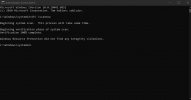
Microsoft (R) Windows Debugger Version 10.0.20153.1000 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Users\maksu\Desktop\Yeni klasör (2)\121120-11890-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
************* Path validation summary **************
Response Time (ms) Location
Deferred srv*
Symbol search path is: srv*
Executable search path is:
Windows 10 Kernel Version 19041 MP (12 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Edition build lab: 19041.1.amd64fre.vb_release.191206-1406
Machine Name:
Kernel base = 0xfffff807`23000000 PsLoadedModuleList = 0xfffff807`23c2a2b0
Debug session time: Fri Dec 11 17:46:03.500 2020 (UTC + 3:00)
System Uptime: 1 days 1:11:13.135
Loading Kernel Symbols
...............................................................
................................................................
............................................................
Loading User Symbols
Loading unloaded module list
.......................
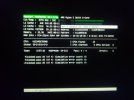
For analysis of this file, run !analyze -v
nt!KeBugCheckEx:
fffff807`233f5780 48894c2408 mov qword ptr [rsp+8],rcx ss:0018:ffff8b81`f0706020=000000000000003b
7: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
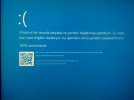
SYSTEM_SERVICE_EXCEPTION (3b)
An exception happened while executing a system service routine.
Arguments:
Arg1: 00000000c0000005, Exception code that caused the bugcheck
Arg2: fffff8072324ee2a, Address of the instruction which caused the bugcheck
Arg3: ffff8b81f0706920, Address of the context record for the exception that caused the bugcheck
Arg4: 0000000000000000, zero.
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 6968
Key : Analysis.DebugAnalysisProvider.CPP
Value: Create: 8007007e on DESKTOP-G2EFLS9
Key : Analysis.DebugData
Value: CreateObject
Key : Analysis.DebugModel
Value: CreateObject
Key : Analysis.Elapsed.mSec
Value: 15660
Key : Analysis.Memory.CommitPeak.Mb
Value: 74
Key : Analysis.System
Value: CreateObject
Key : WER.OS.Branch
Value: vb_release
Key : WER.OS.Timestamp
Value: 2019-12-06T14:06:00Z
Key : WER.OS.Version
Value: 10.0.19041.1
ADDITIONAL_XML: 1
OS_BUILD_LAYERS: 1
BUGCHECK_CODE: 3b
BUGCHECK_P1: c0000005
BUGCHECK_P2: fffff8072324ee2a
BUGCHECK_P3: ffff8b81f0706920
BUGCHECK_P4: 0
CONTEXT: ffff8b81f0706920 -- (.cxr 0xffff8b81f0706920)
rax=0000000000000001 rbx=ffffcb01e8010290 rcx=0400000000000000
rdx=ffffcb01f668bcd8 rsi=0000000000000001 rdi=ffffcb01f668bcd8
rip=fffff8072324ee2a rsp=ffff86093e4595c8 rbp=000000000000002d
r8=0000000000000001 r9=0400000000000000 r10=0000000000000000
r11=ffffcb01f3e31798 r12=ffffcb01f6684030 r13=ffffcb01f6684000
r14=0000000000000000 r15=ffffcb01f668bcd0
iopl=0 nv up ei pl nz na po nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00050206
nt!RtlRbRemoveNode+0x35a:
fffff807`2324ee2a 498b4110 mov rax,qword ptr [r9+10h] ds:002b:04000000`00000010=????????????????
Resetting default scope
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: opera.exe
BAD_PAGES_DETECTED: c
IRP_ADDRESS: ffffcb01f2d53088
BAD_STACK_POINTER: ffff8b81f0706018
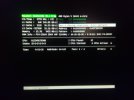
STACK_TEXT:
ffff8609`3e4595c8 fffff807`2324e963 : 00000000`0000002d ffffcb01`f668ba00 00000000`00000000 ffffcb01`f668bcd0 : nt!RtlRbRemoveNode+0x35a
ffff8609`3e4595e0 fffff807`2324e2d8 : ffffcb01`e8010280 ffffcb01`f6684000 ffffcb01`e8010280 ffff8609`3e4596e8 : nt!RtlpHpVsChunkCoalesce+0x183
ffff8609`3e459640 fffff807`2324cc64 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!RtlpHpVsContextFree+0x188
ffff8609`3e4596e0 fffff807`239b1019 : 00000000`00000270 ffffcb01`f658b3b0 ffffcb01`f2f161c0 01000000`00100000 : nt!ExFreeHeapPool+0x4d4
ffff8609`3e4597c0 fffff807`2324984e : 00000000`00000002 00000031`4efdeb9b ffffcb01`f2f16080 fffff807`232686b3 : nt!ExFreePool+0x9
ffff8609`3e4597f0 fffff807`232683e3 : ffffcb01`f2d53100 00000000`00000001 ffffcb01`f6076ab0 ffffcb01`f6076aa0 : nt!IopCompleteRequest+0x8e
ffff8609`3e4598b0 fffff807`236b791d : 00000000`00000000 00000000`00000000 ffffcb01`fa1638a0 00000000`00000000 : nt!IoRemoveIoCompletion+0x393
ffff8609`3e4599e0 fffff807`234071b8 : ffffcb01`f2f16080 00000099`c89ffae8 ffff8609`3e459aa8 00000204`9f4bb430 : nt!NtRemoveIoCompletion+0x13d
ffff8609`3e459a90 00007ffd`1550c0d4 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x28
00000099`c89ffac8 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x00007ffd`1550c0d4
SYMBOL_NAME: PAGE_NOT_ZERO
MODULE_NAME: Unknown_Module
IMAGE_NAME: Unknown_Image
STACK_COMMAND: .cxr 0xffff8b81f0706920 ; kb
FAILURE_BUCKET_ID: PAGE_NOT_ZERO_0x3B_c0000005
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: vb_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {e53488a4-f53d-5828-4e8b-03e3e9cba4c2}
Followup: MachineOwner
---------
*** Memory manager detected 12 instance(s) of page corruption, target is likely to have memory corruption.