffffffffc0000005, The exception code that was not handled
Arg2: fffff8034b6e54d0, The address that the exception occurred at
Arg3: ffffab073deb52b8, Exception Record Address
Arg4: ffffab073deb4af0, Context Record Address
Debugging Details:
------------------
*** WARNING: Unable to verify timestamp for win32k.sys
KEY_VALUES_STRING: 1
Key : AV.Fault
Value: Read
Key : Analysis.CPU.mSec
Value: 8796
Key : Analysis.DebugAnalysisManager
Value: Create
Key : Analysis.Elapsed.mSec
Value: 24303
Key : Analysis.Init.CPU.mSec
Value: 890
Key : Analysis.Init.Elapsed.mSec
Value: 3427
Key : Analysis.Memory.CommitPeak.Mb
Value: 84
Key : WER.OS.Branch
Value: vb_release
Key : WER.OS.Timestamp
Value: 2019-12-06T14:06:00Z
Key : WER.OS.Version
Value: 10.0.19041.1
BUGCHECK_CODE: 7e
BUGCHECK_P1: ffffffffc0000005
BUGCHECK_P2: fffff8034b6e54d0
BUGCHECK_P3: ffffab073deb52b8
BUGCHECK_P4: ffffab073deb4af0
EXCEPTION_RECORD: ffffab073deb52b8 -- (.exr 0xffffab073deb52b8)
ExceptionAddress: fffff8034b6e54d0 (Ntfs!NtfsFsdClose+0x0000000000000100)
ExceptionCode: c0000005 (Access violation)
ExceptionFlags: 00000000
NumberParameters: 2
Parameter[0]: 0000000000000000
Parameter[1]: ffffffffffffffff
Attempt to read from address ffffffffffffffff
CONTEXT: ffffab073deb4af0 -- (.cxr 0xffffab073deb4af0)
rax=0000000000000000 rbx=ffff800e232292e0 rcx=ffff800e1489c180
rdx=ffff800e1432b210 rsi=ffffc407b8065740 rdi=ffefc407b80655e0
rip=fffff8034b6e54d0 rsp=ffffab073deb54f0 rbp=0000000000000000
r8=0000000000000002 r9=ffff800e1489c030 r10=fffff8034665ed60
r11=ffffab073deb5628 r12=ffff800e14721201 r13=0000000000000000
r14=0000000000000000 r15=ffff800e1fb4ba60
iopl=0 nv up ei ng nz na pe nc
cs=0010 ss=0000 ds=002b es=002b fs=0053 gs=002b efl=00050282
Ntfs!NtfsFsdClose+0x100:
fffff803`4b6e54d0 488b4f68 mov rcx,qword ptr [rdi+68h] ds:002b:ffefc407`b8065648=????????????????
Resetting default scope
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: System
READ_ADDRESS: fffff803470fb390: Unable to get MiVisibleState
Unable to get NonPagedPoolStart
Unable to get NonPagedPoolEnd
Unable to get PagedPoolStart
Unable to get PagedPoolEnd
unable to get nt!MmSpecialPagesInUse
ffffffffffffffff
ERROR_CODE: (NTSTATUS) 0xc0000005 - 0x%p adresindeki y nerge 0x%p adresindeki belle e ba vurdu. Bellek u olamaz %s.
EXCEPTION_CODE_STR: c0000005
EXCEPTION_PARAMETER1: 0000000000000000
EXCEPTION_PARAMETER2: ffffffffffffffff
EXCEPTION_STR: 0xc0000005
STACK_TEXT:
ffffab07`3deb54f0 fffff803`46652f55 : ffffab07`3deb5701 ffff800e`1fb4ba60 ffffab07`3deb6000 ffffab07`00000002 : Ntfs!NtfsFsdClose+0x100
ffffab07`3deb5630 fffff803`452a6ccf : 00000000`74536d4d ffffc407`a5f59650 00000000`00000000 ffffc407`9b000100 : nt!IofCallDriver+0x55
ffffab07`3deb5670 fffff803`452a48d3 : ffffab07`3deb5700 00000000`00000000 00000000`00000000 ffff800e`141b4b40 : FLTMGR!FltpLegacyProcessingAfterPreCallbacksCompleted+0x28f
ffffab07`3deb56e0 fffff803`46652f55 : ffff800e`232292e0 fffff803`46655758 ffff800e`148742d0 ffff800e`00000000 : FLTMGR!FltpDispatch+0xa3
ffffab07`3deb5740 fffff803`46a00f9a : ffff800e`232292e0 ffffc407`b8054bd0 ffff800e`14889ce0 ffff800e`14889ce0 : nt!IofCallDriver+0x55
ffffab07`3deb5780 fffff803`469fb300 : ffffc407`b8054bd0 00000000`00000000 ffff800e`116f9380 fffff803`46db1019 : nt!IopDeleteFile+0x13a
ffffab07`3deb5800 fffff803`46661277 : 00000000`00000000 00000000`00000000 ffffc407`b8054bd0 ffff800e`232292e0 : nt!ObpRemoveObjectRoutine+0x80
ffffab07`3deb5860 fffff803`4666119e : 00000000`00000000 ffff800e`2316f3d0 ffff800e`2316f3d0 ffff800e`2316f3d0 : nt!ObfDereferenceObjectWithTag+0xc7
ffffab07`3deb58a0 fffff803`46a3e459 : 00000000`00088081 ffff800e`2316f3d0 fffff803`47050c80 00000000`00088081 : nt!HalPutDmaAdapter+0xe
ffffab07`3deb58d0 fffff803`467843bd : 00000000`00000001 00000000`00000000 ffffab07`3deb59a0 ffff800e`2316f3d8 : nt!MiSegmentDelete+0x155
ffffab07`3deb5920 fffff803`467b9259 : 00000000`00000000 fffff803`00000001 00000000`00000000 00000000`00000000 : nt!MiProcessDereferenceList+0xc1
ffffab07`3deb59e0 fffff803`46717e85 : ffff800e`148b6580 ffff800e`148b6580 00000000`00000080 fffff803`467b9130 : nt!MiDereferenceSegmentThread+0x129
ffffab07`3deb5c10 fffff803`467fd498 : ffff9981`b5f5d180 ffff800e`148b6580 fffff803`46717e30 00000000`00000000 : nt!PspSystemThreadStartup+0x55
ffffab07`3deb5c60 00000000`00000000 : ffffab07`3deb6000 ffffab07`3deb0000 00000000`00000000 00000000`00000000 : nt!KiStartSystemThread+0x28
SYMBOL_NAME: Ntfs!NtfsFsdClose+100
MODULE_NAME: Ntfs
IMAGE_NAME: Ntfs.sys
IMAGE_VERSION: 10.0.19041.928
STACK_COMMAND: .cxr 0xffffab073deb4af0 ; kb
BUCKET_ID_FUNC_OFFSET: 100
FAILURE_BUCKET_ID: AV_Ntfs!NtfsFsdClose
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: vb_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {42498c29-613b-7b4c-da04-cbf50aed7e53}
Followup: MachineOwner
---------
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
MEMORY_MANAGEMENT (1a)
# Any other values for parameter 1 must be individually examined.
Arguments:
Arg1: 0000000000041792, A corrupt PTE has been detected. Parameter 2 contains the address of
the PTE. Parameters 3/4 contain the low/high parts of the PTE.
Arg2: fffffc8139417720
Arg3: 0042000000000000
Arg4: 0000000000000000
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 10702
Key : Analysis.DebugAnalysisManager
Value: Create
Key : Analysis.Elapsed.mSec
Value: 20811
Key : Analysis.Init.CPU.mSec
Value: 1015
Key : Analysis.Init.Elapsed.mSec
Value: 3820
Key : Analysis.Memory.CommitPeak.Mb
Value: 86
Key : MemoryManagement.PFN
Value: 0
Key : WER.OS.Branch
Value: vb_release
Key : WER.OS.Timestamp
Value: 2019-12-06T14:06:00Z
Key : WER.OS.Version
Value: 10.0.19041.1
BUGCHECK_CODE: 1a
BUGCHECK_P1: 41792
BUGCHECK_P2: fffffc8139417720
BUGCHECK_P3: 42000000000000
BUGCHECK_P4: 0
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: browser.exe
STACK_TEXT:
ffffeb80`9215c2a8 fffff803`2549d0fa : 00000000`0000001a 00000000`00041792 fffffc81`39417720 00420000`00000000 : nt!KeBugCheckEx
ffffeb80`9215c2b0 fffff803`2540b9e6 : 00000000`00000000 00000000`00000000 00000000`00000033 fffffc81`39417720 : nt!MiDeleteVa+0x153a
ffffeb80`9215c3b0 fffff803`2540bafb : fffffcfe`409ca0b8 ffffd605`799bd980 ffffeb80`00000000 ffffeb80`9215c820 : nt!MiWalkPageTablesRecursively+0x776
ffffeb80`9215c450 fffff803`2540bafb : fffffcfe`00000000 ffffd605`799bd980 ffffeb80`00000001 ffffeb80`9215c830 : nt!MiWalkPageTablesRecursively+0x88b
ffffeb80`9215c4f0 fffff803`2540bafb : fffffcfe`7f204000 ffffd605`799bd980 ffffeb80`00000002 ffffeb80`9215c840 : nt!MiWalkPageTablesRecursively+0x88b
ffffeb80`9215c590 fffff803`2545de6b : ffffeb80`9215c600 ffffd605`799bd980 00000000`00000003 ffffeb80`9215c850 : nt!MiWalkPageTablesRecursively+0x88b
ffffeb80`9215c630 fffff803`2549b991 : ffffeb80`9215c7d0 ffffd605`00000000 00000000`00000002 fffff803`00000000 : nt!MiWalkPageTables+0x36b
ffffeb80`9215c730 fffff803`2546baf0 : 00000000`00000001 ffffeb80`00000000 ffffd605`799bd7d0 ffffd605`773b3080 : nt!MiDeletePagablePteRange+0x4f1
ffffeb80`9215ca40 fffff803`25836189 : ffff8109`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!MiDeleteVad+0x360
ffffeb80`9215cb50 fffff803`25835f62 : ffffd605`7aa30d40 00000000`00000000 ffffd605`799bd300 00000000`00000000 : nt!MiUnmapVad+0x49
ffffeb80`9215cb80 fffff803`258d951f : ffffd605`756ff9d0 00000000`00000004 00000000`00000001 ffffd605`799bd300 : nt!MiUnmapViewOfSection+0x152
ffffeb80`9215cc60 fffff528`e9542bda : ffffd605`799bd300 00000000`00000181 ffffeb80`9215d040 ffffd605`756ff9d0 : nt!MmUnmapViewOfSection+0xf
ffffeb80`9215cc90 fffff528`e95421e8 : ffffeb80`9215d040 ffffeb80`9215ce70 ffffeb80`9215d040 ffffb57c`34600000 : win32kfull!FreeView+0xa2
ffffeb80`9215cd10 fffff528`e925de48 : 00000000`00000001 00000000`0000000a 00000000`c000001c fffff803`255f9ca0 : win32kfull!UnmapDesktop+0x98
ffffeb80`9215cd70 fffff528`e9c510d0 : 00000000`c000001c fffff803`25461104 00000000`00000000 ffffeb80`9215d040 : win32kbase!W32CalloutDispatch+0x488
ffffeb80`9215cf80 fffff803`25837849 : ffffeb80`9215d040 00000000`0000000a fffff803`25e1df80 ffff8109`e452a8c0 : win32k!W32CalloutDispatchThunk+0x30
ffffeb80`9215cfc0 fffff803`25837bcd : 00000000`0000000a ffffeb80`9215d060 00000000`00000000 ffff8109`f38206f0 : nt!ExCallCallBack+0x3d
ffffeb80`9215cff0 fffff803`258d1bcf : ffffd605`6a8c6c40 ffffeb80`9215d060 ffffd605`00000000 00000000`00000000 : nt!PsInvokeWin32Callout+0xbd
ffffeb80`9215d020 fffff803`25828d1c : 00000000`00000001 ffffd605`00000000 ffffffff`00000000 ffffffff`ffffffff : nt!ExpWin32CloseProcedure+0x9f
ffffeb80`9215d070 fffff803`2583761b : ffff8109`ed0351c0 00000000`00000000 00000000`00000000 00000000`00004000 : nt!ObCloseHandleTableEntry+0x24c
ffffeb80`9215d1b0 fffff803`2583757b : 00000000`00000200 00000000`00000000 00000000`00000000 ffffb57c`34600000 : nt!ObpCloseHandle+0x8b
ffffeb80`9215d220 fffff528`e921947f : 00000000`00000200 00000000`c00000bb fffff559`82c05ab0 00000000`00000000 : nt!ObCloseHandle+0x2b
ffffeb80`9215d250 fffff528`e926b947 : fffff528`e94563f8 00000000`00000000 00000000`c00000bb fffff559`82c05ab0 : win32kbase!CloseProtectedHandle+0x2b
ffffeb80`9215d280 fffff528`e9266fe0 : 00000000`00000000 00000000`00000000 ffffeb80`9215d3e0 ffffd605`773b3080 : win32kbase!DestroyProcessInfo+0x327
ffffeb80`9215d2e0 fffff528`e95089f5 : fffff803`25461420 fffff528`e95c6d61 fffff559`82c05ab0 7fffd605`763c8f40 : win32kbase!xxxUserProcessCallout+0x470
ffffeb80`9215d510 fffff528`e925de48 : 00000000`00000000 00000000`c000001c ffffeb80`9215d878 fffff803`25460c8b : win32kfull!W32pProcessCallout+0xe5
ffffeb80`9215d550 fffff528`e9c510d0 : 00000000`c000001c ffffeb80`9215d810 00000000`00000000 ffffeb80`9215d878 : win32kbase!W32CalloutDispatch+0x488
ffffeb80`9215d760 fffff803`25837b65 : 00000000`00000000 fffff803`25e1df80 ffffd605`759fe260 00000000`00000000 : win32k!W32CalloutDispatchThunk+0x30
ffffeb80`9215d7a0 fffff803`25906a38 : ffffd605`763c8de0 ffffeb80`9215d990 ffffeb80`00000000 00000000`00000000 : nt!PsInvokeWin32Callout+0x55
ffffeb80`9215d7d0 fffff803`258d2918 : ffffd605`00000000 00000000`00000001 ffffeb80`9215d9e0 ffffd605`78561080 : nt!PspExitThread+0x598
ffffeb80`9215d8d0 fffff803`25467fb7 : 00000000`40eb0088 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSchedulerApcTerminate+0x38
ffffeb80`9215d910 fffff803`255fa3e0 : 00000097`055ffb38 ffffeb80`9215d9c0 ffffeb80`9215db80 7fffffff`00000000 : nt!KiDeliverApc+0x487
ffffeb80`9215d9c0 fffff803`2560785f : ffffd605`773b3080 00000000`00000000 ffffeb80`9215db18 ffffffff`ec549980 : nt!KiInitiateUserApc+0x70
ffffeb80`9215db00 00007ffe`a948cda4 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceExit+0x9f
00000097`055ffb08 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x00007ffe`a948cda4
SYMBOL_NAME: win32kfull!FreeView+a2
MODULE_NAME: win32kfull
IMAGE_NAME: win32kfull.sys
IMAGE_VERSION: 10.0.19041.906
STACK_COMMAND: .thread ; .cxr ; kb
BUCKET_ID_FUNC_OFFSET: a2
FAILURE_BUCKET_ID: 0x1a_41792_win32kfull!FreeView
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: vb_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {39760622-2871-baa8-4d78-5e5e7368a84c}
Followup: MachineOwner
---------[/CODE]